WatchGuard XTM 26-W review
Despite modest dimensions the WatchGuard’s XTM 26-W appliance provides enterprise level security measures at a price SMBs can afford.
The XTM 26-W can be tricky to configure but it delivers a range of features at an affordable price for SMBs. Its security policies are versatile and WatchGuard’s application awareness can strictly control social networking in the workplace.

Proxy setup
You need to create a proxy action which defines functions such as exceptions, cache usage, user override passwords, alarms and logging requests and then link it to the profile. You can then create a firewall rule. This defines which interfaces the profile is to be applied to.
The same process is used by the POP3 proxy for the Commtouch hosted anti-spam service and in all cases you can apply IPS and gateway anti-virus to selected firewall rules. It takes a bit of practice but the proxies do provide a powerful and versatile set of security measures.
There's more as WatchGuard's application awareness controls specific apps such as Facebook. It can be linked with AD authentication so you can fine-tune social networking access on a per user basis and decide who can login, edit their profile, access web mail, use video, transfer files, play games or chat.
For wireless operations you can use either 2.4GHz b/g/n or 5GHz a/n and the appliance can present up to three SSIDs. The predefined guest SSID bridges with the WAN port for secure Internet access and can present a custom login portal with an AUP.
The appliance's web interface is well designed and provides plenty of performance graphs
The other two SSIDs can bridge with any of the five Gigabit ports but the rogue AP detection is of limited value as it disables all SSIDs when it's running. However, we found it worked well during testing and you can use a scheduler to run it outside working hours.
Reporting features
For full reporting you'll need to run the WatchGuard logging and reporting servers on a separate Windows host. They have a light footprint and we found they ran happily in the background on a basic Windows 7 PC. New reporting features include HIPAA and PCI compliancy reports plus audit trails.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
WatchGuard includes its System Manager utilities for remotely managing multiple appliances. A new feature is the option to schedule feature key synchronisations, reboots and OS upgrades across groups of appliances.
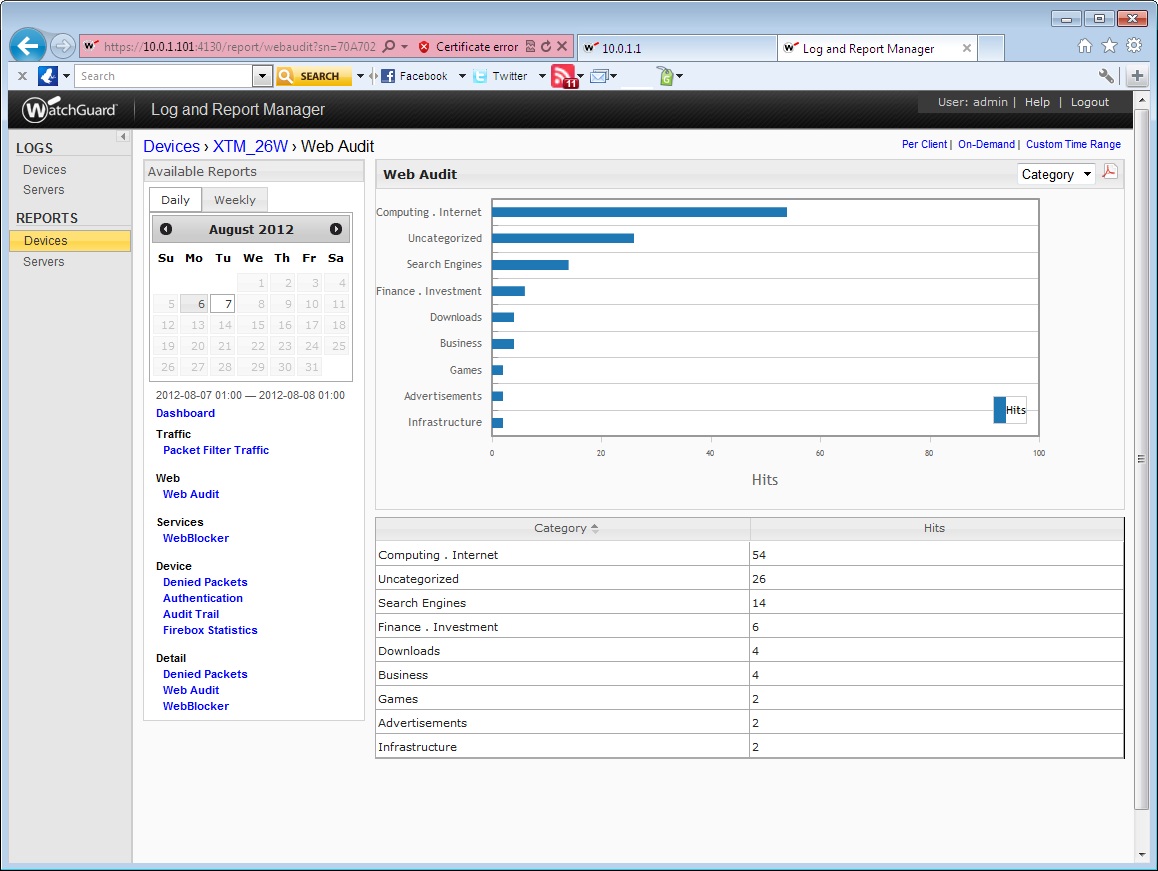
The new Log and Report Manager provides more detailed information about network activity than previous versions
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 The open source ecosystem is booming thanks to AI, but hackers are taking advantage
The open source ecosystem is booming thanks to AI, but hackers are taking advantageNews Analysis by Sonatype found that AI is giving attackers new opportunities to target victims
By Emma Woollacott Published
-
 Westcon-Comstor enters Balkan market with REAL Security acquisition
Westcon-Comstor enters Balkan market with REAL Security acquisitionNews The acquisition gives the distribution giant immediate access to an established partner ecosystem spanning eight Balkan markets
By Daniel Todd Published
-
 Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsers
Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsersNews Defenders advised to use runtime behavioral analysis to detect and block malicious activity at the point of execution, directly within the browser
By Emma Woollacott Published
