Roxio Secure Burn Plus review
Roxio Secure Burn Plus could help you avoid the public embarrassment of losing optical discs containing sensitive data, so should you heed that burning sensation and rush out and buy it? Read our review first.
Roxio Secure Burn is easy to administer and use and it's cheap too. It'll have to be used in conjunction with other security tools to prevent other forms of data leakage though, so you might as well invest in an integrated security package such as DeviceLock instead, especially if you're managing lots of users.
Even the most diligent, security-conscious firms will inevitably fall victim to human error and lose discs containing sensitive data. Roxio's Secure Burn Plus aims to prevent the most serious security consequences of such a loss strangers getting ahold of the important information on those discs. Secure Burn Plus encrypts and password protects optical discs such as CDs and DVDs so any private information should remain private, even if the disc is lost or stolen.
Secure Burn Plus is a complete disc writing program in its own right and is used in place of whatever disc burning software you currently use. IT administrators configure Secure Burn Plus by installing a Permissions Manager on each computer. Permissions Manager is then used to create user names and passwords. Those user accounts can be organised into groups which not only makes administration easier, but also allows finer grained control over security certain groups can be allowed to access discs burnt by other groups, but not vice-versa, for example. Permissions can also be set so that users don't need to input their password when viewing discs created by a colleague in their group.
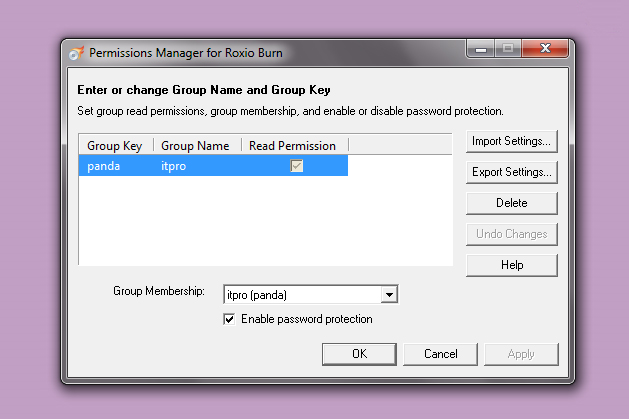
The Permissions Manager is where you set user account details and security policies
Once you've finished configuring Secure Burn Plus, the Permissions Manager can be locked or deleted from the computer to prevent the user from making unauthorised changes. If deleted, the security polices will still be in force. A more sophisticated server-based management approach is available in the more expensive Roxio Secure Managed version of the software, but this isn't yet available in Europe for reasons Roxio has yet to reveal to us.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
-
 CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do that
CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do thatNews The incident at CISA raises yet more concerns about the rise of ‘shadow AI’ and data protection risks
By Ross Kelly Published
-
 Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documents
Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documentsNews Linwei Ding told Chinese investors he could build a world-class supercomputer
By Emma Woollacott Published
-
 OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anway
OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anwayNews OpenAI has confirmed plans to retire its popular GPT-4o model in February, citing increased uptake of its newer GPT-5 model range.
By Ross Kelly Published