ForeScout Technologies CounterACT 6.3.4
Network access control (NAC) products are often seen as expensive and difficult to deploy. ForeScout's CounterACT claims to be anything but and in this review Dave Mitchell tests this latest virtual appliance.
Compared with many NAC products, we found CounterACT easy to deploy and, apart from setting up switch span ports, requires no major changes to the existing network infrastructure. Its policy-based security makes it very versatile allowing administrators to provide controlled, secure network access to managed, unmanaged and guest systems as they attempt to join the network.

Compliancy policies check systems to ensure they have required components such as specific anti-virus software products. These can also check for apps such as IM and P2P and the policy can be set to terminate the program if the user tries loading them.
Mobile devices are on CounterACT's radar as it can manage products such as iPhones and iPads as well as Blackberry, Android and Windows Mobile smartphones. It can query the device and use policies to manage usage. For greater control ForeScout is now developing agents for them with an Android agent already available.
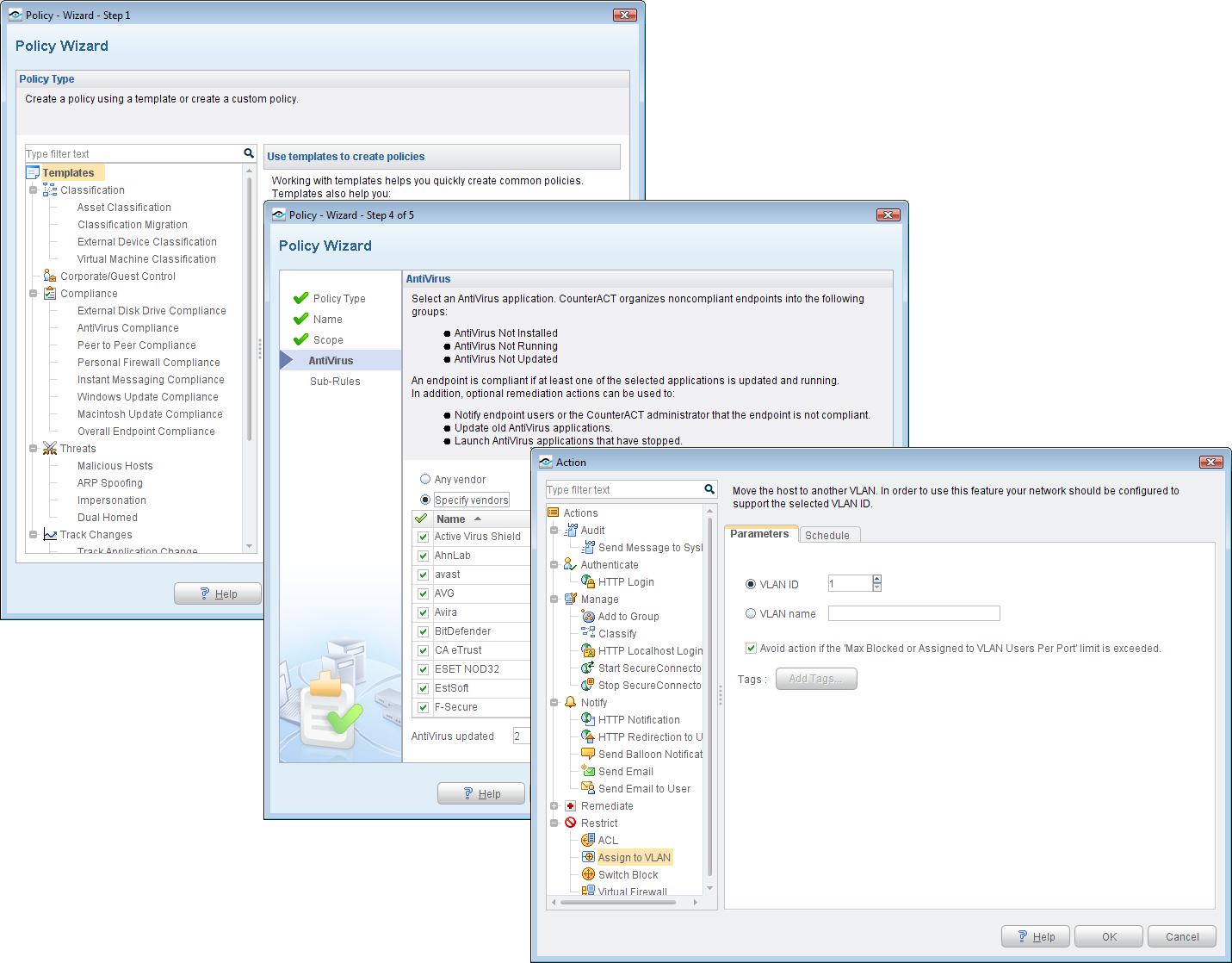
Policy creation is wizard driven and these can be used to check on required software products and apply a range of actions to non-compliant systems.
Although Windows clients that are part of an AD domain can have network access controlled without an agent, there are a number of circumstances where it is required. CounterACT can restrict access to external devices such as USB storage but needs the SecureConnector agent loaded which can be easily downloaded from a self-service portal or pushed out via a policy.
With this agent installed on a Windows 7 test client we created a policy to block all access to USB storage devices. When we inserted a flash drive the agent promptly blocked access. We also created policies that terminated IM and P2P apps - when we loaded Windows Live Messenger and a BitTorrent client, the SecureConnector agent closed them both down immediately.
ForeScout's CounterACT is a good choice for businesses that don't want to make any major changes to their networks to accommodate a NAC solution. CounterACT is comparatively good value and we found the new virtual appliance version easy to deploy and capable of providing strong policy-based network security and access controls.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Verdict
Compared with many NAC products, we found CounterACT easy to deploy and, apart from setting up switch span ports, requires no major changes to the existing network infrastructure. Its policy-based security makes it very versatile allowing administrators to provide controlled, secure network access to managed, unmanaged and guest systems as they attempt to join the network.
Operating System: VMware ESX/ESXi 3.5 and above Memory: 1.5GB Hard disk: 80GB free space
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Trump's AI executive order could leave US in a 'regulatory vacuum'
Trump's AI executive order could leave US in a 'regulatory vacuum'News Citing a "patchwork of 50 different regulatory regimes" and "ideological bias", President Trump wants rules to be set at a federal level
By Emma Woollacott Published
-
 Microsoft Excel is still alive and kicking at 40 – and it's surging in popularity as 82% of finance professionals report ‘emotional attachment’ to the spreadsheet software
Microsoft Excel is still alive and kicking at 40 – and it's surging in popularity as 82% of finance professionals report ‘emotional attachment’ to the spreadsheet softwareNews A recent survey found Gen Z and Millennial finance professionals have a strong “emotional attachment” to Microsoft Excel
By Emma Woollacott Published
-
 LastPass hit with ICO fine after 2022 data breach exposed 1.6 million users – here’s how the incident unfolded
LastPass hit with ICO fine after 2022 data breach exposed 1.6 million users – here’s how the incident unfoldedNews The impact of the LastPass breach was felt by customers as late as December 2024
By Emma Woollacott Published
