ForeScout Technologies CounterACT 6.3.4
Network access control (NAC) products are often seen as expensive and difficult to deploy. ForeScout's CounterACT claims to be anything but and in this review Dave Mitchell tests this latest virtual appliance.
Compared with many NAC products, we found CounterACT easy to deploy and, apart from setting up switch span ports, requires no major changes to the existing network infrastructure. Its policy-based security makes it very versatile allowing administrators to provide controlled, secure network access to managed, unmanaged and guest systems as they attempt to join the network.


The ForeScout Technologies logo
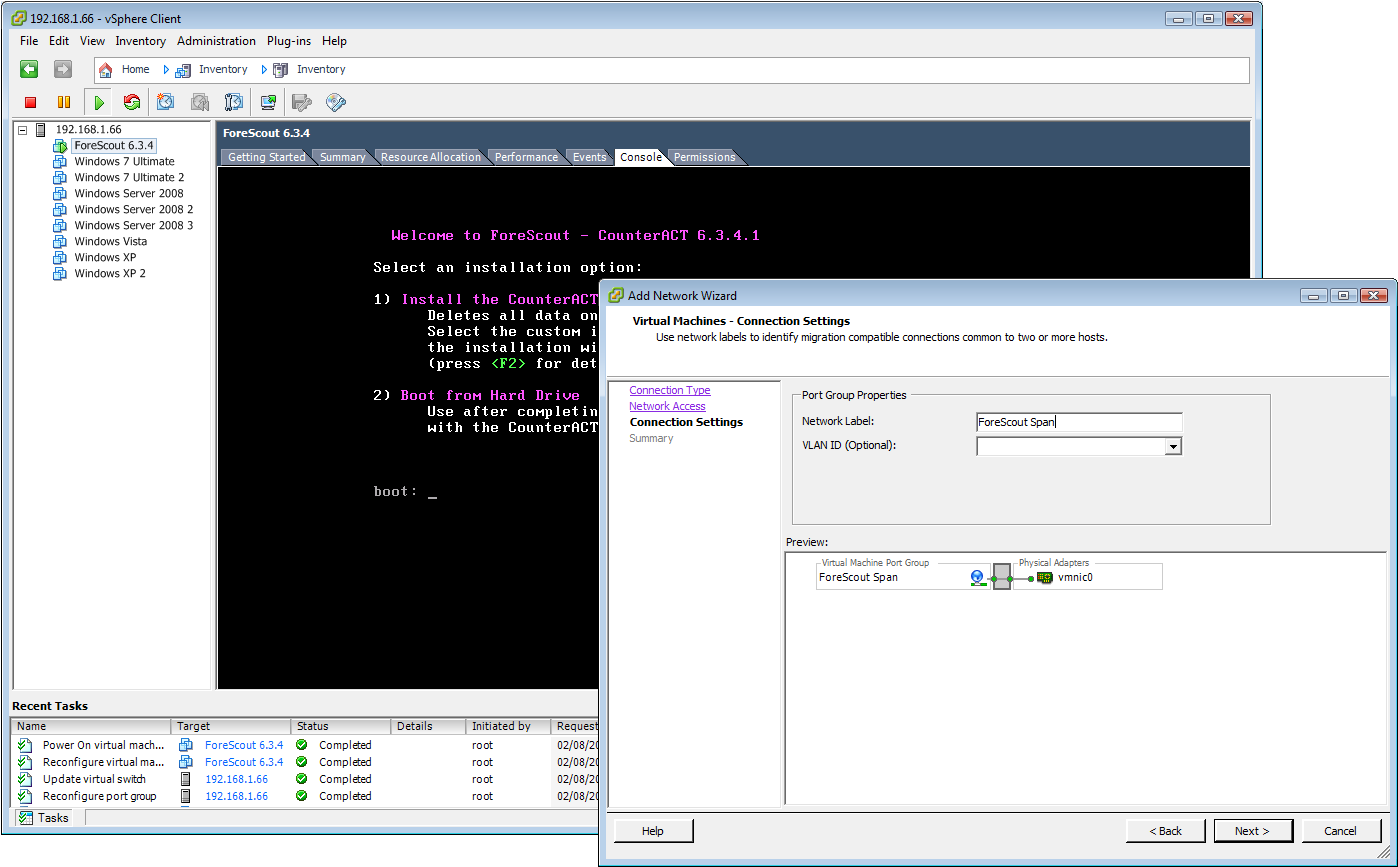
Virtual appliance installation is straightforward and CounterACT requires a dedicated virtual switch for its span port.
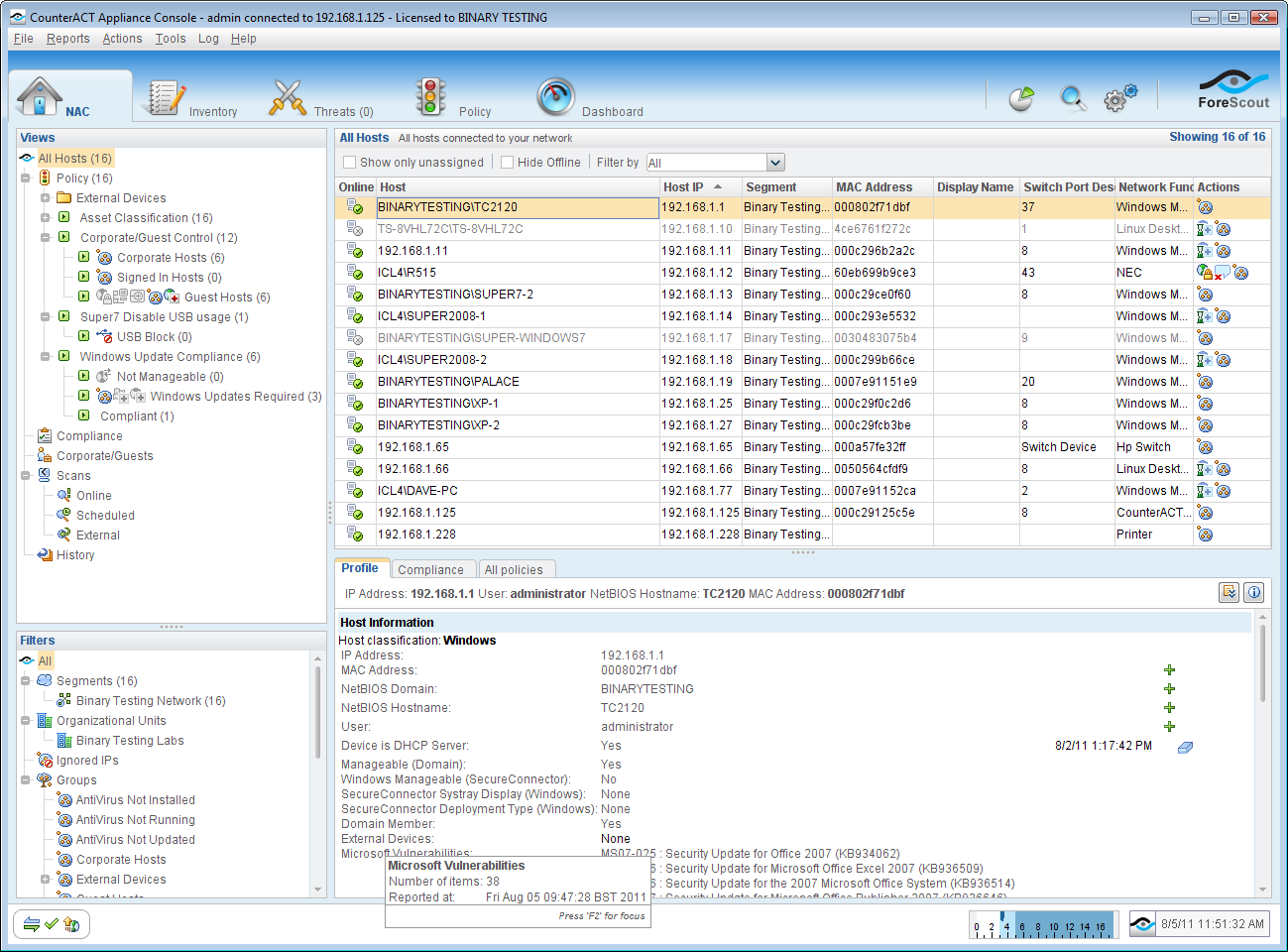
The CounterACT Console is well designed and provides high levels of information about monitored systems and policy status.
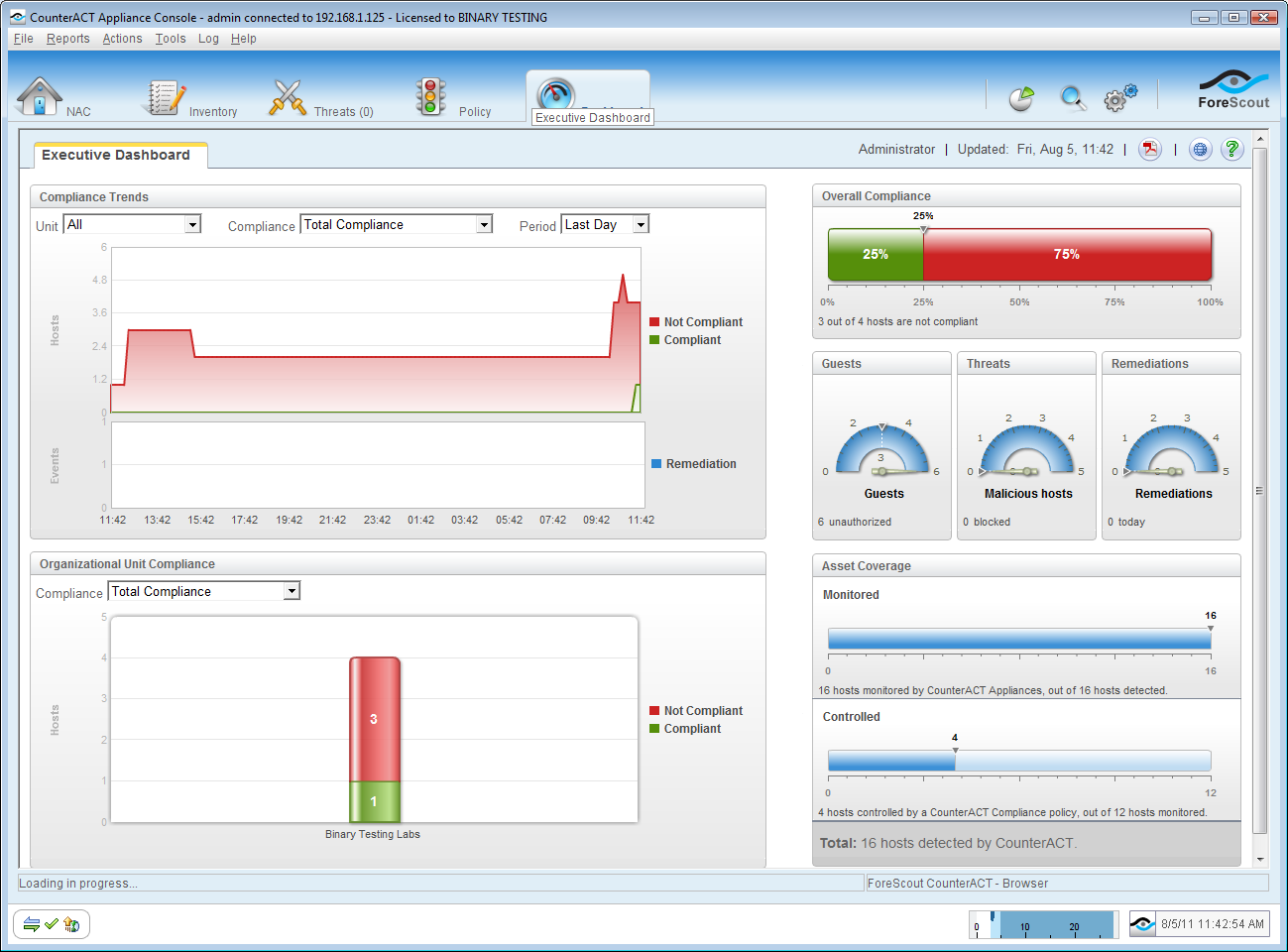
The new Dashboard in this latest version provides a useful overview of monitored systems and policy compliance.

Clients that are not compliant with CounterACT policies can access a web page that lists the reasons and can offer remediatio
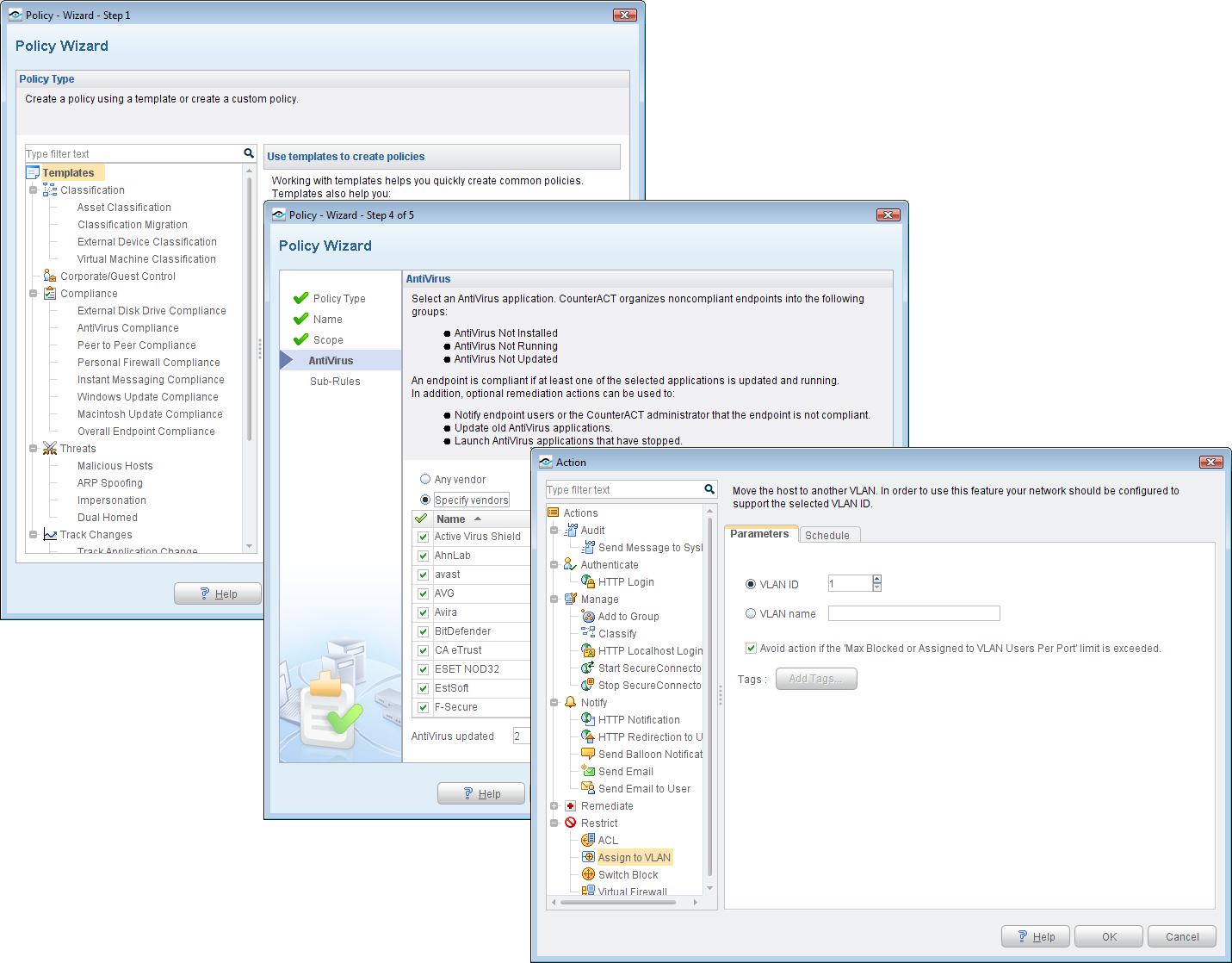
Policy creation is wizard driven and these can be used to check on required software products and apply a range of actions to
The network access control (NAC) market has seen a modest growth over the past few years, but the added pressures of compliance with data protection regulations has sparked increased interest. Established in 2000, ForeScout Technologies has been in this game longer than most and its latest CounterACT 6.3.4 is now available as a virtual appliance.
CounterACT is designed to provide full visibility of all network devices, users and applications, use baselines to determine their security posture and permit appropriate network access based on these findings. ForeScout offers it preinstalled on a range of hardware appliances, but now supports VMware ESX and ESXi
One of the biggest drawbacks of many NAC solutions is their inability to work within existing network infrastructures but CounterACT avoids these problems with two methods of network scanning. An OOB (out-of-band) mode uses a switch span port to see all network traffic and also allows CounterACT to provide intrusion prevention and apply virtual firewall policies. It can also query devices such as firewalls and routers about connected devices. This uses SNMP or CLI access and requires a plug-in for the device which ForeScout provides for all major vendors.

Virtual appliance installation is straightforward and CounterACT requires a dedicated virtual switch for its span port.
CounterACT uses a response port to enforce NAC policies with actions such as HTTP redirection, VLAN quarantining and virtual firewall blocking. If it spots potentially malicious traffic it also uses the response port to redirect the traffic to a virtual host it creates on the fly so it can examine it.
For installation, we created a new virtual machine on one of the lab's VMware ESX Server 4 systems. ForeScout provides an ISO image rather than an OVF template so you need to upload the file into the VM's datastore and set it as the boot media.
For OOB operations you create a new virtual switch with a dedicated physical network port on the VMware host. This is assigned to the CounterACT VM and must be set to promiscuous mode so it can see all traffic.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 AWS and NTT Data team up to drive legacy IT modernization in Europe
AWS and NTT Data team up to drive legacy IT modernization in EuropeNews Partnership between AWS and NTT DATA aims to boost AWS European Sovereign Cloud capabilities
By Nicole Kobie Published
-
 What the UK's new Centre for AI Measurement means for the future of the industry
What the UK's new Centre for AI Measurement means for the future of the industryNews The project, led by the National Physical Laboratory, aims to accelerate the development of secure, transparent, and trustworthy AI technologies
By Emma Woollacott Published
-
 ‘In the model race, it still trails’: Meta’s huge AI spending plans show it’s struggling to keep pace with OpenAI and Google – Mark Zuckerberg thinks the launch of agents that ‘really work’ will be the key
‘In the model race, it still trails’: Meta’s huge AI spending plans show it’s struggling to keep pace with OpenAI and Google – Mark Zuckerberg thinks the launch of agents that ‘really work’ will be the keyNews Meta CEO Mark Zuckerberg promises new models this year "will be good" as the tech giant looks to catch up in the AI race
By Nicole Kobie Published
