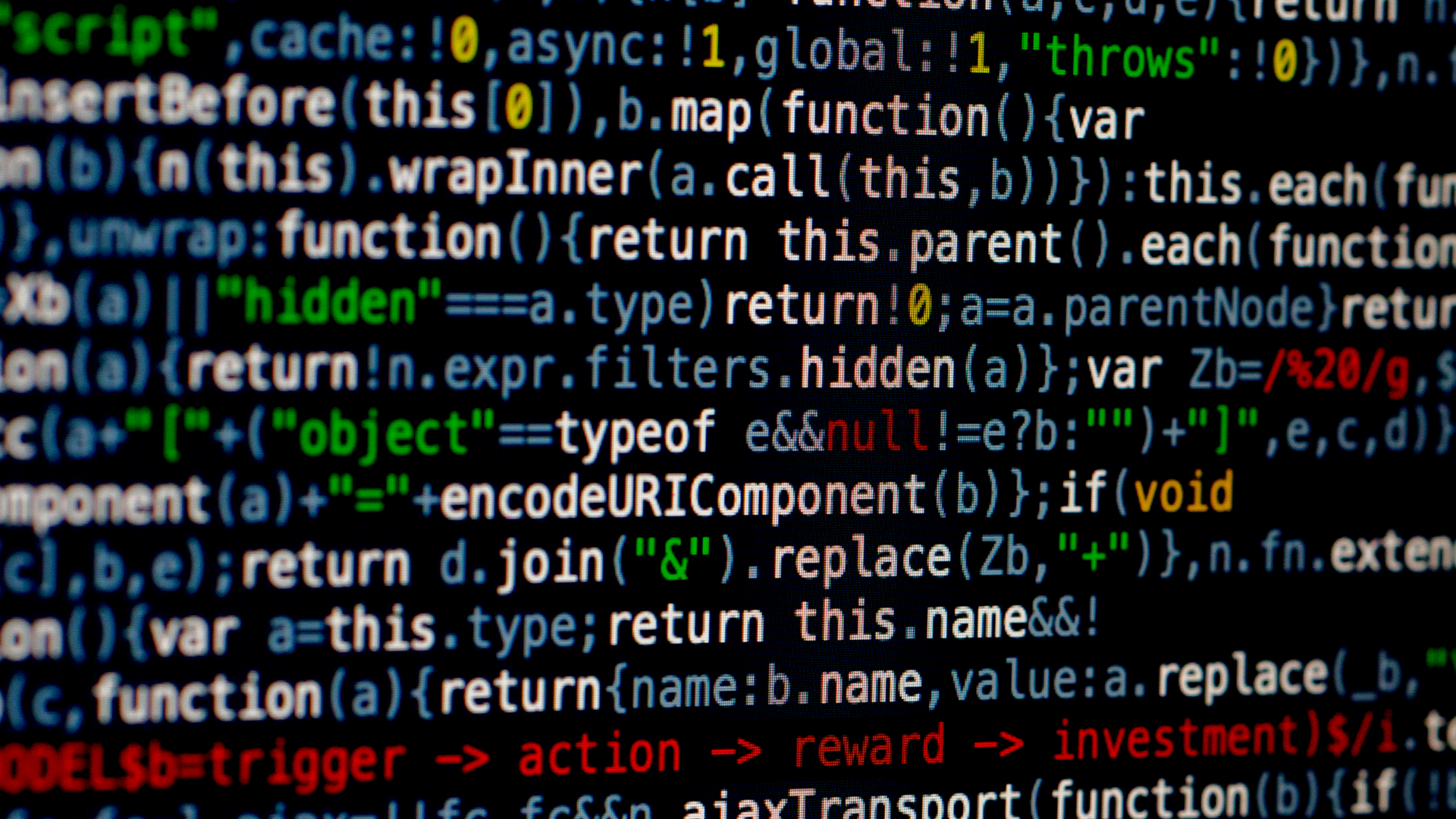
A quarter of all malicious JavaScript is obfuscated
Hackers using concealed packers to avoid detection

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Hackers obfuscate over 25% of malicious JavaScript code to avoid detection, new research has found.
Analysis of 10,000 malicious JavaScript samples, representing threats like malware droppers, phishing pages, scammers, and cryptominers’ malware, revealed that at least 25% of the examined samples used JavaScript obfuscation techniques to evade detection, according to security researchers at Akamai.
Obfuscation makes it harder for humans to understand the code running, but this is not the case for the machine, which will run it as normal.
Researchers said this significant percentage of files indicates continued adoption of obfuscation techniques by cyber criminals that want to stay under the radar.
While hackers use packers to compress and encrypt code to prevent detection, the obfuscated code samples appear similar. This is because the same packers are used, making the code structure similar despite having different functions.
Researchers gave an example of four pieces of JavaScript code — two phishing codes, one malware dropper, and one Magecart scammer — with the same structure and executing the same obfuscation functionality.
“These four examples are the output of the same unique packer functionality being used to obfuscate any given JavaScript code,” said researchers.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
By profiling packers and their functionality, researchers said they could evaluate 30,000 benign and malicious JavaScript files and see that at least 25% of the malicious files used one of five profiled packer functionalities.
RELATED RESOURCE

How to plan for endpoint security against ever-evolving cyber threats
Safeguard your devices, data, and reputation
While many obfuscated code samples appeared to be malicious, the report said 0.5% of the 20,000 top-ranking websites on the web were also using obfuscation techniques.
The researchers found that legit websites use obfuscation for various reasons. Some use it to conceal their client-side code functionality, while others have code that a third-party provider obfuscated. Some also use it to protect sensitive information, like email addresses.
Researchers said this evidence sheds more light on the challenges of detecting malicious JavaScript. It shows that obfuscation alone is not enough to indicate the presence of malicious code.
“The approach for detecting malicious obfuscation requires more advanced machine learning techniques that enable differentiation between malicious and benign obfuscated JavaScript,” said researchers.
“A better approach for detection should be one that uses additional indicators and considers obfuscated code as suspicious till proven otherwise. Indicators can be in the form of website features, like domain age and website popularity rank, or in the form of JavaScript code features, like code size and complexity,” they added.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.


