What is phishing?
From banking scams to industrial espionage, we look at why phishing is so lucrative

From banking scams to industrial espionage, phishing continues to be one of the most lucrative methods for cybercriminals. Every day, employees are inundated with thousands of emails, many of which are designed to look like urgent requests from trusted sources.
This overwhelming volume makes it incredibly challenging to scrutinize each message, and even a single missed red flag can lead to significant breaches of security.
Recent figures from the UK Government’s Cyber Security Breaches Survey 2024 reveal that a staggering 84% of businesses reported encountering phishing attacks in the past year. This persistent prevalence underscores the fact that the human element remains the weakest link in cyber defense.
Whether it’s the lure of a seemingly routine request for account verification or a cleverly disguised alert about a failed transaction, phishing attacks aim to trick individuals into surrendering money, personal data, or login credentials.
Even as organizations invest in more sophisticated security solutions, the simple act of opening a malicious email attachment continues to be one of the most effective methods for attackers. The ease with which phishing campaigns bypass technical safeguards only reinforces why cybercriminals remain undeterred by traditional defenses.
In this article, we explore some of the evolving tactics behind phishing attacks and what motivates cybercriminals to exploit these vulnerabilities.
The first phishing attacks
Although the concept of phishing was first theorized in 1987, it wasn’t until the widespread adoption of the consumer internet in the 1990s that the technique truly began to flourish. One of the earliest and most infamous instances of phishing involved a tool known as AOHell.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
This rudimentary program, designed for use on AOL, allowed attackers to impersonate customer service representatives and trick users into handing over their passwords. Once the victims divulged their credentials, the attackers could exploit their accounts for various nefarious purposes.
This use of deceptive social engineering remains the cornerstone of phishing today — even though the tactics and techniques have grown far more sophisticated. Modern phishing campaigns now employ a wide range of strategies, from AI-driven messaging to multi-channel scams, but they still fundamentally rely on tricking individuals into compromising their own security.
How to spot a phishing attack
Most users encounter phishing attacks primarily through malicious emails. While many of these harmful messages are intercepted by built-in filters — alerting users to suspicious content or flagging recent attacks associated with a sender's address — attackers continue to evolve their tactics. As a result, some phishing emails still manage to bypass these defenses, emphasizing the need for constant vigilance, especially when receiving unexpected emails from companies you’ve never dealt with.
Beyond relying on technical safeguards, it's crucial for individuals to adopt a healthy skepticism when reviewing their inboxes. Always verify the legitimacy of an email by checking the sender's details, looking for any irregularities in language or branding, and confirming suspicious requests directly through a known contact method. By combining advanced filtering with informed, cautious user behavior, you can better protect yourself from falling victim to these evolving cyber threats.
Unusual sender address
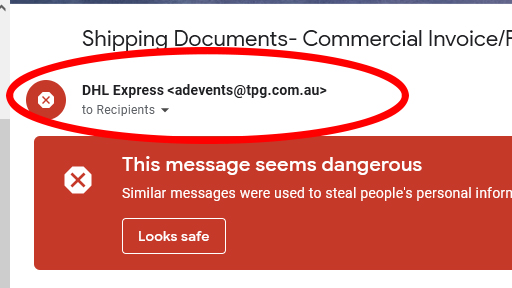
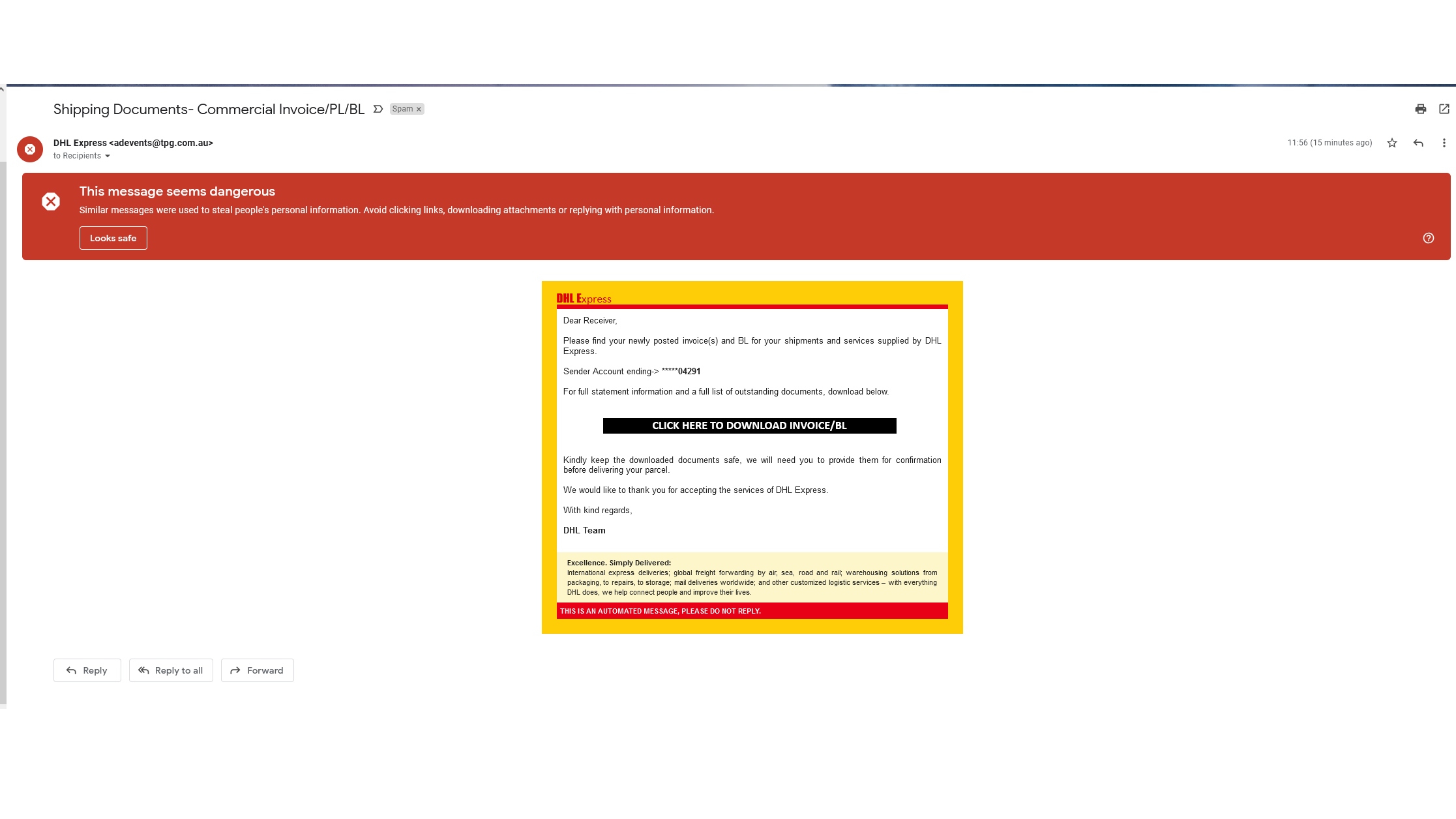
An email from a legitimate company typically originates from a standard, recognizable address that reflects the brand's domain. While sophisticated attackers may attempt to mimic official domains — such as using "PayPal.net" instead of "PayPal.com" — many malicious emails come from addresses that are clearly suspicious or unrelated, hoping the recipient won't scrutinize the sender's details. For instance, an email purporting to be from "DHL Express" might be sent from an unrecognizable address, which should raise immediate concerns.
It's crucial to examine the sender's email address carefully, as phishing attempts often involve deceptive tactics like slight misspellings or alterations in the domain name. Additionally, be wary of emails originating from public domains (e.g., @gmail.com) instead of the company's official domain. Always verify the sender's authenticity before engaging with the content, especially if the message prompts urgent actions or requests sensitive information.
Spelling mistakes, grammatical errors, strange phrasing
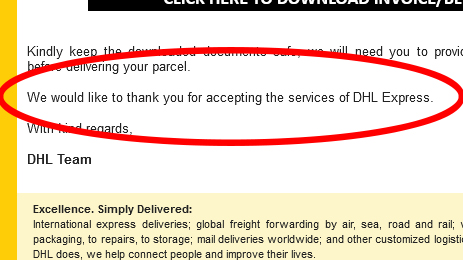
Legitimate emails typically undergo multiple rounds of proofreading and quality checks — especially those sent automatically.
As a result, spelling mistakes, grammatical errors, or awkward phrasing should immediately raise suspicion. While an occasional minor error might be understandable in a more personal message, glaring mistakes are a clear red flag. For example, the email shown above concludes with an official-sounding sign-off that just doesn’t seem authentic.
Mitigating against phishing
As cybercriminals continue to evolve and launch increasingly sophisticated phishing campaigns, it is essential that employers invest in comprehensive training to help staff identify and report suspicious emails and messages.
Employees should be adept at recognizing the typical indicators of a phishing attempt and must know the proper protocols for alerting their security teams. However, even with robust training, there will inevitably be instances when phishing scams bypass individual vigilance. Therefore, it is equally important to implement strong technical controls to prevent malicious emails from reaching staff and to have well-defined incident response plans in place for when breaches occur.
Shelby Flora, managing director for security at the UK and Ireland arm of professional services firm Accenture, says businesses must take a “multi-faceted approach” to tackling advanced phishing attacks. This should include cyber security awareness training and technical safeguards like multi-factor authentication, spam filtering solutions, and continuous monitoring programs.
"Additionally, encouraging a policy of verification before responding to unexpected requests for information or access can serve as a critical barrier against social engineering tactics," she adds.
The cost of phishing
Phishing remains the single biggest cyber security threat faced by businesses (84%) and charities (83%), according to the UK Government’s 2024 Cyber Security Breaches Survey.
These threats and others have led to the UK developing new systems to better rate the severity of cyber-attacks to improve responses and understanding of the risks.
The awareness of British employees regarding their impact on organizational cyber security has improved. A recent blog by Egress found that there has been a 28% increase in phishing emails sent between April and June vs January and March, 2024.
Despite the serious risk posed by phishing emails, a recent Proofpoint survey found that 67% of British employees are aware that their actions are harming their organization’s cyber security posture.
Geographically, the US remains by far and away the most-targeted country for phishing, with 1.13 billion attacks recorded between 2023 and 2024, according to Zscaler research, India followed this (79.1 million), Canada (58.6 million), Germany (57 million), and the UK (12.9 million).
From an industry perspective, Zscaler found that attacks against finance and insurance companies make up around 28% of all phishing attempts — followed by manufacturing (21%), the services industry (15.8%), technology (11%), retail and wholesale (6.2%), government (5.2%), healthcare (4.6%) and education (4.4%).
There has also been a 109% growth in the number of phishing attacks using malicious links disguised as legitimate Salesforce URLs, according to the CRM giant.
Phishing subtypes
Under the umbrella of "phishing", security researchers have identified a number of sub-groups that are even more targeted in their approach, with the two most common being spear-phishing and whaling.
Spear phishing: This is a phishing campaign that targets a specific individual or company. This technique requires a bit more effort on the part of the cybercriminal, as they need to do more background research in order to create a personalized phishing email.
According to research, 88% of organizations worldwide reported spear-phishing attacks in 2019.
Whaling: This is a highly targeted form of spear-phishing that specifically aims at senior executives, such as CEOs and CFOs. Unlike broad phishing campaigns, whaling attacks are meticulously crafted to appear as urgent and legitimate communications — often disguised as legal notices, executive directives, or critical business matters requiring immediate attention.
These emails typically pressure the recipient into transferring large sums of money or revealing sensitive company information under the guise of authority and urgency.
Such scams can be devastating, as they require minimal technical expertise yet yield massive financial rewards for attackers. A notable example is the case of an Austrian aerospace company that, in 2016, suffered nearly $50 million in losses due to a Business Email Compromise (BEC) scam — an attack so severe that it led to the dismissal of the company's CEO. The rising sophistication of these scams highlights the importance of executive-level cybersecurity awareness and robust verification protocols to mitigate risks.
Quishing: This is a newer tactic, quishing involves embedding malicious URLs within QR codes. When scanned, these codes direct users to phishing websites designed to steal personal information. This method leverages the growing use of QR codes in various applications, making it a timely threat.
The use of Artificial Intelligence (AI) in phishing campaigns
AI tools are making it even easier for cybercriminals to design and disseminate highly convincing phishing campaigns.
According to research from Zscaler, such attacks have increased by almost 60%. Meanwhile, Harvard University found that 60% of people have experienced AI-driven phishing attacks.
Hackers are turning to AI software like ChatGPT, Stable Diffusion and Midjourney to increase the volume of phishing attacks and make them more believable, according to Jess Burn, principal analyst at market research firm Forrester.
In particular, she says generative AI is aiding the creation of “compelling text and images” that “improve the quality of phishing emails and websites”. Hackers can then use this technology to “compose their attacks on a greater scale,” she warns.
Burn notes, however, that hackers still spread most of these attacks using “spoofed accounts or domains”. She adds: “We’re expecting cyber attacks to increase in number but the threats themselves are not novel. Security analysts and incident responders already know how to identify, resolve, and mitigate them.
Martin Borrett, UK and Ireland technical director at IBM Security, explains that cybercriminals can leverage AI tools to “analyze user behavior, preferences, and patterns”. This information helps them design “highly personalized and targeted phishing emails and social engineering campaigns that are more likely to succeed”.
He adds: “Additionally, AI can help automate the process of crafting and sending these messages, enabling attackers to carry out large-scale and coordinated attacks more efficiently."
Jon France, chief information security officer at the non-profit cyber security certification body ISC2, suggests that cybercriminals are no longer focusing on email phishing scams due to the rise of AI. He says they can now use deep fakes, AI-generated fake videos of real people, to trick victims into handing over their passwords, payment information, and cash.
This technology is also resulting in “multi-stage campaigns” that see cybercriminals “increase their chances of success by narrowing their focus and refining their tactics based on the information gathered at each stage”. He adds: “The information obtained can be used to carry out more targeted and convincing attacks later down the line.”
RELATED WEBINAR

Other key phishing trends: Spam, BEC, vishing
In addition to a sharp rise in AI-based phishing campaigns, many other notable phishing trends emerged in 2024.
One key development was the growing sophistication of unwanted emails, according to Borrett. He says people are finding it harder to “distinguish legitimate business emails from phishing emails”.
To avoid this, he advises the following: “Verify the sender, decide if an email is valid before clicking links or attachments, and verify the email without forwarding it to others.”
Burn says cybercriminals are spending greater amounts of time trying to understand their victims, in the hopes of designing and conducting more advanced phishing and business email compromise (BEC) attacks.
“Yes, there are some that still take a “spray and pray” approach but many know that a well-crafted phishing message will allow them to get that desired foothold in their target organization," she explains.
Jack Peters, customer solutions architect at cloud and connectivity provider M247, notes a growth in cross-channel and voice-based phishing attacks (also known as vishing). He explains that cybercriminals are using a range of voice calls, emails, and text messages as part of advanced phishing campaigns that “manipulate victims into revealing sensitive information".
“It takes many forms, including prompting the recipient to take action on a fake receipt sent to them by email, or to reply to an IT support issue, or impersonating authorities or legal entities."
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
- Nicholas Fearn
- Clare HoppingFreelance writer


