Microsoft mishap leaves 38TB of private data exposed for three years
Microsoft’s blunder first occurred in 2020 and wasn’t uncovered until June this year


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
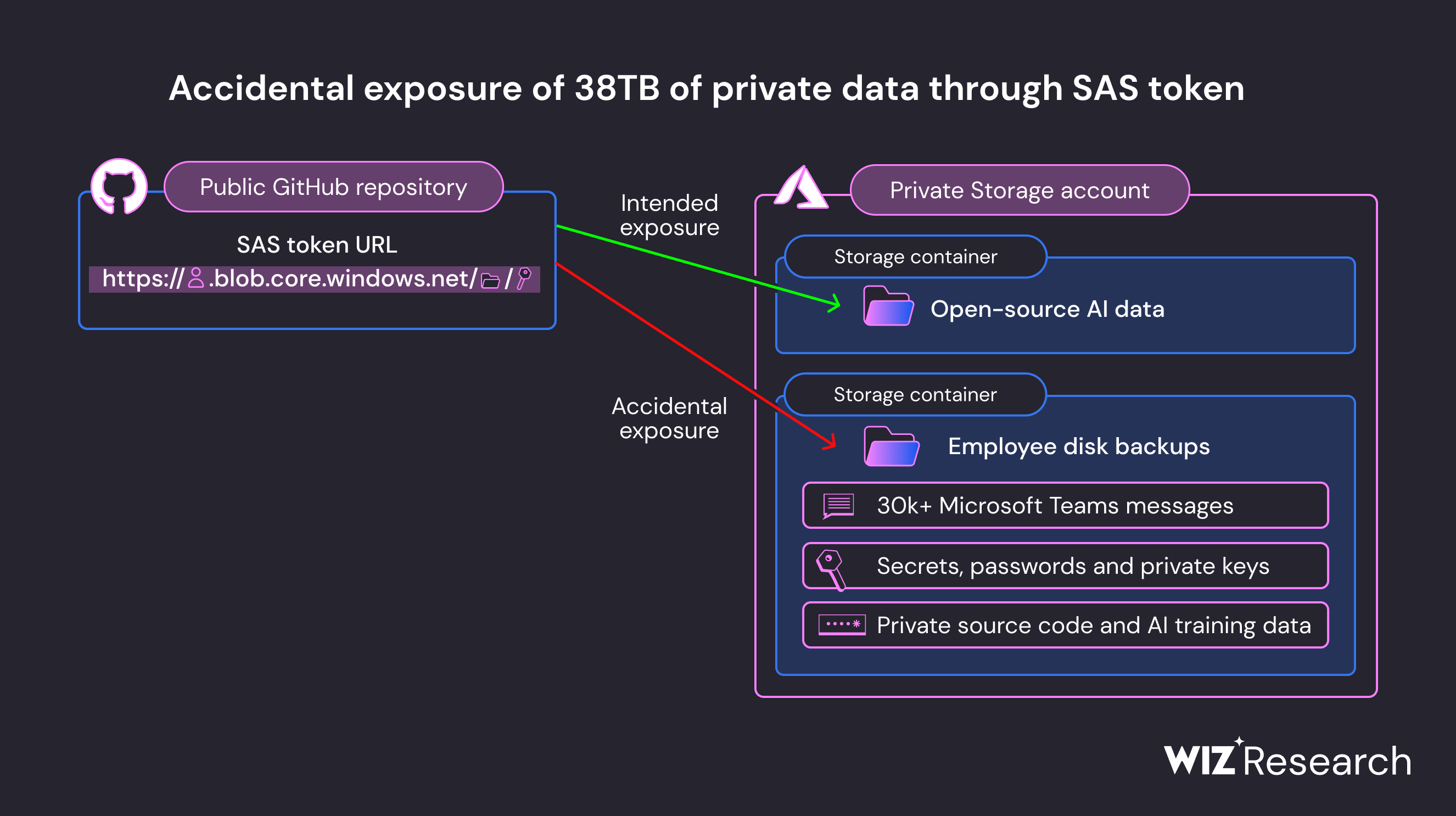
Up to 38TB of sensitive company information was accidentally leaked by Microsoft AI staffers due to a misconfigured Azure SAS token, according to new research.
Analysis from researchers at cloud security firm Wiz found that Microsoft’s AI research team uploaded an overly permissive URL to its GitHub repository which directed anyone to access the trove of what should be private data.
Data exposed in the mishap included full backups of two employee work devices, both of which contained data including passwords to Microsoft services, private keys, and records of more than 30,000 internal Microsoft Teams messages.
As part of its activity on the platform, Microsoft’s AI research team regularly provides links to open source training data for the community to use, but the link in question led to an Azure Storage bucket which was misconfigured, allowing access to more private data.
Researchers at the tech giant were found to have shared files using Azure Shared Access Signature (SAS) tokens, which enable users to access and share data from the service’s storage accounts.
Typically, SAS tokens prevent unauthorized users from accessing files. However, in this instance a URL to stored data was configured to grant permission to the entire account, Wiz found.
“The [Microsoft] researchers shared their files using an Azure feature called SAS tokens, which allows you to share data from Azure Storage accounts,” Wiz’s team said.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“The access level can be limited to specific files only; however, in this case, the link was configured to share the entire storage account – including another 38TB of private files.”
The investigation from Wiz found that the initial mishap occurred in July 2020 and went unnoticed for nearly three years, although Wiz only made the discovery in June 2023.
Researchers informed Microsoft of the issue after making the discovery. Microsoft then conducted an investigation into the potential risk to customers.
Microsoft said in a statement this week there was no evidence that customer data was exposed. Similarly, the firm said that “no other internal services were put at risk because of the issue”.
“A researcher at Microsoft inadvertently included this SAS token in a blob store URL while contributing to open source AI learning models and provided the URL in a public GitHub repository,” Microsoft confirmed.
“There was no security issue or vulnerability within Azure Storage or the SAS token feature.”
RELATED RESOURCE
Watch this on-demand webinar and learn how multi-cloud environment accelerate network transformation initiatives
Wiz said the incident highlights the need for more robust governance and monitoring practices with regard to SAS tokens.
Researchers noted that Microsoft does not offer a “centralized way” to manage tokens, which presents security risks due to the difficulties teams may have in tracking them.
“Due to a lack of monitoring and governance, SAS tokens pose a security risk, and their usage should be as limited as possible,” Wiz said. “These tokens are very hard to track, as Microsoft does not provide a centralized way to manage them within the Azure portal.”
“In addition, these tokens can be configured to last effectively forever, with no upper limit on their expiry time. Therefore, using Account SAS tokens for external sharing is unsafe and should be avoided.”
Microsoft said the incident has prompted a reassessment of SAS token management processes.
“We are making ongoing improvements to further harden the SAS token feature and continue to evaluate the service to bolster our secure-by-default posture,” the firm said.

Ross Kelly is ITPro's News & Analysis Editor, responsible for leading the brand's news output and in-depth reporting on the latest stories from across the business technology landscape. Ross was previously a Staff Writer, during which time he developed a keen interest in cyber security, business leadership, and emerging technologies.
He graduated from Edinburgh Napier University in 2016 with a BA (Hons) in Journalism, and joined ITPro in 2022 after four years working in technology conference research.
For news pitches, you can contact Ross at ross.kelly@futurenet.com, or on Twitter and LinkedIn.
-
 ITPro Best of Show NAB 2026 awards now open for entries
ITPro Best of Show NAB 2026 awards now open for entriesThe awards are a fantastic opportunity for companies to stand out at one of the industry's most attended shows
-
 Mistral CEO Arthur Mensch thinks 50% of SaaS solutions could be supplanted by AI
Mistral CEO Arthur Mensch thinks 50% of SaaS solutions could be supplanted by AINews Mensch’s comments come amidst rising concerns about the impact of AI on traditional software
-
 Cloud infrastructure spending hit $102.6 billion in Q3 2025 – and AWS marked its strongest performance in three years
Cloud infrastructure spending hit $102.6 billion in Q3 2025 – and AWS marked its strongest performance in three yearsNews Hyperscalers are increasingly offering platform-level capabilities that support multi-model deployment and the reliable operation of AI agents
-
 Dell Technologies targets private cloud gains with new Azure Local features
Dell Technologies targets private cloud gains with new Azure Local featuresNews Dell and Microsoft are teaming up to offer private cloud on Azure Local for a simplified hybrid solution
-
 Microsoft’s new ‘marketplace’ lets customers pick and choose cloud, AI solutions
Microsoft’s new ‘marketplace’ lets customers pick and choose cloud, AI solutionsNews The Microsoft Marketplace looks to streamline customer access to AI and cloud services
-
 Is AWS' cloud dominance waning? New stats show the hyperscaler's IaaS market share is decreasing while Microsoft and Google record gains
Is AWS' cloud dominance waning? New stats show the hyperscaler's IaaS market share is decreasing while Microsoft and Google record gainsNews AWS maintained its lead in the IaaS market last year, but its share decreased while Microsoft and Google recorded gains.
-
 ‘Misses the mark’: Microsoft, AWS hit out at CMA cloud competition report
‘Misses the mark’: Microsoft, AWS hit out at CMA cloud competition reportNews The CMA claims Microsoft and AWS are harming competition – the duo strongly disagree
-
 US companies dominate the European cloud market – regional players are left fighting for scraps
US companies dominate the European cloud market – regional players are left fighting for scrapsNews Synergy data shows EU providers hold just 15% of the market despite rise in AI and drive for cloud sovereignty
-
 What the new Microsoft Sovereign Cloud push means for European customers
What the new Microsoft Sovereign Cloud push means for European customersNews The tech giant is bolstering protections for regional users using public and private cloud services
-
 Where is the cloud headed?
Where is the cloud headed?ITPro Podcast UK businesses are balancing cloud migration with AI adoption and demands for data sovereignty