Dell PowerEdge R510 review
Dell has found a gap in the rack server market and aims to be the first to fill it. Is its latest PowerEdge R510 a good fit? We investigate in this review.
The new PowerEdge R510 is an interesting alternative to standard rack mount storage servers and its compact 24in deep chassis doesn’t compromise on features. It offers plenty of remote management options and low power consumption, although if you want even more storage choices we’d recommend waiting for Dell to launch the R510 version with the higher drive bay count.


front

open

thumb
Dell's latest PowerEdge R510 aims to fit neatly into a niche in the server market as it targets small and medium-sized businesses (SMBs) that want plenty of available storage in their rack but don't want to invest in a storage area network (SAN).

The R510 may not have the depth of the R710 but it matches it easily in the storage department as its front panel has room for up to eight hot-swap hard disks. The carriers accept 3.5in. or 2.5in drives and Dell's optional RAID controllers support a mixture of SAS and SATA as well. There's more on the horizon as Dell plans to expand the R510 with even more SFF drive bays.
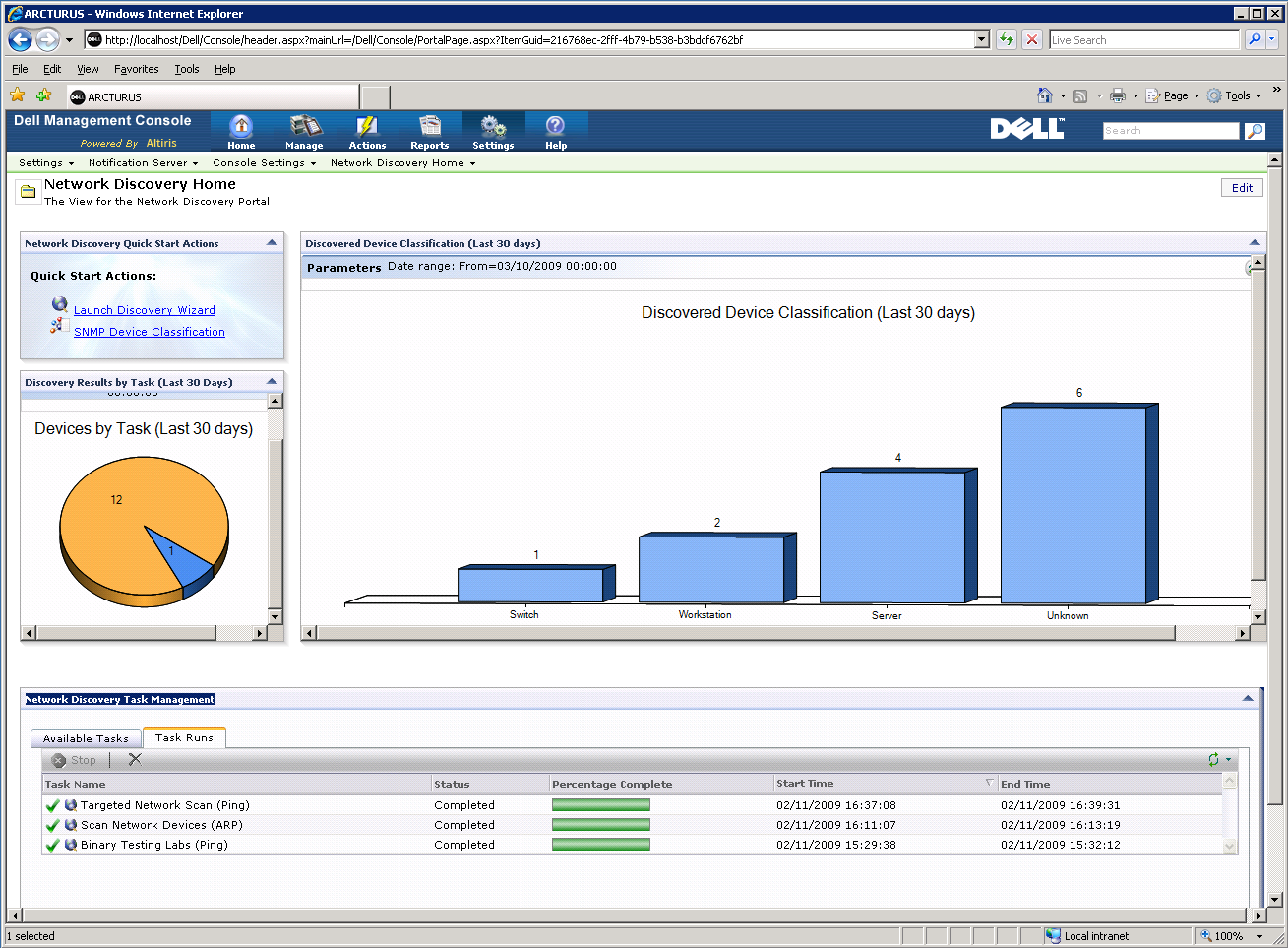
Dell's Management Console software offers a lot of useful features along with good network discovery tools.
Remote management options are in line with other 11th generation PowerEdge servers and the R510 offers three alternatives. The base model on review came with an embedded IPMI 2.0 BMC, which offers basic remote access by sharing the first network port. Access is via a command line shell although it only enables you to reboot the server and control its power supply.
Next up is Dell's iDRAC 6 Express card that snaps into a proprietary socket at the rear of the motherboard and shares the first network port to provide web browser access to the server. This brings Dell's unique Lifecycle controller into play, which adds 1GB of NVRAM memory for storing drivers and other software for immediate access.
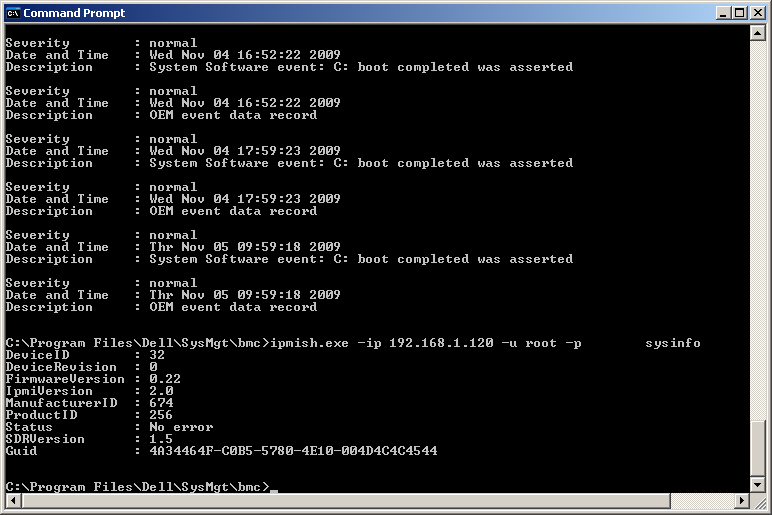
If you leave out Dell's iDRAC6 management card you can only access the BMC using the SOL command line utility.
You can't upgrade to the iDRAC 6 Enterprise version as this is a different card that fits into a separate socket on the motherboard. It presents a dedicated network management port and an advanced feature set that includes KVM-over-IP functions and an integral V-Flash media slot. When an SD card is inserted it appears as a boot option and can also be accessed from the host operating system.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 ‘1 engineer, 1 month, 1 million lines of code’: Microsoft wants to replace C and C++ code with Rust by 2030 – but a senior engineer insists the company has no plans on using AI to rewrite Windows source code
‘1 engineer, 1 month, 1 million lines of code’: Microsoft wants to replace C and C++ code with Rust by 2030 – but a senior engineer insists the company has no plans on using AI to rewrite Windows source codeNews Windows won’t be rewritten in Rust using AI, according to a senior Microsoft engineer, but the company still has bold plans for embracing the popular programming language
By Ross Kelly Published
-
 Google drops $4.75bn on data center and energy firm Intersect
Google drops $4.75bn on data center and energy firm IntersectNews The investment marks the latest move from Google to boost its infrastructure sustainability credentials
By Nicole Kobie Published
-
 OpenAI says prompt injection attacks are a serious threat for AI browsers – and it’s a problem that’s ‘unlikely to ever be fully solved'
OpenAI says prompt injection attacks are a serious threat for AI browsers – and it’s a problem that’s ‘unlikely to ever be fully solved'News OpenAI details efforts to protect ChatGPT Atlas against prompt injection attacks
By Nicole Kobie Published
