Cyberoam CR1000iNG-XP review
Cyberoam’s CR1000iNG-XP delivers enterprise network security at a price mid-sized businesses will approve


The CR1000iNG-XP offers mid-sized businesses high performance network security at a sensible price. Easy to deploy and packed with features, it can also be easily expanded to keep in step with demand
-
+
Excellent value; Easy installation; Top performance; User-based security policies; Reporting included as standard
-
-
Non hot-swap network modules

Identify yourself
After grouping our ports, we applied firewall rules to source and destination zones along with associated networks and hosts. Other network objects include service filters, blocking actions and time schedules which can be applied within each rule.
We recommend acquainting yourself with Cyberoam's identity-based security as this allows you to apply more versatile security policies to users and groups. Clients authenticating to an external directory server will be automatically logged in while others can log in to the appliance via the Corporate Client.
Cyberoam provides Linux and Mac clients plus free mobile apps for Android and iOS devices. We had no problems with the iAccess app on our iPad where it auto-detected the appliance's IP address and asked for our login details.
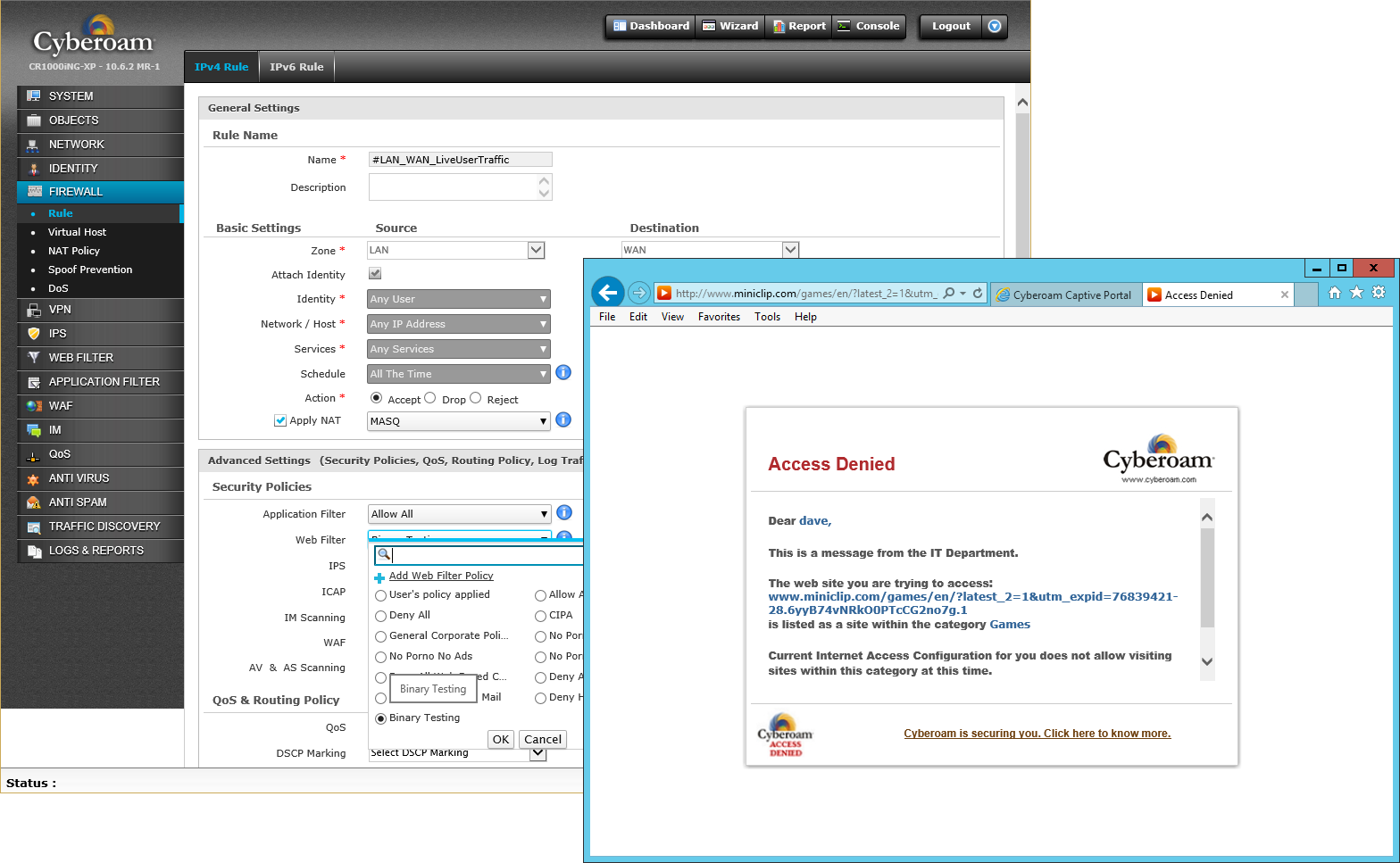
Cyberoam's web filtering can be applied to specific users and performs extremely well
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 OpenAI's 'Skills in Codex' service aims to supercharge agent efficiency for developers
OpenAI's 'Skills in Codex' service aims to supercharge agent efficiency for developersNews The Skills in Codex service will provide users with a package of handy instructions and scripts to tweak and fine-tune agents for specific tasks.
By Ross Kelly Published
-
 Cloud infrastructure spending hit $102.6 billion in Q3 2025 – and AWS marked its strongest performance in three years
Cloud infrastructure spending hit $102.6 billion in Q3 2025 – and AWS marked its strongest performance in three yearsNews Hyperscalers are increasingly offering platform-level capabilities that support multi-model deployment and the reliable operation of AI agents
By Emma Woollacott Published
-
 Google Cloud teases revamped partner program ahead of 2026
Google Cloud teases revamped partner program ahead of 2026News The cloud giant’s new-look partner ecosystem shifts focus from activity tracking to measurable customer outcomes
By Daniel Todd Published
