DailyMotion hit by sophisticated malvertising
Scammers' Angler malware appeared benign when tested by cybersecurity bods


DailyMotion has allegedly been caught serving up malware to visitors through malicious adverts - a technique known as malvertising - but the French streaming site is denying the issue ever occurred.
Malvertising makes use of the high-speed bidding and transactions that happen in online advertising, as well as the fact the process of bringing an ad to a site often involves multiple steps and organisations.
First, scammers produce an advert that, when a user clicks on it, redirects one or more times to a site hosting a malware exploit kit. They then set up an automated process to bid on advertising space that is normally sold through a third party or broker using real-time bidding.
The winning ad is then taken by the third-party and displayed through the advertising company's ad space on the host page - all in all, four entities or more can be involved.
Because of the nature of real-time bidding, the fact the ad itself appears to be genuine, and the multiple steps that lead to the advertisement appearing, it is difficult for any of the benign actors in the chain to detect the rogue assets.
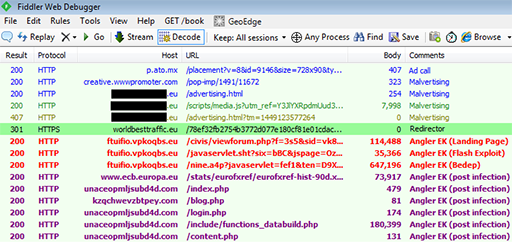
Security company Malwarebytes claims to have found the malicious advert on 2 December 2015, which was being displayed on a video of the UK X-Factor that was first uploaded to DailyMotion in November 2012.
The below log claims to show the path of the infection, which shows the redirection process malvertising uses.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Jrme Segura, senior security researcher at Malwarebytes, said he and his team had been tracking the attack via various .eu sites for several days but, until DailyMotion was hit, was unable to find the final payload.
"This particular malvertising attack is one of a few campaigns we have been tracking which is much more sophisticated than the average incidents we encounter daily. We can say that lately threat actors have really stepped up their game in terms of being very stealthy and making a particular ad call look benign when reproduced in a lab environment," Segura said in a blog post.
"Indeed, the problem comes when we suspect foul play but can't prove it with a live infection. It is difficult to convince ad networks to take action, when on the surface there's nothing wrong with a particular advertiser," he added.
Segura commended all those involved, including DailyMotion and the Atomx online media exchange platform, for their prompt action to remove the malicious advert once it was detected.
However, DailyMotion has contacted IT Pro, denying the attack happened at all.
A spokesperson for the video streaming platform said: "Dailymotion monitors the quality of ads delivered on its website through the robust technology of its advertising partners, as well as through partnerships with specialized third-party services, such as industry leader TheMediaTrust (TMT).
"TMT has looked into this article and the content shown was detected by TMT starting back in mid-November. This exact content was not seen on any Dailymotion ad tags or site scans. TMT has not detected [Atomx] on any ad tags provided for scanning in the past month."
TMT added: "TMT tried to help Atomx a long time back get their content cleaned up but recently the influx in malicious content from this company has began to grow. TMT has flagged this domain as malicious."

Jane McCallion is Managing Editor of ITPro and ChannelPro, specializing in data centers, enterprise IT infrastructure, and cybersecurity. Before becoming Managing Editor, she held the role of Deputy Editor and, prior to that, Features Editor, managing a pool of freelance and internal writers, while continuing to specialize in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.
-
 Hackers are using LLMs to generate malicious JavaScript in real time
Hackers are using LLMs to generate malicious JavaScript in real timeNews Defenders advised to use runtime behavioral analysis to detect and block malicious activity at the point of execution, directly within the browser
-
 Developers in India are "catching up fast" on AI-generated coding
Developers in India are "catching up fast" on AI-generated codingNews Developers in the United States are leading the world in AI coding practices, at least for now