How to check if your passwords have been stolen
It's likely that one or more of your passwords are sitting in a database on the dark web


Every year there is a list of most 'hacked' or leaked passwords and it always features variants on 'password' or '123456'. These default and straight-up lazy attempts to secure computers, devices and software are a big reason why there are so many security breaches.
That coupled with ever more sophisticated ways of cracking passwords and decrypting codes has lead to a large glut of access codes being brought and sold on the dark web. No matter how well you write a password, there is a big chance you have one sitting on the dark web.
Not just your passwords either, the ones that large companies use to keep your information safe is also at risk. Think about some of the biggest leaks over the last few years, such as British Airways which saw 380,000 leaked user accounts after hackers implanted rogue code on its website.
In a world where even smartphones have biometric security, such as facial recognition and fingerprint sensors, many people are still happier with a password. Problem is, we need a different one for the multiple services we use and no one seems to be taking advantage of password managers. A little education is needed, the dangers have to be spelt out and we essentially need saving from ourselves.
How are passwords stolen?
Most of us have been there. Struggling to remember one of our passwords, but bashing in those we use most in the hope of striking lucky. Then we see the dreaded message 'Too many incorrect logins account locked'. The silver lining, you might think, to this frustrating cloud is that someone trying to hack your password would suffer a similar fate.
A locked-out message might be infuriating for you, but it's no problem for hackers
Sadly, this isn't how the world works. Most passwords are cracked by hackers working offline, having already 'acquired' a database of user accounts. They will then use various methods to crack the accounts' passwords. The only time they'll ever try to log into your account is when they've already got your password. So while a limit on login attempts helps prevent people casually trying to access your accounts, it's useless if your account details have been leaked.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
How passwords are 'hashed'
The good news is that even hackers who have access to a database of account details can't see the actual passwords as plain text. Any reputable website won't ever store your password. Instead, they use an algorithm to convert it into a unique, fixed-length block of data, known as a hash.
For example, using one very popular cryptographic algorithm SHA256, which was developed by the US National Security Agency the much-used password 'P@SSWOrd' generates a 64-character hash starting 'BO3DDF3C...'.
This particular password will always create this unique hash, meaning a website can compare it to the hash of the password you enter when you log in if the two match, you're allowed in. You can see how it works by generating SHA256 hashes on the Password Generator website. Notice that when you alter a single character, the hash changes completely.
Securing passwords with a pinch of salt
Hashing lets websites store your passwords securely because it's impossible to reverse-engineer them, but hackers can still use any number of techniques to work out your password. How easy this is depends on how complex your password is and the methods used by the website to generate its hash.
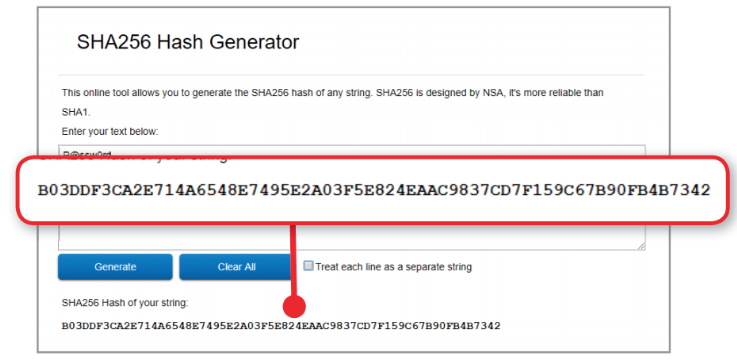
Password Generator uses the SHA256 algorithm to make unique 64-character hashes
To make it harder for hackers to use rainbow tables (databases of leaked passwords) to work out a password from its hash, most websites generate a series of random characters and add them to your password before creating the hash a process known as 'salting'.
Using a salt of aE92@3' (most are far more complex than this), our earlier password of P@ssword' becomes 'aE92@3P@assword'. Because this generates a completely different hash, it's highly unlikely it will exist in a rainbow table and will, therefore, be much harder to crack. To increase security, the website will use a different salt for each user.
How to check if your passwords have been stolen
When your passwords (or any other personal information) have been leaked, they normally end up being added to huge databases on the dark web. Trying to locate these to find out whether you've been a victim not only takes ages, but is also risky because they're typically listed on criminal websites. Thankfully, there are safe websites you can use instead.
Have I Been Pwned? (HIBP) was created in 2013 by Australian security expert Troy Hunt. It's home to a database of over five billion hacked (or 'pwned') email accounts from the many leaks that have occurred over the years. You can also search its database using Mozilla's Firefox Monitor tool, launched last month.
Hacked Emails (run by US-Spanish security firm 4IQ) and BreachAlarm (run by Australian firm Avalanche), are two popular alternatives. All three sites scan for new data leaks by monitoring sites on the dark web and websites such as Pastebin, where hackers post leaked account details. This data is then combined into a single, searchable database.
The sites use similar methods to check whether an email address was part of a data breach simply type it into the box on the home page then press Enter. While HIBP and BreachAlarm show instant results, Hacked Emails sends a link to the email address you entered, restricting you to running password scans only on addresses you can access.
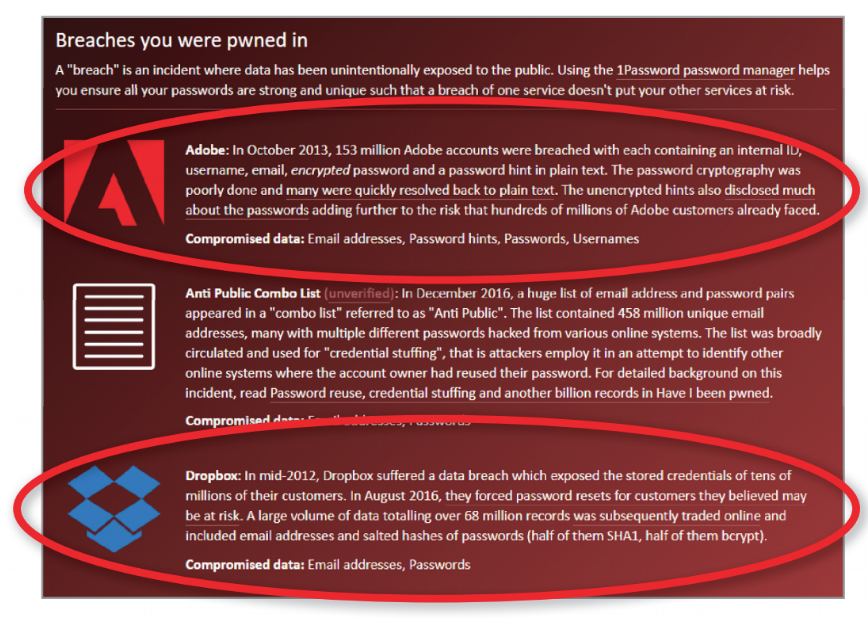
According to HIBP, our email is linked with two breaches that leaked our password and more
We tested the sites using the same email address an old Gmail account we no longer use. Both HIBP and Hacked Emails reported that it was part of the Adobe (2013) and Dropbox (2012) breaches though the former went further by specifying the type of information that was leaked. HIBP also said the address was made available through the Onliner spambot in 2017. Both also listed several 'unverified' leaks from unknown sources.
In contrast, BreachAlarm simply said our email address has been leaked "at least 2 times", with the latest being August 2016. This was disappointingly vague, but it's still worth trying BreachAlarm because it uses different databases of leaked emails. Between all three sites, you'll probably find out whether your email account has been hacked.
Run searches for your password
As well as email addresses, HIBP lets you check whether your password has been leaked. Head here or click the Passwords menu from the main HIBP site, then type your password.
We've no doubt that HIBP can be trusted, but searching your current password isn't without risk. Although unlikely, hackers might be able to steal it if they attack HIBP and install keylogger malware.
We, therefore, recommend against using a current password. Instead, try running searches for your old passwords, or simply use it to find out how common certain passwords are. For instance, '654321' has been leaked nearly one million times, while 'P@ssw0rd' nearly 50,000 times.
If you do check a current password and find it's been leaked, there's no way of telling whether it belonged to you or someone else (the simpler the password, the more it would have been used by other people). Regardless, you should still change it immediately. If the password has been seen online even just once, it will be included in rainbow tables, making it easier to crack.
What to do if your data has been leaked
If your details have been leaked, check the date of the latest breach. If you've yet to change your password on the attacked site, do so immediately. Hackers are aware people often just add an extra character when changing their password, so make sure it's completely different (don't change 'Ilovepasta' to 'Ilovepasta1'). And if you've reused the stolen password on other sites, change them there as well.
If you get the all-clear from these sites, it doesn't mean your personal details have never been leaked. Lots of smaller data breaches go unreported, while some companies simply aren't aware they've been attacked.
The best way to protect yourself is to use strong passwords and, ideally, a password manager. Also consider signing up to HIBP's monitoring service, which will email you if your details appear in a new leak. Click 'Notify me' at the top of the website, then enter the email address you want to monitor.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses