Cyberoam CR1500i review
Cyberoam’s latest UTM appliance brings its unique identity based security to bear on the enterprise. In this exclusive review we find out if the Cyberoam CR1500i hits the target.
Compared with many enterprise UTM security appliances, the CR1500i looks good value and it also offers Cyberoam’s unique identity based security. It’s easy to deploy, performs very well and allows you to create user and group based policies to control just about any type of internet related activity.

Cyberoam CR1500i
Cyberoam CR1500i

Cyberoam CR1500i
Cyberoam CR1500i
Cyberoam CR1500i

Cyberoam CR1500i
EXCLUSIVE: Cyberoam isn't a name that comes immediately to mind when considering UTM appliances but this division of the India-based EliteCore Technologies is keen as mustard to change this perception. It's been muscling into the UK market for the past year with a particular focus on the small and medium-sized business (SMB) market but in this review we take a closer look at the CR1500i which represents the very pinnacle of its product range.
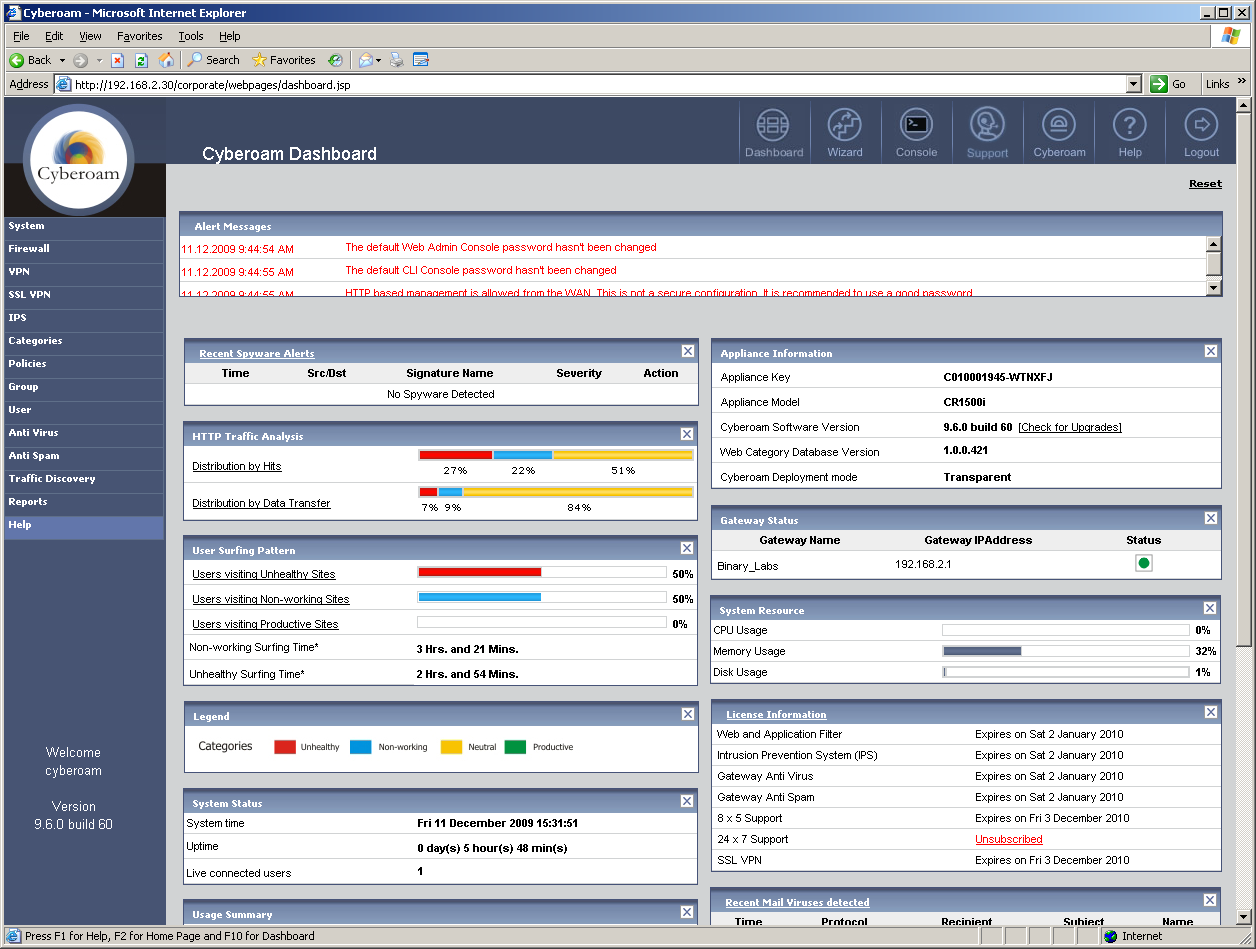
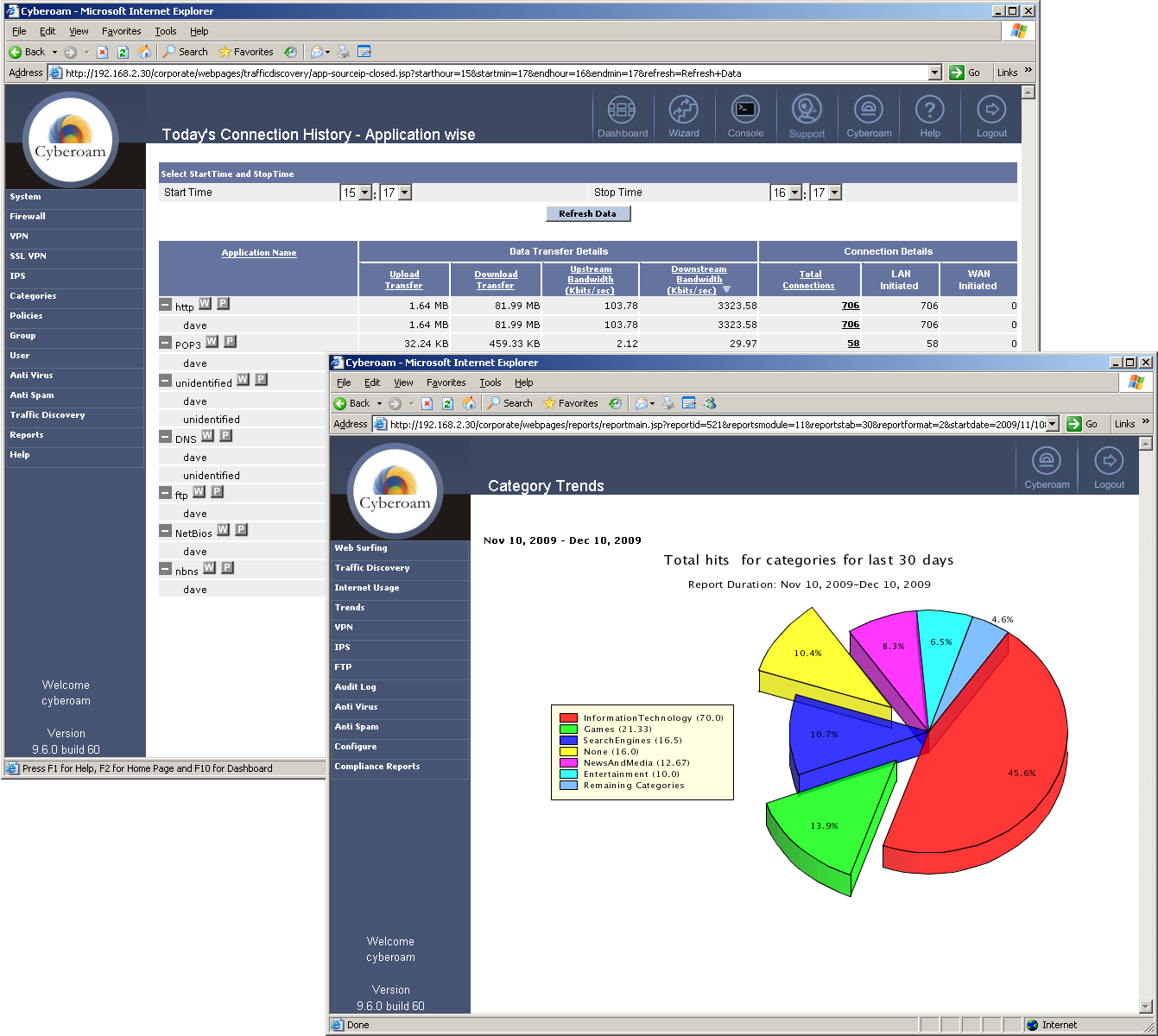
As a UTM appliance, the CR1500i ticks a lot of boxes. It offers firewalling and IPsec VPNs as standard and to these you can add options including anti-virus, anti-spam, IPS, filtering for web content and applications plus SSL VPNs.
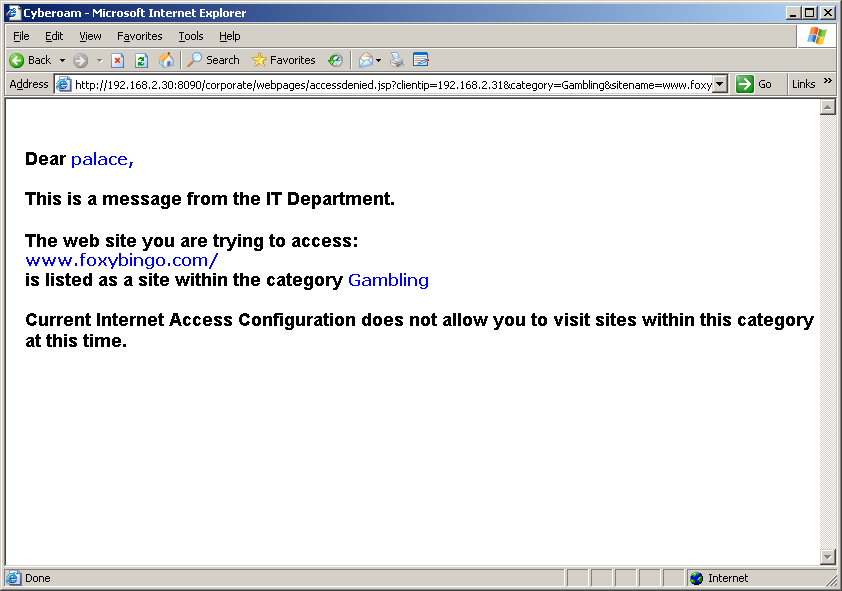
A key feature is Cyberoam's identity based UTM security which allows you to tie policies to users rather than systems. This isn't a new concept by any means but Cyberoam goes one step beyond the majority as it can apply a wider range of controls within its firewall rules to specific users and groups.
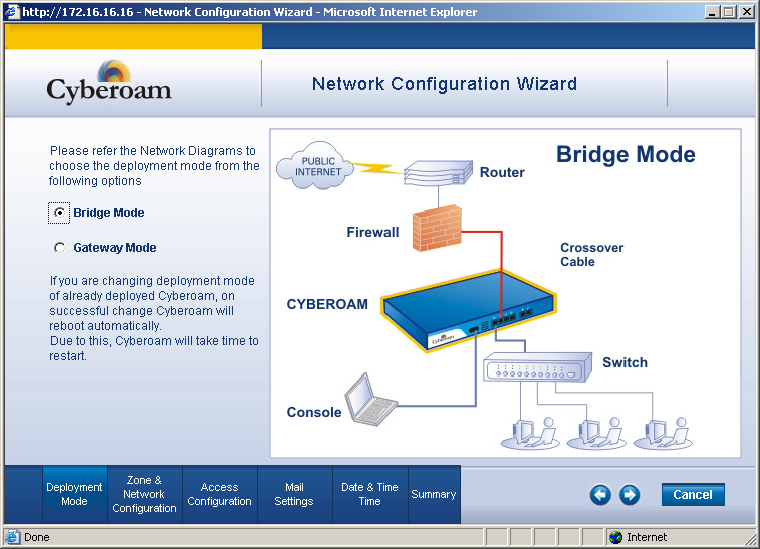
The appliance offers a reasonable specification and you have plenty of port permutations to play with as all twelve are the Gigabit variety with two of them accepting SFPs for fibre connections. For all ports you can choose individually between LAN, WAN or DMZ duties and you can deploy the appliance in routed or transparent bridge modes although the latter doesn't support Cyberoam's optional SSL VPNs.
Installation in the lab was a smooth process and we opted for transparent mode where we dropped the appliance behind our existing firewall. The main web interface is a tidy affair and on first contact you're greeted by a wizard which helps set up the bridged or transparent modes. You can also start off in passive mode or apply a default security policy to all traffic.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do that
CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do thatNews The incident at CISA raises yet more concerns about the rise of ‘shadow AI’ and data protection risks
By Ross Kelly Published
-
 Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documents
Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documentsNews Linwei Ding told Chinese investors he could build a world-class supercomputer
By Emma Woollacott Published
-
 OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anway
OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anwayNews OpenAI has confirmed plans to retire its popular GPT-4o model in February, citing increased uptake of its newer GPT-5 model range.
By Ross Kelly Published
