What is cloud computing?
It's the buzz word of the year, but what does cloud computing actually mean? And, more importantly, what opportunities, benefits and challenges does the new model offer businesses?
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
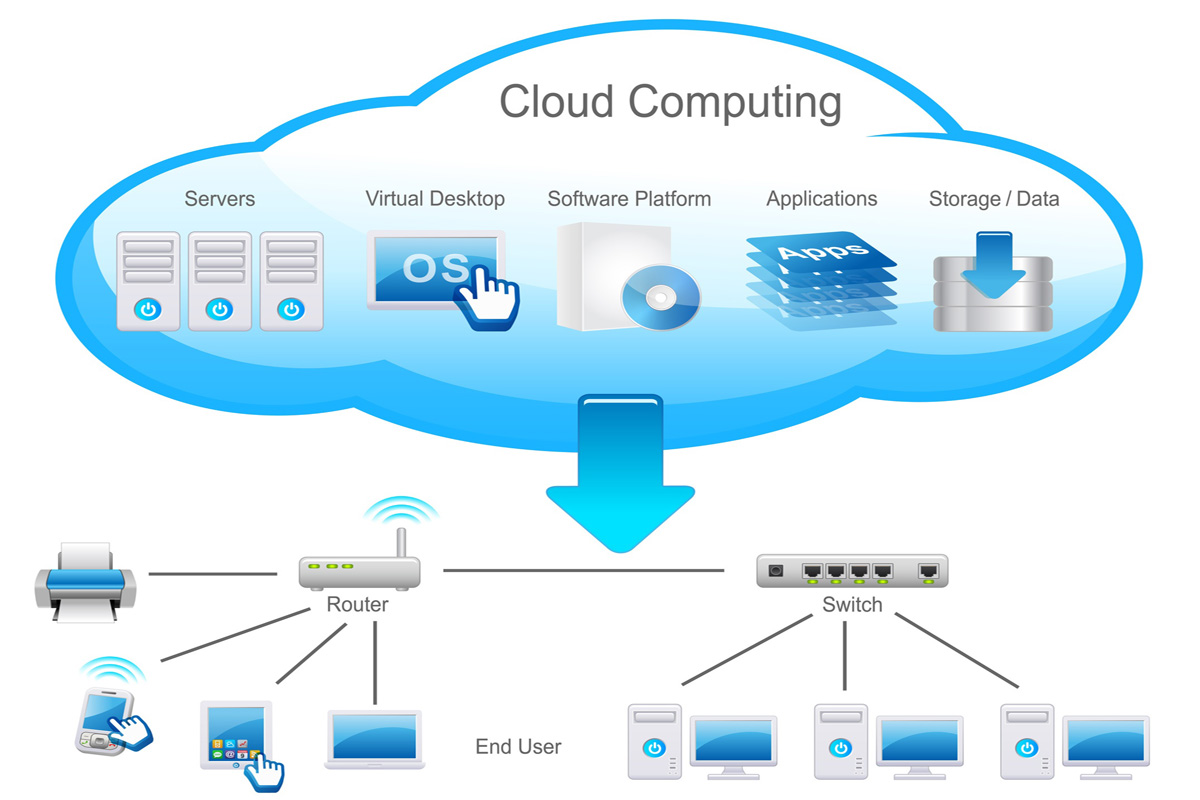
"The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software including operating systems and applications." Examples include Amazon's EC2 cloud platform.
Businesses may well be using some, or all, of these services already. Hosted Microsoft Exchange email or hosted SharePoint services, Google's Docs product and software as a service applications - of which Salesforce.com is perhaps the best known - show the range of services on offer through the cloud.
Increasingly, cloud computing is being used as a byword for bought-in IT services that stop short of full outsourcing deals, involving long-term contracts and the transfer of equipment or staff.
In practice, cloud computing can be defined as technology including software and hardware that is owned by others, run remotely from the end-user business, and paid for through a flexible contract.
That pricing model could either be a subscription, per user, per month, or a form of pricing based on IT capacity or even transactions. Consumer services such as Mozy, an online backup service, have already set an example for this, by charging end users per gigabyte of storage they rent.
The cloud in practice
Inevitably, definitions will star to blur, as businesses, and vendors, put the emerging infrastructure to new uses. One business might well use a cloud service to provide a service, in turn, to others; there are already examples of companies building suites of hosted applications, using cloud technologies, for vertical markets such as law firms or estate agency.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
At the other end of the spectrum, large enterprises and public sector bodies are going about creating their own, private versions of cloud computing. These use many of the same technology building blocks as public clouds, and even some of the same economic models, through internal charge-back mechanisms.
By putting cloud computing infrastructure behind the firewall and within the control of the IT department, some of the difficulties around security, privacy and data ownership are overcome.
-
 Sumo Logic expands European footprint with AWS Sovereign Cloud deal
Sumo Logic expands European footprint with AWS Sovereign Cloud dealNews The vendor is extending its AI-powered security platform to the AWS European Sovereign Cloud and Swiss Data Center
-
 Going all-in on digital sovereignty
Going all-in on digital sovereigntyITPro Podcast Geopolitical uncertainty is intensifying public and private sector focus on true sovereign workloads