Have we reached the cyber crime saturation point?
With discussions of an ever increasing threat lanscape, it might sound wrong, but it appears we've reached a saturation point with security incidents. That doesn't mean it's time to relax though...


ANALYSIS: A rather interesting blog post came out of Symantec this week.
It made a statement that simultaneously appeared to go against the run of play in the security sphere, and yet made perfect sense.
In the post, Symantec researcher Kevin Haley claimed we have reached a "saturation point" with security incidents.
"The bad guys just can't pump out new malware any faster. Check out the Norton Cybercrime Index. The trends for 2011 are pretty much flat," he said.
"The explosive growth in malware we've seen in the previous 10 years is just not sustainable. Maybe new hacker tools will come along, new propagation methods, or more platforms, or more people to infect. But for now, things are beginning to stagnate."
So have we really hit saturation point?
Dreaming of a data breach deluge?
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Given the slew of security breaches which have seen in 2011 already, these sentiments might seem a little odd.
There's been Sony, RSA and Citigroup, alongside the numerous hits made by LulzSec and Anonymous on both Government bodies and private organisations. Games companies have taken an absolute pounding, in particular.
Security professionals seem to think more attacks are coming their way too. During a briefing with HP this week, the tech giant revealed survey results from InfoSecurity 2011 showing an overwhelming 81 per cent expecting attack frequency to rise.
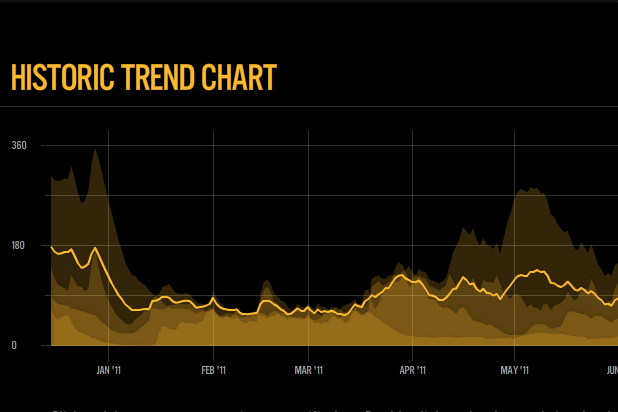
That bright yellow line tells you all you need to know - levels are pretty flat. The index takes into account all kinds of different attacks, including fraud, identity theft, malware and spam. You can check out the index for yourself here.
There is a simple explanation for the dichotomy of the increasing prominence of breaches in the media and the stabilisation in growth of incidents: attacks are becoming more noticeable, whilst not growing in frequency.
"How to explain the nearly endless parade of security incidents we've seen in the last few weeks? Well, in some ways, these are the puddles forming on the ground. It's not that rain has gotten harder," Haley explained.
"It's just that the ground has stopped absorbing them all. Some of what we are seeing does reflect the bad guys attacking new platforms and finding new people to infect. But it's mainly puddles."
Slower growth rates for threats started emerging last year. A Panda Security report from November showed the growth rate of new threats was in decline, finding from 2003 new threats had increased at a rate of 100 per cent or more. But by that point in 2010, the rate of growth was around 50 per cent.
Now in mid-2011, growth has declined even further. We are indeed at saturation point.
Houston, we have still got a problem
So if security incident levels are stagnating, we can start relaxing a little, right? Obviously not. In fact, companies should be more afraid than they have ever been.
The reason why we have hit saturation point is we are now at a peak for malware growth and incident occurrence. That means things are bad. It would be more appropriate to call it a nadir than a zenith.
Businesses still face an insane amount of threats today. As recently pointed out by our friends over at PC Pro, we might even be living in the golden age of hacking.
It's now easier than ever to make money from hacking, especially given the range of tools freely available on the web designed to simplify the process of stealing data from businesses. ZScaler research this week showed multi-function exploit kits were increasingly being used to carry out online attacks.
Automated tools like the infamous Blackhole and Eleonore exploit kits make it easy for hackers to carry out frequent and effective attacks, without the need for much IT expertise at all.
You can even rent botnets for a fairly small amount of money, as highlighted by a case in Germany, which came to a conclusion this week. A Frankfurt man was sent to jail after being found guilty of extorting gambling sites in the run up to the World Cup in 2010.
He threatened the gambling sites with distributed denial of service (DDoS) attacks if they failed to give him money, which three actually did. How was he able to back up his DDoS claims? The man rented a botnet for just $65 a day.
Oh and then there's the really sophisticated hackers who are able to infiltrate some of the biggest corporations in the world. Targeted attacks are clearly proving effective even against business giants, so don't think your company is any more secure.
The present and future risk
"There won't necessarily be an increase in the number of attacks, but an increase in the effect of attacks," Simon Leech, EMEA technical director for HP Tippingpoint, told IT Pro.
"Around 10 years ago, attacks were being used just to crash a system. The same people who did those have progressed to not just crash a system but steal your money."
Furthermore, Leech believes the plateau we've reached now will not be around for long either. So the apparent peak of today might be surpassed someday.
"I think the number of attacks will go up as well, but it's going to be the significance of the attacks that really changes," he added.
And although it appears we have indeed reached saturation point, one area remains a truly growing concern: hacktivism.
As expected, hacktivist groups have really upped their game this year, going after all kinds of businesses.
LulzSec has proven in just one month that the need for companies to reassess their security is greater than ever. So the message remains the same: stay aware and stay protected.
Tom Brewster is currently an associate editor at Forbes and an award-winning journalist who covers cyber security, surveillance, and privacy. Starting his career at ITPro as a staff writer and working up to a senior staff writer role, Tom has been covering the tech industry for more than ten years and is considered one of the leading journalists in his specialism.
He is a proud alum of the University of Sheffield where he secured an undergraduate degree in English Literature before undertaking a certification from General Assembly in web development.
-
 Meta's huge capex spree shows it's struggling to keep pace with Google and OpenAI
Meta's huge capex spree shows it's struggling to keep pace with Google and OpenAINews Meta CEO Mark Zuckerberg promises new models this year "will be good" as the tech giant looks to catch up in the AI race
-
 The open source ecosystem is booming thanks to AI, but hackers are taking advantage
The open source ecosystem is booming thanks to AI, but hackers are taking advantageNews Analysis by Sonatype found that AI is giving attackers new opportunities to target victims
-
 Power stations under attack from long-running hacking campaign
Power stations under attack from long-running hacking campaignNews Dragonfly threat group is ramping up activities, say researchers
-
 Symantec profits surge as firms prop up their cyber defences
Symantec profits surge as firms prop up their cyber defencesNews The company also announced plans to sell its web certificate business
-
 Symantec to pay $4.65 billion to acquire Blue Coat
Symantec to pay $4.65 billion to acquire Blue CoatNews Greg Clark to become Symantec CEO, promising new cloud security
-
 Symantec ditches reseller guilty of scamming PC users
Symantec ditches reseller guilty of scamming PC usersNews Silurian told people they had malware, then sold them Norton Antivirus for $249
-
 NATO builds up cyber alliance with Symantec tie-in
NATO builds up cyber alliance with Symantec tie-inNews Military industrial link up to fight cyber attacks
-
 Junk emails fall to their lowest rate in 12 years
Junk emails fall to their lowest rate in 12 yearsNews Spam is dropping, says Symantec, but other malware threats are on the rise
-
 Kaspersky: "We have never been asked to whitelist malware"
Kaspersky: "We have never been asked to whitelist malware"News A company blog has revealed neither government nor any other entity has asked it to stop detecting malware
-
 Symantec confirms split into separate security & storage entities
Symantec confirms split into separate security & storage entitiesNews Storage and security will be separated as Symantec tries to boost sales in both
