Malicous spam hits ‘epic’ levels
This month has seen a serious rise in malicious spam, according to M86 data.

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
The spammers have returned with a vengeance as malicious spam hit "epic" levels in August, according to security experts.
M86 Security said it saw a "huge surge" in malicious spam which has far exceeded anything it has seen in the past two years.
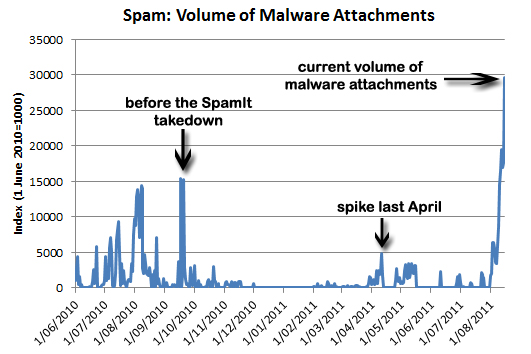
The majority of the spam was put out by the notorious Cutwail botnet, with the Festi and Asprox botnets showing themselves to be significant contributors too.
Last week, 13 per cent of the overall spam volume consisted of malicious spam, marking an "unusual" jump, according to M86. On Monday, that proportion increased to 24 per cent.
"Four of the campaigns, which we identified as originating from the Cutwail botnet are mostly recycled spam themes Fedex, credit card, changelogs and invoices," M86 explained in a blog post.
"The malware is attached within a compressed ZIP archive and is a Trojan that downloads additional malware including Fake AV, SpyEye and the Cutwail spambot itself."
Spammers used typical tricks, such as telling users there credit card had been blocked, promising more information in an attached file. Anyone opening the attachment would risk infecting their machines.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
It seems spammers have returned from a holiday break and are enthusiastically back to work.
Other spam offered rebates on purported accidental charges from hotels, as well as messages appearing to confirm UPS deliveries.
"This is an epic amount of malicious spam. After multiple recent botnet takedowns, cyber criminal groups remain resilient, clearly looking to build their botnets and distribute more fake AV in the process," M86 added.
"It seems spammers have returned from a holiday break and are enthusiastically back to work."
Spam had seen a significant drop earlier this year, largely thanks to a Microsoft-led operation taking on the Rustock super spammer botnet.
Tom Brewster is currently an associate editor at Forbes and an award-winning journalist who covers cyber security, surveillance, and privacy. Starting his career at ITPro as a staff writer and working up to a senior staff writer role, Tom has been covering the tech industry for more than ten years and is considered one of the leading journalists in his specialism.
He is a proud alum of the University of Sheffield where he secured an undergraduate degree in English Literature before undertaking a certification from General Assembly in web development.
-
 Anthropic promises ‘Opus-level’ reasoning with new Claude Sonnet 4.6 model
Anthropic promises ‘Opus-level’ reasoning with new Claude Sonnet 4.6 modelNews The latest addition to the Claude family is explicitly intended to power AI agents, with pricing and capabilities designed to attract enterprise attention
-
 Researchers call on password managers to beef up defenses
Researchers call on password managers to beef up defensesNews Analysts at ETH Zurich called for cryptographic standard improvements after a host of password managers were found lacking
-
 Europol hails triple takedown with Rhadamanthys, VenomRAT, and Elysium sting operations
Europol hails triple takedown with Rhadamanthys, VenomRAT, and Elysium sting operationsNews The Rhadamanthys infostealer operation is one of the latest victims of Europol's Operation Endgame, with more than a thousand servers taken down
-
 Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up sting
Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up stingNews Europol has detained several people believed to be involved in a botnet operation as part of a follow-up to a major takedown last year.
-
 Horabot campaign targeted businesses for more than two years before finally being discovered
Horabot campaign targeted businesses for more than two years before finally being discoveredNews The newly-discovered Horabot botnet has attacked companies in the accounting, investment, and construction sectors in particular
-
 Brand-new Emotet campaign socially engineers its way from detection
Brand-new Emotet campaign socially engineers its way from detectionNews This latest resurgence follows a three-month hiatus and tricks users into re-enabling dangerous VBA macros
-
 Microsoft says “it’s just too difficult” to effectively disrupt ransomware
Microsoft says “it’s just too difficult” to effectively disrupt ransomwareNews The company details its new approach to combatting cyber crime as the underground industry drains $6 trillion from the global economy
-
 Beating the bad bots: Six ways to identify and block spam traffic
Beating the bad bots: Six ways to identify and block spam trafficIn-depth Not all traffic is good. Learn how to prevent bad bots from overrunning your website
-
 Ukraine's vigilante IT army now has a DDoS bot to automate attacks against Russia
Ukraine's vigilante IT army now has a DDoS bot to automate attacks against RussiaNews The 270,000-strong IT Army of Ukraine will now combine supporters' cloud infrastructure to strengthen the daily attacks against their invaders
-
 Microsoft's secure VBA macro rules already being bypassed by hackers
Microsoft's secure VBA macro rules already being bypassed by hackersNews Recent analysis of Emotet activity has revealed a shift away from malicious Office documents to drop malware
