FaceTime Communications USG-1030 review
Social networking in the workplace presents a real dilemma for businesses as it has both benefits and drawbacks. FaceTime’s USG appliance has a unique way of managing access. Read this exclusive review to find out if you really can have the best of both worlds.
FaceTime’s USG appliances allow businesses to permit access to social networks in the workplace, but with strict controls and monitoring in place. IM and P2P apps also get the same treatment and adding in the versatile URL and true web content filtering makes this security appliance far more sophisticated, albeit a lot more expensive, than standard UTM appliances.


FaceTime USG-1030
With a USG appliance on the network you’ll soon find out what your employees are up to.
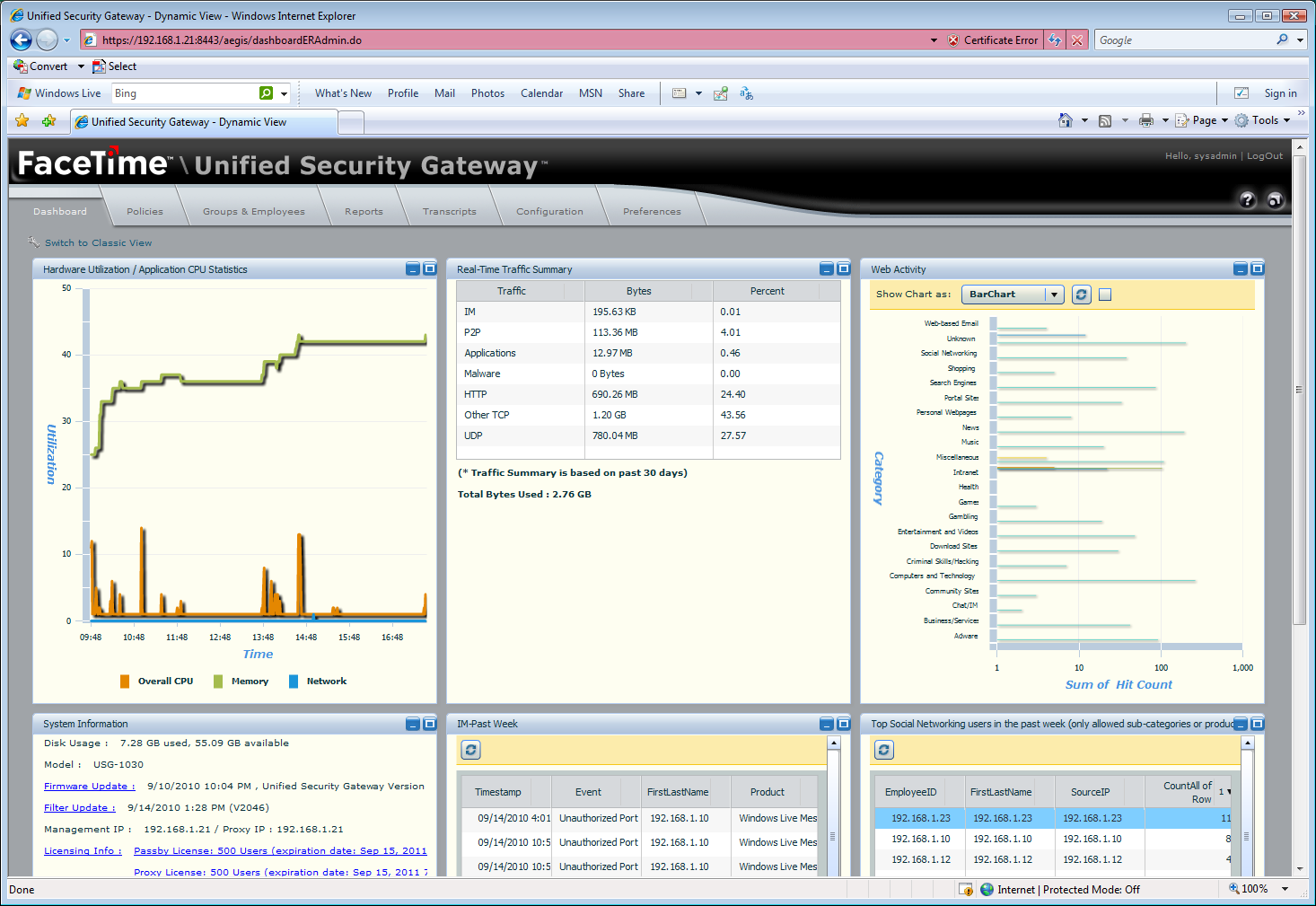
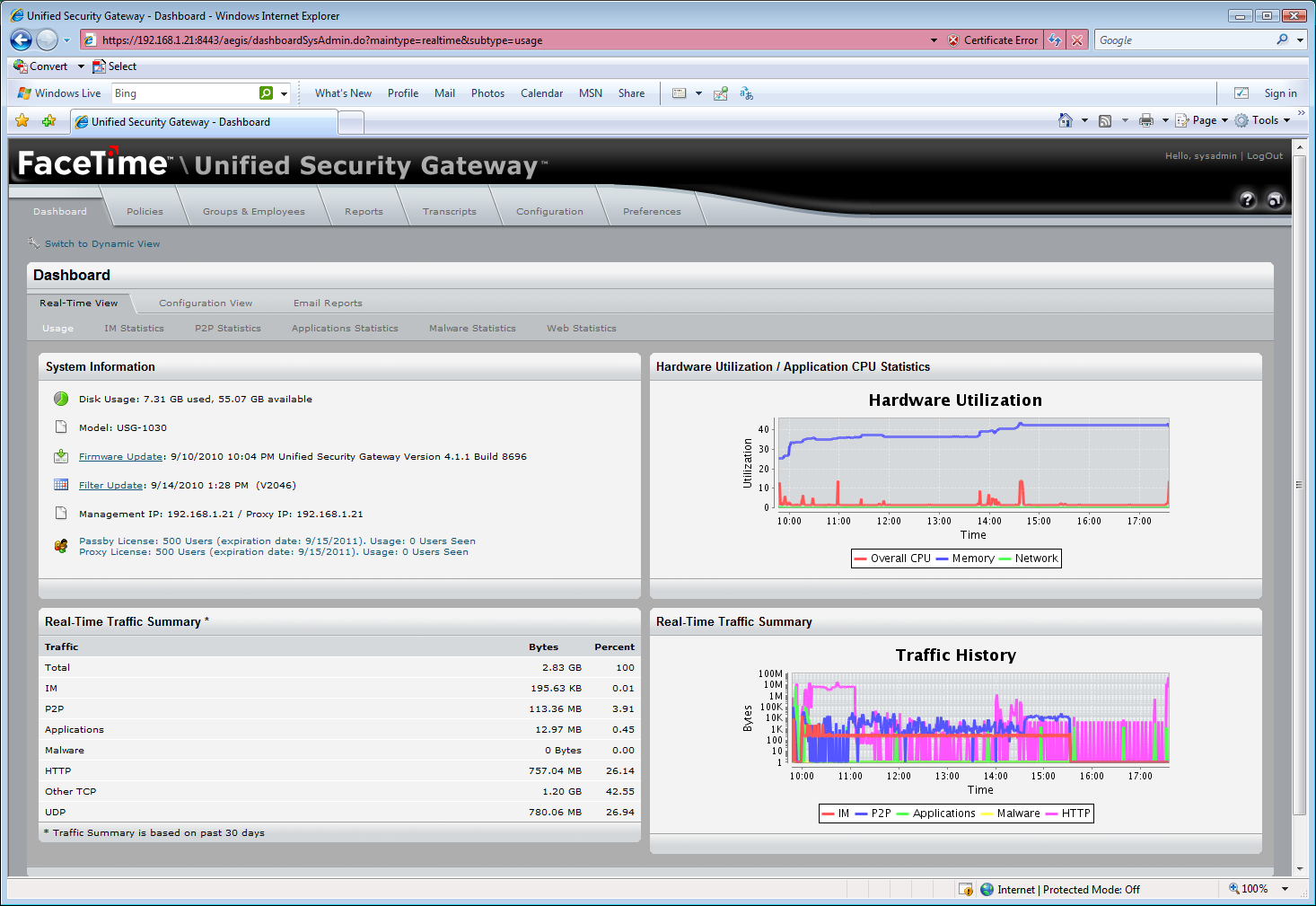
The new dynamic dashboard provides Flash-based real-time views of network activity.
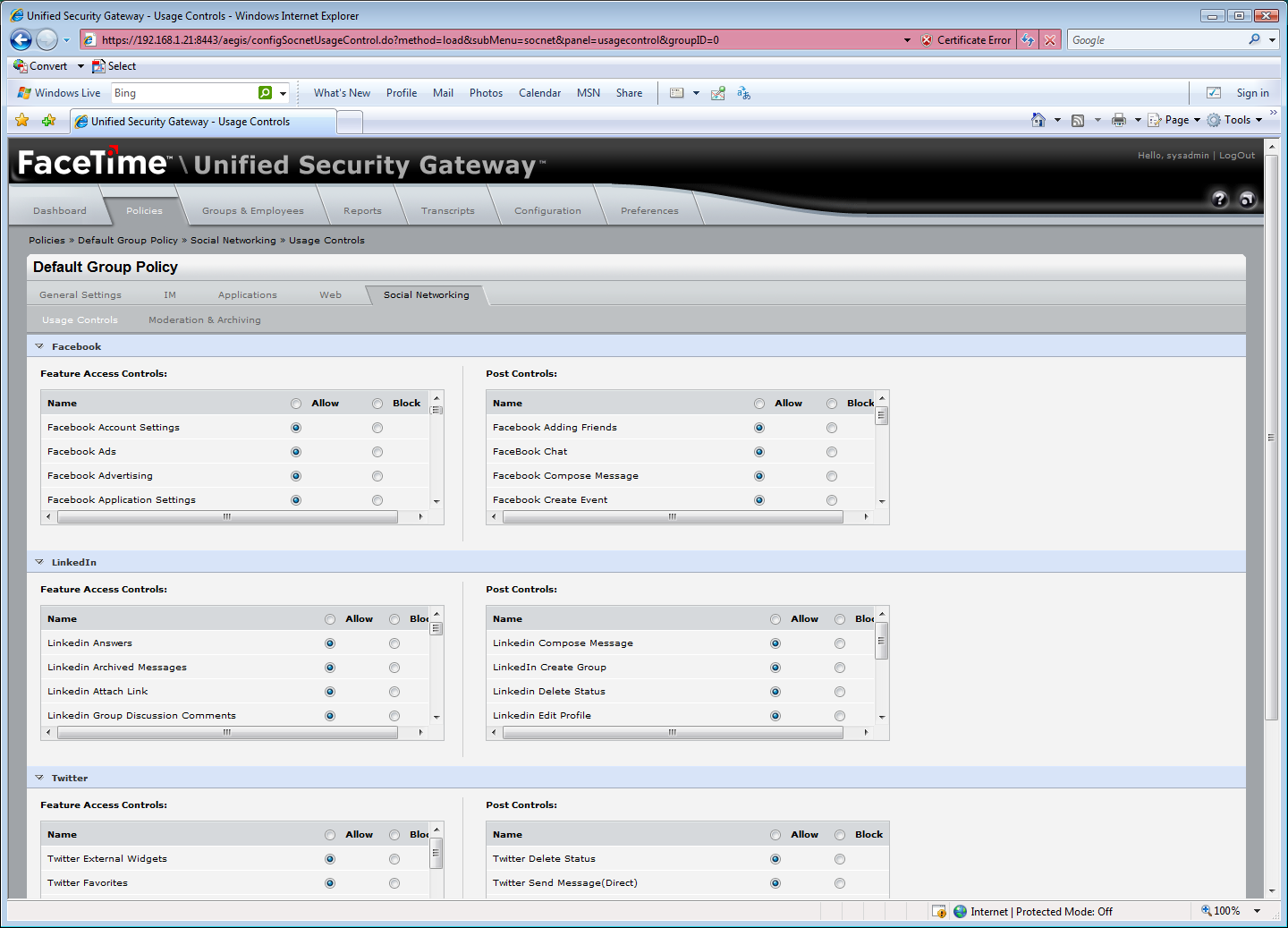
FaceTime’s new Socialite module provides excellent levels of control for Facebook, LinkedIn and Twitter.
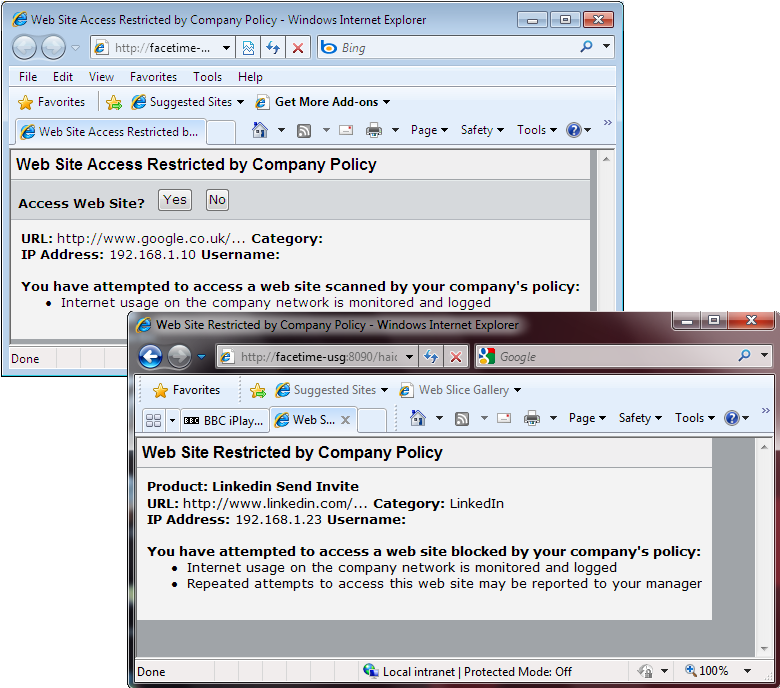
We were able to send AUP agreements to users and control what LinkedIn activities they could access.
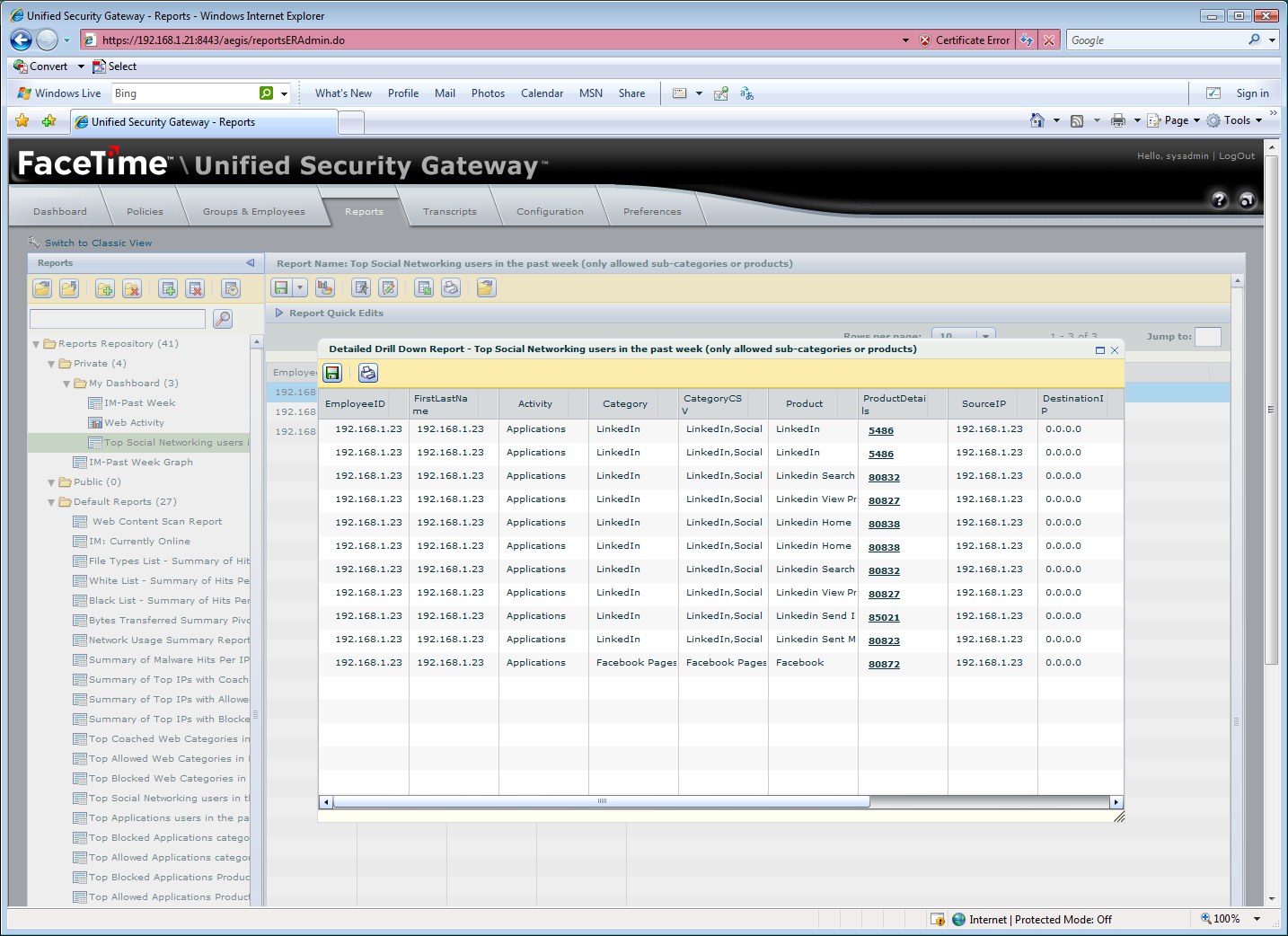
Dynamic reports provide plenty of information about activities and can be easily customised to suit.
There are clear benefits to using social networking for business purposes, but allowing employees to have uncontrolled access in the workplace is asking for trouble. Facebook and Twitter alone can pose serious threats to security. Although businesses can create acceptable use policies (AUPs), actually enforcing them is another matter.
The problem with most Unified Threat Management (UTM) appliances is they can only control access to these types of sites via their URL category filtering capabilities which means all access is either blocked or allowed. FaceTimes Unified Security Gateway (USG) appliances are much smarter as they can control access at a more granular level.
In this exclusive review we look at the top of the range USG-1030 which is delivered as a well specified Dell rack server with enough grunt to handle up to 10,000 users. Smaller models are available with the USG-530 handling up to 7,000 users, the USG-320 good for up to 2,500 users and the entry-level USG-220 suited for SMBs of up to 500 users.

The appliances introduce FaceTime's new Socialite feature (a nauseatingly clever acronym for social: IT enabled) which focuses on controlling access to Facebook, LinkedIn and Twitter. This is an optional module which allows you to strictly control what activities on these sites employees can use. There's also a SaaS deployment option for Socialite which extends these controls to remote workers.
All access is controlled using security policies which can be applied to AD users and groups or individual IP addresses and ranges. We were impressed with the Socialite features as they allowed us to control virtually every aspect of Facebook.
Nearly fifty settings are provided for Facebook allowing you to control access to a wide range of features including account and application settings, installing and playing games, searching for friends and watching video. After users have logged in you can apply plenty of post control settings such as blocking postings, chat and friends lists. The contents of posts can be logged for compliance purposes. It's also possible to restrict access to a single corporate Facebook account and require that all posts are approved by a moderator before going live.
Using our live LinkedIn account for testing we found the levels of control equally impressive as we could block access to functions such as company and job searches, posting messages and sending invitations. With the latter function blocked we received a warning web page from the USG when we tried to send an invitation.
There's much more to the USG appliances as they offer optional controls for IM and P2P apps, URL category and web content filtering plus anti-spyware and anti-virus. More new features have been introduced as the appliances can now run the Squid web proxy cache locally, enforce Safe Search options for Google, Yahoo and Bing and support ISA proxy servers.
There are 55 categories of URLS to block or allow - a useful feature is the option to send an AUP agreement page to a user when they first try to access the Internet. FaceTime's content scanning adds a new dimension to web access control as the USG can be set to look for specific words or phrases in web pages.
This can also be applied to the contents of documents, text files and archives and you can opt to scan inbound and outbound traffic. Lexicons of word categories are provided and options are available to passively monitor web access, block access if a scan policy is triggered and send alerts. So, for example, you can prevent sensitive data from leaking out by restricting what documents be sent as attachments using webmail based on their content.
We found deployment in the lab a swift process as one of the USG's Gigabit Ethernet ports is used to monitor all network traffic via a span port on a switch. A second port on the USG is used to deploy FaceTime's IM proxy which provides greater levels of control as it allows the USG to analyse all IM activity in real time, check for banned words and phrases and issue challenges when users attempt to send messages.
Layer 7 packet inspection is used to identify the various applications and can be initially left to run in a passive discovery mode. At this stage most businesses will be quite shocked when they see what's running around their network.
The web console provides a complete summary of all activities separated out under categories for IM, P2P, applications, web usage and malware. Within minutes the USG had spotted systems on our test network running the BitTorrent client Vuze, the BBC's iPlayer downloader, the iTunes client, remote control apps including GoToMyPC and Windows Live Messenger.
The classic dashboard view provides colour coded graphs showing network activity for all categories along with statistics for each component and quick access to the latest reports. The main console has been updated with a new dynamic Flash-based view which provides a graph of appliance utilisation and a couple of tables showing general network activity.
Three more graphs or tables can be added to the dynamic view and each moved around using drag and drop. However, during testing we found ourselves regularly returning to the classic view as we found it far more informative and intuitive.
FaceTime's new dynamic reports allow you to gather even more information about user activity including web usage, IM proxy activity and content scanning. You have a base set of predefined reports which can be displayed as tables or graphs and exported to PDF and Excel formats.
Each report can be copied, pasted and customised to suit and three of these can be dropped into a special folder where they are shown in the dynamic real-time view page. The classic report view is still provided which offers separate categories for IM, P2P, malware, applications and web access and a base set of predefined reports for each one.
Many businesses are finding themselves between a rock and hard place as employees are now demanding access to social networking in the workplace. To avoid security risks these activities need to be subject to enforceable AUPs and FaceTime is in a unique position as there is nothing else on the market with the same levels of control as its USG appliances.
Verdict
FaceTime’s USG appliances allow businesses to permit access to social networks in the workplace, but with strict controls and monitoring in place. IM and P2P apps also get the same treatment and adding in the versatile URL and true web content filtering makes this security appliance far more sophisticated, albeit a lot more expensive, than standard UTM appliances.
Chassis: Dell PowerEdge R410 1U rack server Processor: 2 x 2.93GHz Intel Xeon X5570 Memory: 6GB 1333MHz DDR3 Storage: 2 x 1TB 7.2k SAS drives in RAID-1 mirror RAID: Dell SAS6/iR controller Network: 3 x Gigabit Ethernet Power: 2 x 500W hot-plug supplies Management: Web browser
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Stansted IT glitch causes thousands to miss their flights
Stansted IT glitch causes thousands to miss their flightsNews Eight hour outage causes chaos at UK’s fourth busiest airport
By Jane McCallion Published
-
 FBI takes down botnet exploiting aging routers
FBI takes down botnet exploiting aging routersNews Organizations warned they should replace potentially affected devices
By Emma Woollacott Published
-
 LockBit ransomware group falls victim to hackers itself
LockBit ransomware group falls victim to hackers itselfNews A data leak has revealed negotiations with victims, along with Bitcoin wallet addresses, affiliate accounts and details of attacks
By Emma Woollacott Published