Chrome malware masquerades as 'missing font' files
New hack tricks users into downloading missing fonts loaded with malicious files
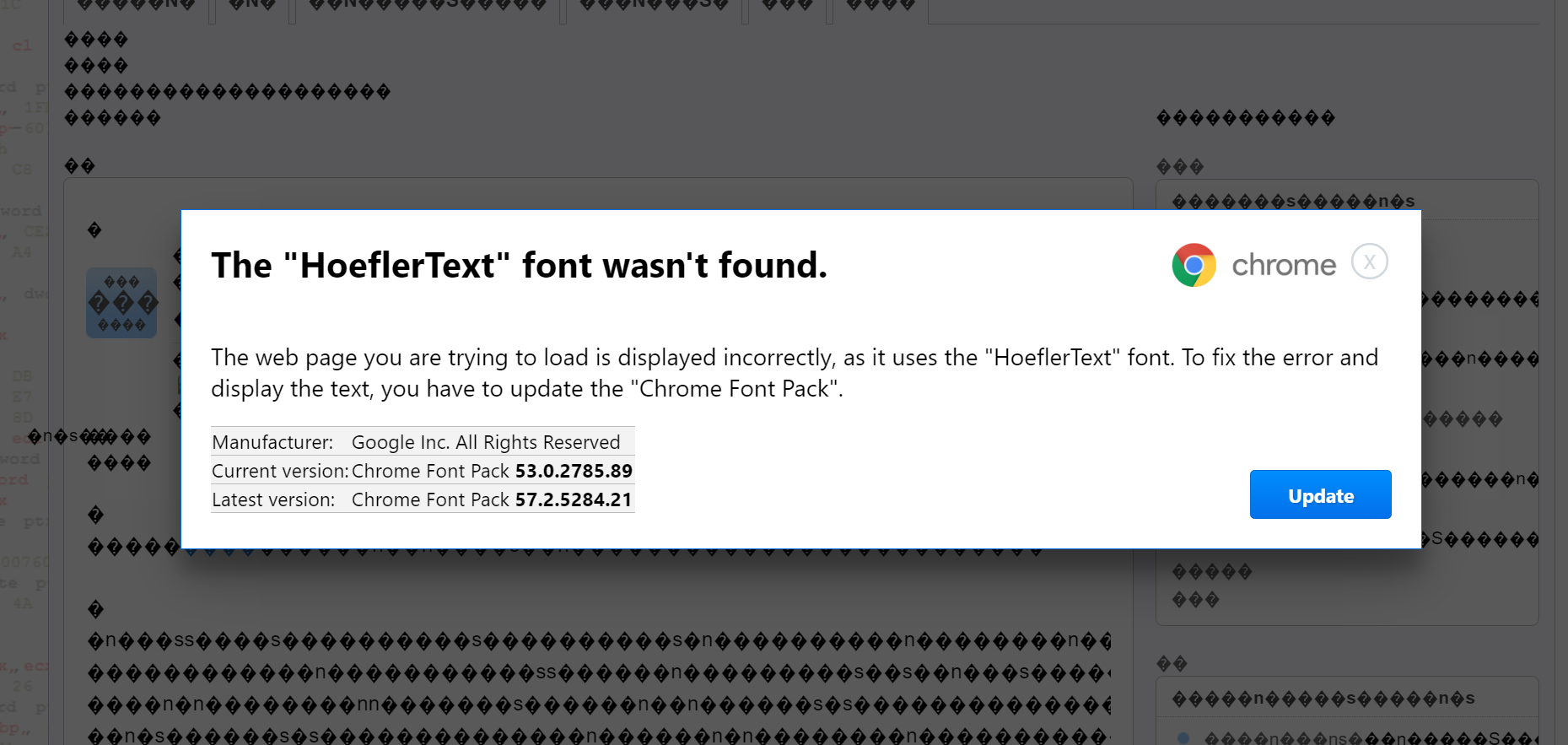
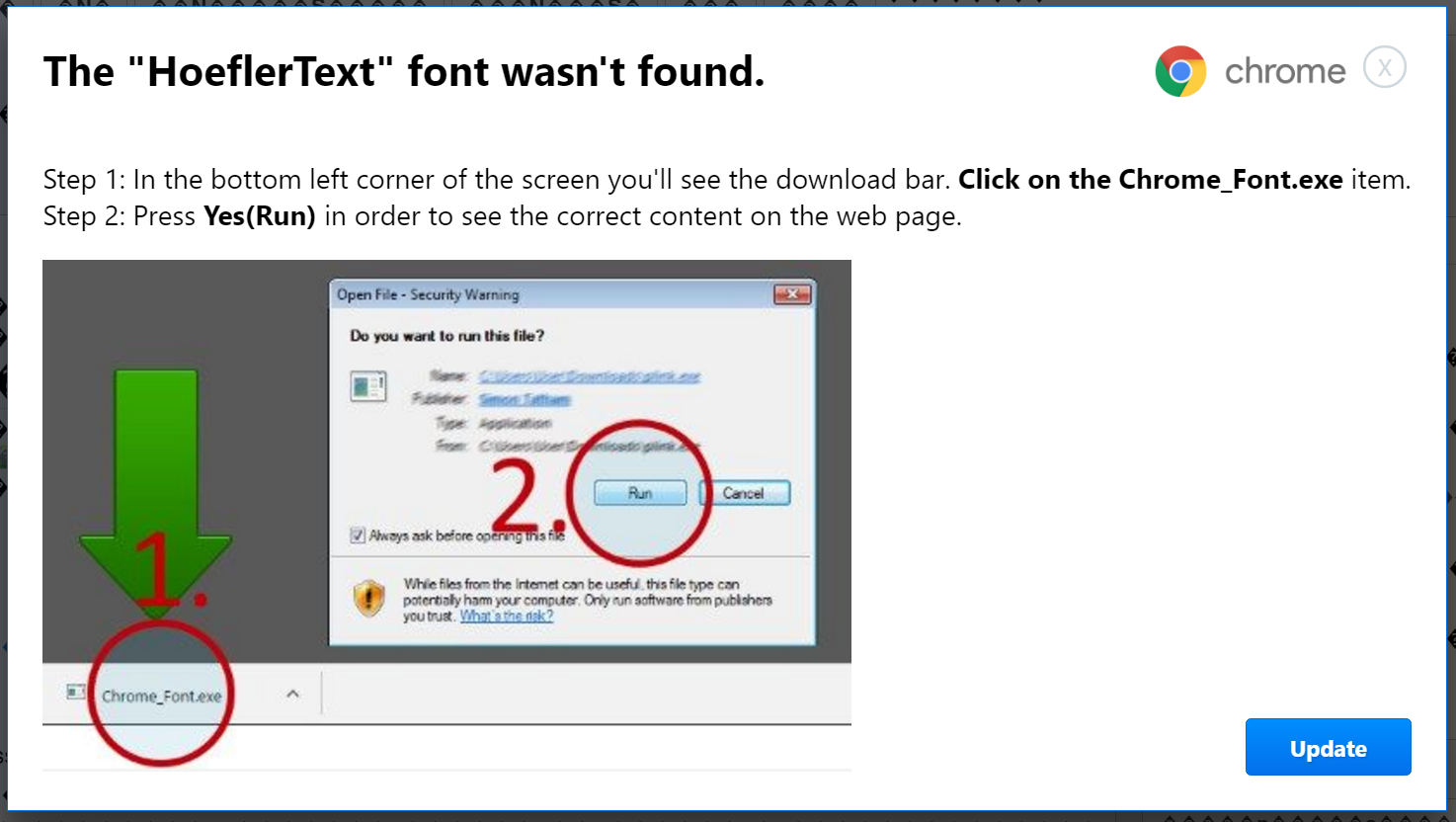
A security researcher has discovered a new hacking tactic on Google Chrome that manipulates websites into displaying missing font prompts, which then trick users into downloading malicious files.
The infection was first spotted on an unnamed WordPress website by Mahmoud Al-Qudsi, a researcher at cybersecurity firm NeoSmart Technologies, who detailed the process in a blog post.
The attack involves a hacker exploiting JavaScript to alter the rendering of content on a webpage, causing it to resemble mis-encoded text which appears as a jumble of symbols and shapes. The code then prompts the user to download the missing fonts through a Chrome language pack to decipher the text.
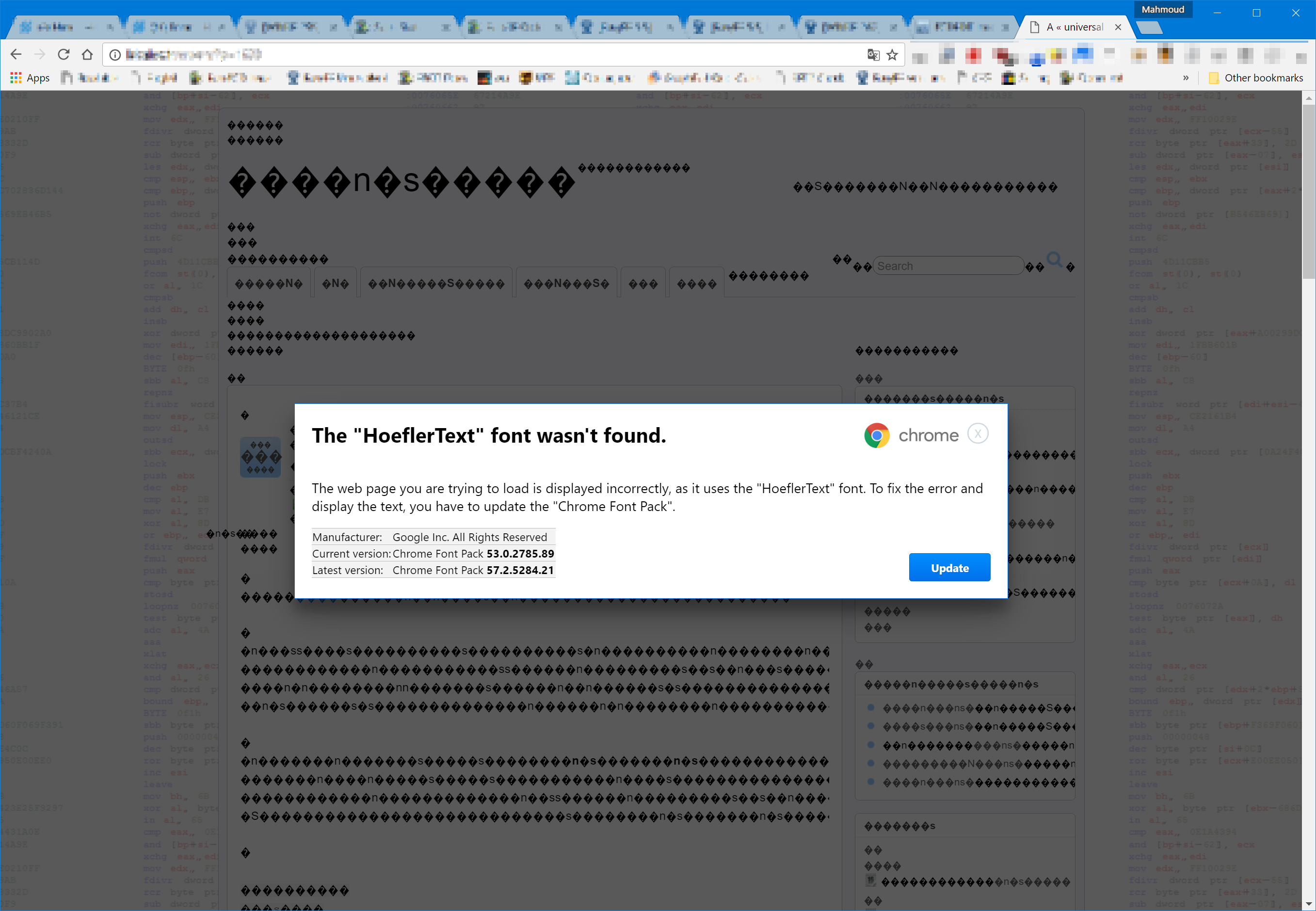
Clicking "Update" results in a file called "Chrome Font v7.5.1.exe" being downloaded and a second prompt encourages the user to run the file, all the while appearing as a perfectly safe Chrome download.
The attack is particularly well disguised and makes every attempt to appear a legitimate Chrome pop up, including the correct text formatting and right use of colours for the "Update" button.
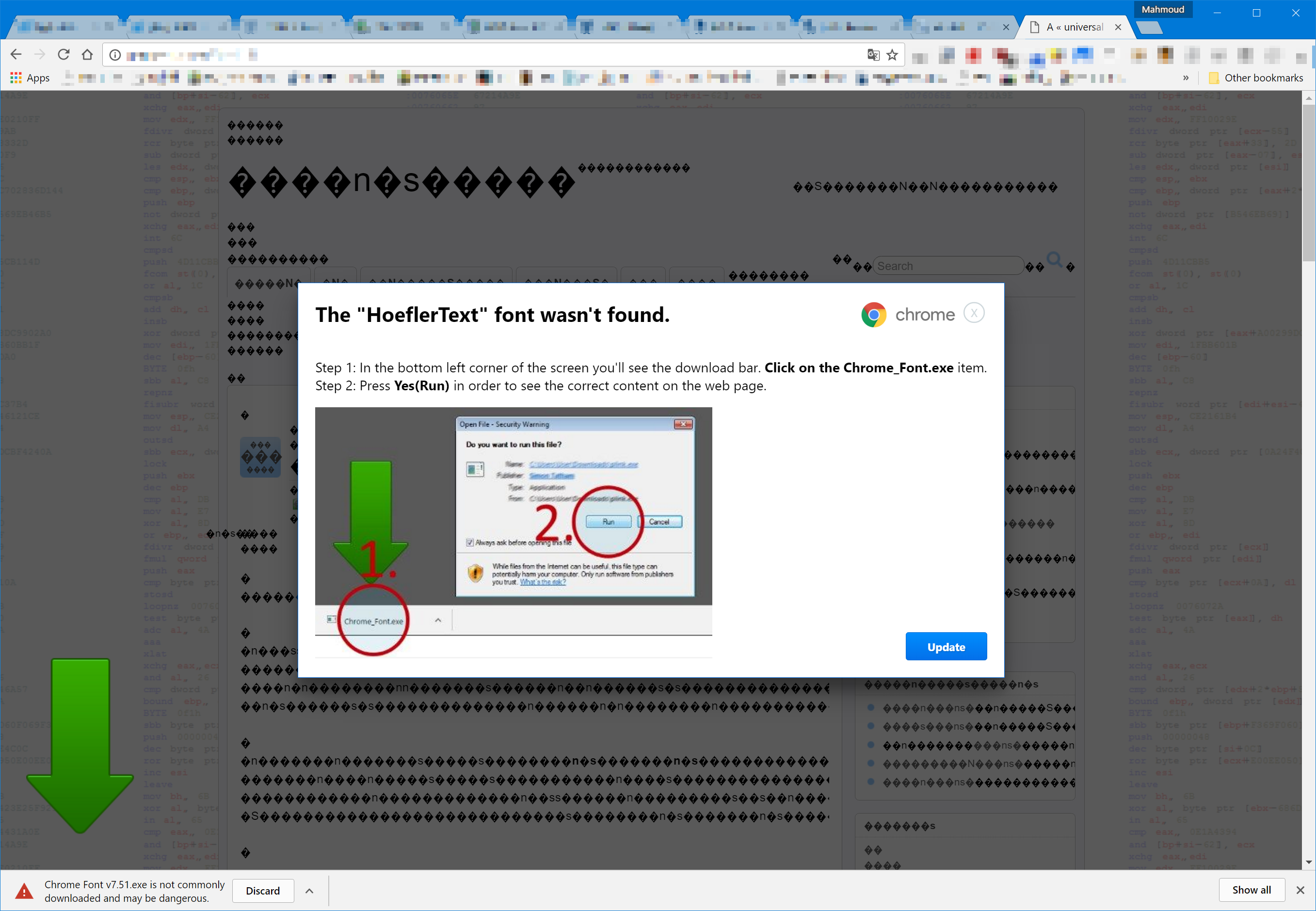
"This attack gets a lot of things right that many others fail at," said Al-Qudsi. "The premise is actually believable: the text doesn't render, and it says that it is caused by a missing font (Hoefler Text, which is a real font), which it then prompts you to download and install."
"The shape of the update button seems correct, and the spelling and grammar are definitely good enough to get a pass."
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
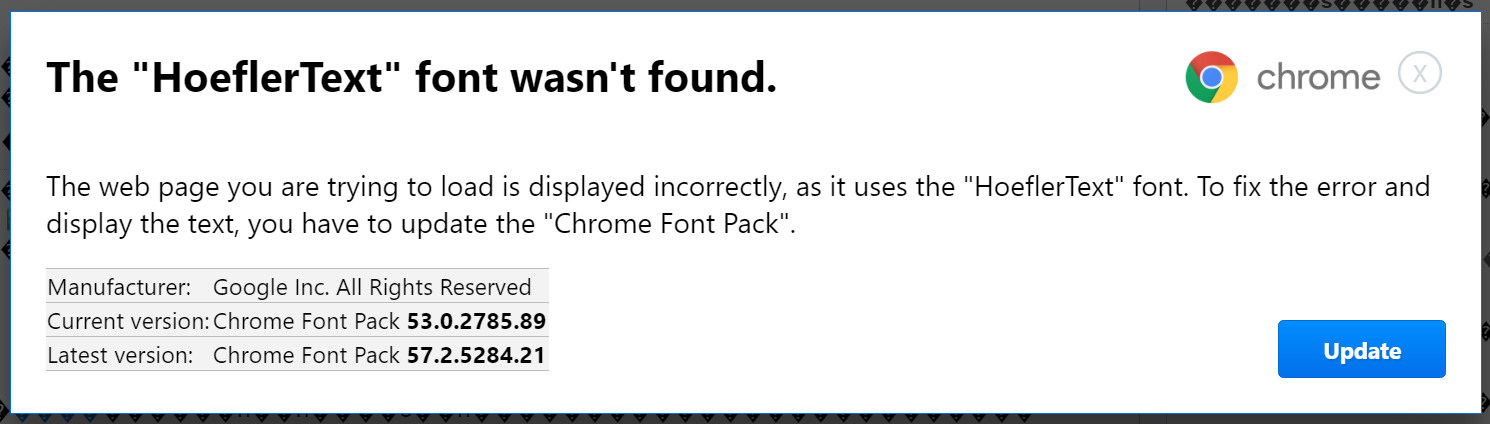
Al-Qudsi does identify some tell-tale signs that the prompt is not all as it seems. A savvy user will know what version of Chrome they are running, in this case version 56, however the prompt has version 53 hard-coded into its dialogue. It also features a rather conspicuous 'X' in the top right corner, which gives the game away, according to Al-Qudsi.
However once the file is downloaded, the quality of the scam "takes a nosedive", with text appearing blurry on prompts, and inconsistent file names for the downloaded material.
Although Chrome will notify the user with a "this file isn't downloaded very often" warning, it will not catch the download as a malicious file. It also slips by Windows Defender, and a check of virus scanning database VirusTotal reveals that only nine of 59 recorded antivirus scanners are able to correctly identify the file as malware.
Al-Qudsi has forwarded the discovery on to Google's security team, but pending an update patch, Chrome still fails to identify the file as malware. The firm advises users to be extra vigilant against these types of download prompts.
Pictures courtesy of NeoSmart
Dale Walker is a contributor specializing in cybersecurity, data protection, and IT regulations. He was the former managing editor at ITPro, as well as its sibling sites CloudPro and ChannelPro. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.
-
 Phantom firms: The rise of fraudulent cybersecurity vendors
Phantom firms: The rise of fraudulent cybersecurity vendorsIndustry Insights Channel partners need systematic vendor vetting to combat rising phantom firm scams
-
 Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"
Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"News OpenAI models and tools will now be embedded within the Snowflake Intelligence and Cortex platforms
-
 Google rolls out patch for high-severity Chrome browser zero day
Google rolls out patch for high-severity Chrome browser zero dayNews It's the eighth time this year Google has been forced to address a zero-day vulnerability in its world-leading browser
-
 Google Chrome branded the least effective browser for stopping phishing attacks
Google Chrome branded the least effective browser for stopping phishing attacksNews The world's most popular browser came dead last when compared against competitors
-
 Windows devices targeted by PuzzleMaker malware exploiting Chrome zero-day flaw
Windows devices targeted by PuzzleMaker malware exploiting Chrome zero-day flawNews Chain of vulnerabilities used to attack multiple companies worldwide
-
 Malware found on popular Facebook, Instagram and Vimeo browser extensions
Malware found on popular Facebook, Instagram and Vimeo browser extensionsNews Chrome and Edge extensions laced with malware have already been installed three million times
-
 Google sets a date for Chrome extension privacy revamp
Google sets a date for Chrome extension privacy revampNews From January 18th, developers must be clear about how they're handling user data
-
 Google looks to replace third-party cookies in two years
Google looks to replace third-party cookies in two yearsNews The online advertising market needs to shift to tracking methods that offer some user privacy, admits Google
-
 Chrome continues HTTP phase-out by removing 'secure' icon from HTTPS sites
Chrome continues HTTP phase-out by removing 'secure' icon from HTTPS sitesNews Changes in 'secure' and 'non secure' icons comprise final steps in plan to make web secure-by-default
-
 Hack on popular Chrome plugin spams ads to one million users
Hack on popular Chrome plugin spams ads to one million usersNews The author says a phishing scam led to the theft of admin credentials