Five weirdest password alternatives of all time
Computers can identify you based on your butt and your walk, not to mention your smell...


Around half of consumers would "choose anything but a traditional username and password account registration when given the option", according to identity management firm Gigya.
But would they choose these truly bizarre password alternatives that have been proposed over the years, and would your business be safer switching to them?1. Biometric Buttocks

Picture by Holgar Ellgaard
What is it?
It was, according to Professor Shigeomi Koshimizu and his team at the Advanced Institute of Industrial Technology in Tokyo, a chair that could identify whoever was sitting in it and enable a kind of sit down to log in authentication system.
How does it work?
The chair itself was fitted with 360 degree sensors that profiled the users, erm, buttocks (via Phys). Measurements including such things as your contours of your buttocks, their weight and the pressure patterns you exert as you sit down were captured in order to identify the user. If all the metrics matched the user profile, then authentication was completed. The professor claimed a 98 percent success under lab conditions.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Would it make your business more secure?
Originally intended as an anti-theft device for motor vehicles, the bum biometrics idea would surely be doomed to fail in an office environment. For one thing, if it got the login wrong twice out of every ten attempts that would soon get old. Then there's the problem of gaining a bit of weight, which would see you locked out of the network, and the resulting embarrassing tech support call. Not to mention requiring staff to allow you to measure their backsides and store the data being more than a little problematic in practice.
2. SkullConduct

What is it?
Created by researchers from the Human-Computer Interaction Group at the University of Stuttgart and the Perceptual User Interfaces Group at the Max Plank Institute for Informatics, SkullConduct is "biometric user identification using bone conduction through the skull." Literally a login system that demands you use your head to remain secure.
How does it work?
Apparently SkullConduct uses changes made to a sound wave once it has passed through bone, in this case the skull, to identify an individual user with a 97 per cent success rate under lab conditions. Why the skull? For a start every skull is sufficiently unique to enable identification, and it also lends itself to the sensors coming in the form of specially modified Google Glass devices.
Would it make your business more secure?
We can't see this working in an office environment for two reasons. Firstly, the 97 per cent success rate was under lab conditions where the environment was free of external noise. Even 97 per cent is way too low to be usable, and if normal office noise levels drop it further then it's a massive fail. Secondly, who wants to wear Google Glasses at work?3. The e-Nose
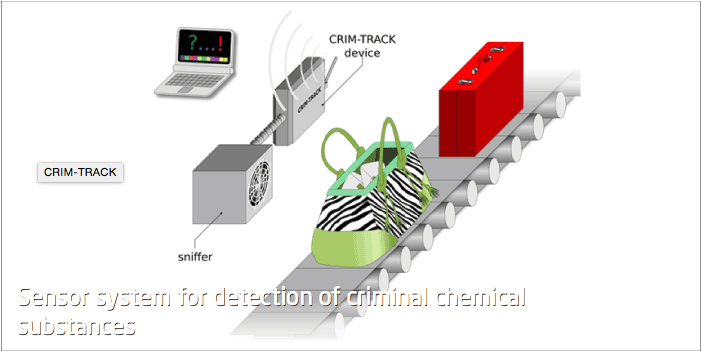
Crim-Track is a project to create a portable "sniffer"
What is it?
Everyone smells, and more to the point everyone has a different smell. Yes, we are talking body odour, and some scientists are talking about using body odour as a biometric.
How does it work?
Researchers from the Universidad Politcnica de Madrid (UPM) and a Spanish start-up called SEADM have been working on identification by smell (via Technologist). These e-Nose technologies all work in pretty much the same way; building a chemical profile of the target user and matching future scans against that. That profile, and the future scanning, is done in slightly different ways though. So while the US military via a DARPA project requires a swab from your armpit (yuck) to produce the molecular profile, the Spanish folk just need to sniff your hand. OK, they need you to put your hand in a glass jar and the machine sniffs out the chemical profile.
Would it make your business more secure?
Unfortunately, the e-Nose had failure rate of 15 percent last time we heard about it, which is far too unreliable for a business critical environment.4. Behavioural Metrics

What is it?
The military research boffins at DARPA (via Behavio Sec) have been working on something called the Active Authentication program for some years, and it essentially promises to identify an individual by measuring what they do and how they do it. In other words, using human secrets as an authentication method.
How does it work?
Rather than scan your fingerprint or eyeball, DARPA is talking about a process of continuously monitoring how you move a mouse or type on a keyboard. Everything from speed to pressure, eye movements and your overall interaction with the computer (or mobile device) are measured; including your browsing behaviour.
Other researchers are looking at similar behavioural monitoring, for smartphone touchscreen interaction, for example. These behavioural metrics wouldn't actually replace the password, or whatever login authentication method is in use, but rather ensure that whoever continues to use the device is the authorised person and not someone else.
Would it make your business more secure?
Yes, it almost certainly would given that it extends user authentication into a continuous process. The problem, however, comes with the Big Brother implications of continuous monitoring alongside practical concerns such as changes caused by injury, health matters (like failing eyesight) or even the use of a new mouse or keyboard.5. Gait Recognition

What is it?
This is how Aerosmith might choose to login, as it is based around a 'walk this way' concept. Your identity can be tied down to the way you walk, according to Japanese researchers from the Shinshu University (via the Royal Society).
How does it work?
The way that you walk is a unique identifier, it turns out. Computers are pretty good at recognising known gait patterns, so it was just a small step (pardon the pun) to incorporate this into authentication technology. What these researchers did was find that your dynamic foot pressure pattern, an indirect method of reflecting the acceleration of all body parts, is also unique. The user walks across a pressure sensitive surface, and 3D image processing captures the gait. Combining the two data sets and doing some clever processing enables a 99.6 percent success rate.
Would it make your business more secure?
It could do, from the authenticated access to a building perspective, but we can't see how this kind of technology would be transferable to network logins and the like. Plus, what happens if you sprain your ankle or turn up wearing unfeasibly high heels to work?
Davey is a three-decade veteran technology journalist specialising in cybersecurity and privacy matters and has been a Contributing Editor at PC Pro magazine since the first issue was published in 1994. He's also a Senior Contributor at Forbes, and co-founder of the Forbes Straight Talking Cyber video project that won the ‘Most Educational Content’ category at the 2021 European Cybersecurity Blogger Awards.
Davey has also picked up many other awards over the years, including the Security Serious ‘Cyber Writer of the Year’ title in 2020. As well as being the only three-time winner of the BT Security Journalist of the Year award (2006, 2008, 2010) Davey was also named BT Technology Journalist of the Year in 1996 for a forward-looking feature in PC Pro Magazine called ‘Threats to the Internet.’ In 2011 he was honoured with the Enigma Award for a lifetime contribution to IT security journalism which, thankfully, didn’t end his ongoing contributions - or his life for that matter.
You can follow Davey on Twitter @happygeek, or email him at davey@happygeek.com.
-
 What the UK's new Centre for AI Measurement means for the future of the industry
What the UK's new Centre for AI Measurement means for the future of the industryNews The project, led by the National Physical Laboratory, aims to accelerate the development of secure, transparent, and trustworthy AI technologies
-
 Meta's huge capex spree shows it's struggling to keep pace with Google and OpenAI
Meta's huge capex spree shows it's struggling to keep pace with Google and OpenAINews Meta CEO Mark Zuckerberg promises new models this year "will be good" as the tech giant looks to catch up in the AI race
-
 Thousands of exposed civil servant passwords are up for grabs online
Thousands of exposed civil servant passwords are up for grabs onlineNews While the password security failures are concerning, they pale in comparison to other nations
-
 Gen Z has a cyber hygiene problem
Gen Z has a cyber hygiene problemNews A new survey shows Gen Z is far less concerned about cybersecurity than older generations
-
 Passwords are a problem: why device-bound passkeys can be the future of secure authentication
Passwords are a problem: why device-bound passkeys can be the future of secure authenticationIndustry insights AI-driven cyberthreats demand a passwordless future…
-
 LastPass just launched a tool to help security teams keep tabs on shadow IT risks
LastPass just launched a tool to help security teams keep tabs on shadow IT risksNews Companies need to know what apps their employees are using, so LastPass made a browser extension to help
-
 The NCSC wants you to start using password managers and passkeys – here’s how to choose the best options
The NCSC wants you to start using password managers and passkeys – here’s how to choose the best optionsNews New guidance from the NCSC recommends using passkeys and password managers – but how can you choose the best option? ITPro has you covered.
-
 I love magic links – why aren’t more services using them?
I love magic links – why aren’t more services using them?Opinion Using magic links instead of passwords is safe and easy but they’re still infuriatingly underused by businesses
-
 Password management startup Passbolt secures $8 million to shake up credential security
Password management startup Passbolt secures $8 million to shake up credential securityNews Password management startup Passbolt has secured $8 million in funding as part of a Series A investment round.
-
 LastPass breach comes back to haunt users as hackers steal $12 million in cryptocurrency
LastPass breach comes back to haunt users as hackers steal $12 million in cryptocurrencyNews The hackers behind the LastPass breach are on a rampage two years after their initial attack
