Salesforce-based phishing attacks surge 109% since the start of 2024
Threat analysts have uncovered a sophisticated phishing attack imitating emails from Salesforce that are likely bypassing many business email filters


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Phishing attacks making use of fake Salesforce domains have increased by 109% since the start of 2024, according to new research.
The new tactic involves the impersonation of a legitimate Salesforce domain in order to send victims to a spoofed version of a Meta partner portal, which is able to steal user credentials.
The malicious payload used by the threat actors had not been identified on any of VirustTotal’s antivirus scanners and URL/blocklisting services, according to researchers at security software company Egress.
Threat actors were able to impersonate an authentic Salesforce domain by compromising a business using Salesforce products and then launching the attack through the legitimate Salesforce servers, analysis from Egress’ threat intelligence team suggests.
More on Phishing
The attack takes advantage of the popularity of Salesforce’s solutions, used by over 150,000 organizations around the world. Salesforce domains are likely to be included on a ‘trusted sender’ list at many organizations, and thus regardless of the message’s content it would be guaranteed to reach the recipient’s inbox.
The attack also involves the obfuscation of a malicious URL by using the legitimate Google notification service to redirect users to a malicious site.
Unlike other popular approaches used in phishing campaigns, such as using a legitimate site to host a malicious payload or using a legitimate link to disguise the final destination, this attack uses a legitimate service to redirect users to the malicious site.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Employees quickly inspecting the hyperlink may be deceived upon reading ‘notification.google’ at the start of the URL. These links cannot be mass blocked by blocklists due to their legitimate use elsewhere.
Signature-based anti-phishing technologies are also unable to identify the emails as malicious, as Egress found the email passed all three of the SPF, DKIM, and DMARC authentication methods.
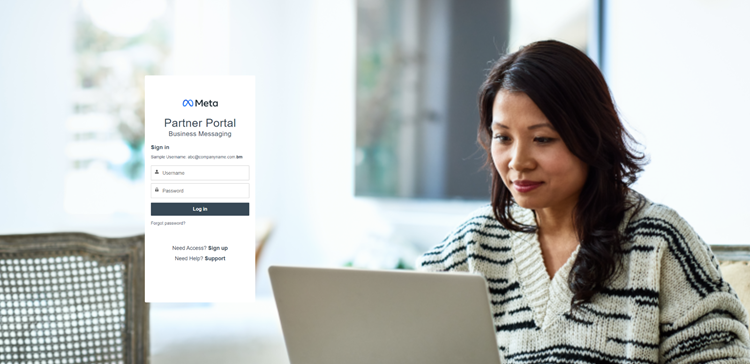
Spoofed Meta partner portal
Once redirected to the spoofed Meta partner page, any information entered into the log in portal are sent as plain text to a command-and-control server linked to the malicious URL.

Legitimate Meta partner page
After entering their credentials, users are redirected again to another fake Meta site disguised as a webform intended to provide extra support for users. This form includes fields for the user’s name, business, email address, and phone number, information the attackers can use to refine their instigate and leverage follow-up attacks.
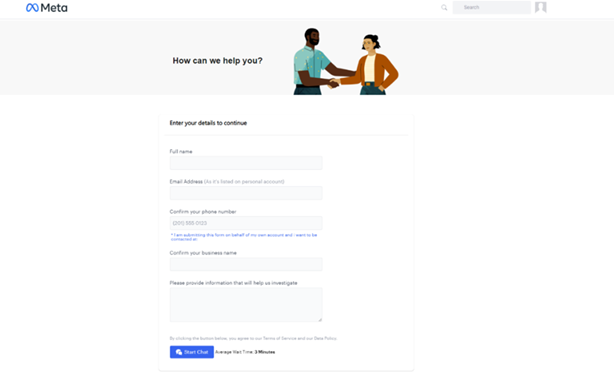
Fake meta webform
Compromising business emails a happy hunting ground for hackers
Phishing attacks targeting businesses are quickly becoming the most profitable form of attack method available to threat actors, with the costs associated with business email compromise attacks exceeding ransomware losses in 2022.
RELATED RESOURCE

Create value from your Salesforce investment
DOWNLOAD NOW
Egress’ 2024 report on email security found 94% of organizations fell victim to phishing attacks, with 79% of account takeover attacks starting with a phishing email.
The widespread adoption of AI among threat actors is also a key factor in improving the efficacy and efficiency of phishing attacks, making them more realistic and faster to produce.
According to the report, the offensive use of AI is front of mind for cyber security leaders, over 60% of whom said the use of deep fakes and AI chatbots within attacks kept them up at night.
AI does have defensive potential also, however, with businesses exploring using generative AI to learn the writing style of an organization’s staff, which is then able to detect suspicious activity including incongruous text in an email.

Solomon Klappholz is a former staff writer for ITPro and ChannelPro. He has experience writing about the technologies that facilitate industrial manufacturing, which led to him developing a particular interest in cybersecurity, IT regulation, industrial infrastructure applications, and machine learning.
-
 PayPal poaches HP’s Enrique Lores in surprise CEO appointment
PayPal poaches HP’s Enrique Lores in surprise CEO appointmentNews The veteran tech executive will lead the payments giant into its next growth phase amid mounting industry challenges
-
 Oracle targets financial services gains with new agentic AI suite
Oracle targets financial services gains with new agentic AI suiteNews The cloud giant has unveiled a new series of agents for retail banking providers
-
 Salesforce customers face second third-party incident this year with Gainsight breach
Salesforce customers face second third-party incident this year with Gainsight breachNews Customers impacted in the Gainsight breach have been contacted by Salesforce
-
 The Salesloft hackers claim they have 1.5 billion compromised Salesforce records
The Salesloft hackers claim they have 1.5 billion compromised Salesforce recordsNews Dozens of big tech companies have been impacted by the Salesloft Drift attacks
-
 How to check if you’ve been affected by Salesforce attacks – and stop hackers dead in their tracks
How to check if you’ve been affected by Salesforce attacks – and stop hackers dead in their tracksNews The FBI has issued a fresh advisory over the threat posed to Salesforce customers by two threat groups. Here's how you can stay safe and mitigate any risks.
-
 Warning issued to Salesforce customers after hackers stole Salesloft Drift data
Warning issued to Salesforce customers after hackers stole Salesloft Drift dataNews Customers were targeted through compromised OAuth access tokens from Salesloft Drift integrations
-
 The Allianz Life data breach just took a huge turn for the worse
The Allianz Life data breach just took a huge turn for the worseNews Around 1.1 million Allianz Life customers are believed to have been impacted in a recent data breach, making up the vast majority of the insurer's North American customers.
-
 Everything we know about the Workday data breach so far
Everything we know about the Workday data breach so farNews HR technology firm Workday has confirmed a data breach after threat actors gained access to a third-party CRM platform.
-
 Google cyber researchers were tracking the ShinyHunters group’s Salesforce attacks – then realized they’d also fallen victim
Google cyber researchers were tracking the ShinyHunters group’s Salesforce attacks – then realized they’d also fallen victimNews In an update to an investigation on the ShinyHunters group, Google revealed it had also been affected