'Bad Rabbit' ransomware found to be similar to NotPetya
Many antivirus tools can't recognise the malware spreading through Russia and Ukraine

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
A new strain of malware is spreading through organisations in eastern Europe, bearing a striking resemblance to the NotPetya ransomware that targeted users around the world earlier this year.
Dubbed 'Bad Rabbit', it has already hit government departments in Ukraine and Kiev's public transport system, although it has also targeted media outlets and news websites, including news agencies in Russia.
Initial analysis of the ransomware by security researchers yesterday found similarities between Bad Rabbit and the NotPetya ransomware, also known as ExPetr, which was widely considered to have been a state-sponsored variant of the Petya malware.
The Bad Rabbit ransomware uses the fairly common attack vector of fooling users into infecting themselves with malicious files masquerading as something legitimate, in this case an Adobe Flash installer.
The ransomware is able to slowly encrypt a user's files after it is installed, and, just like NotPetya, is able to schedule an automatic reboot of the system, which shuts down the computer.
Users are then presented with a near identical splash screen to that of NotPetya, that directs them to a Tor address where they are asked to pay out 0.05 Bitcoin (around $281) in exchange for a decryption key.
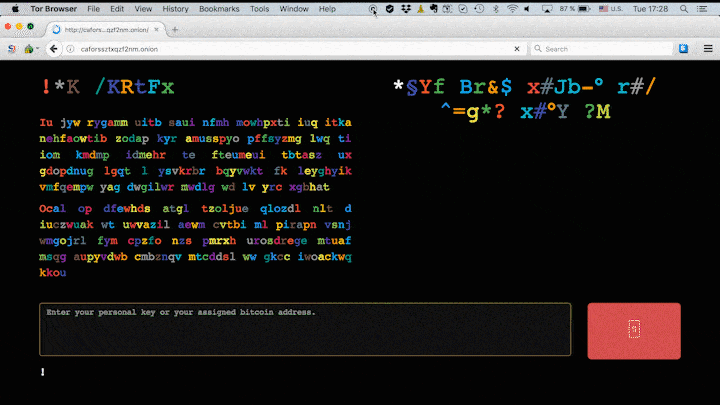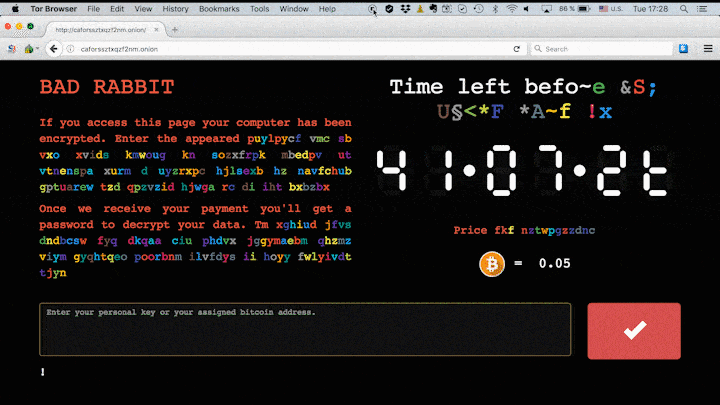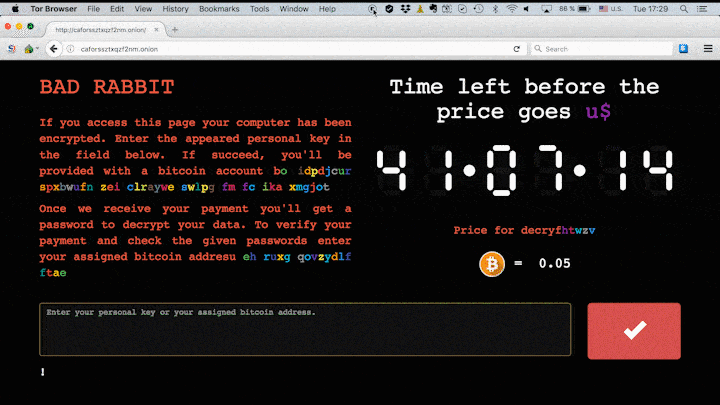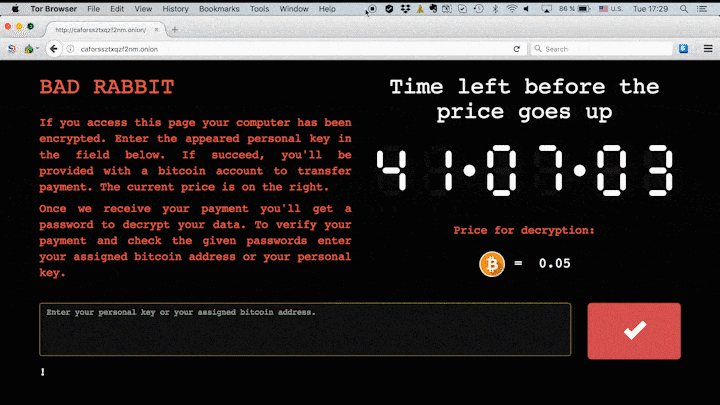
Bad Rabbit's website as seen on Kaspersky's blog
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Researchers have already been successful at creating a 'vaccine' to inoculate against the ransomware, which involves creating a custom script that's able to block its ability to encrypt files. As with similar splash screens seen already this year, such as the WannaCry message, a countdown is displayed showing how long a user has left to pay the ransom until it goes up in price.
Both Kaspersky and Malwarebytes have said that the Bad Rabbit ransomware was likely created by the same author.
"Based on our investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack. However, we cannot confirm it is related to ExPetr," said Kaspersky'sAlex Perekalin in a blog post.
"Whether it's possible to get back files encrypted by Bad Rabbit (either by paying the ransom or by using some glitch in the ransomware code) isn't yet known. Kaspersky Lab antivirus experts are investigating the attack, and we will be updating this post with their findings."
It's unclear how far the ransomware has spread, however Kaspersky has confirmed that most targets are thought to be based in Russia, including news agencies Interfax and Fontanka.ru. Similar reports have emerged from Turkey and Germany, although it's too early to tell whether these are victims of this strain of ransomware.
Tony Rowan, chief security consultant at SentinelOne, said this latest strain demonstrates that hackers will continue to reuse old code as long as it proves effective.
"Indications are that this new variant continues to have success. Given that the propagation mechanism is based on EternalBlue [the Windows exploit patched back in March 2017, which both WannaCry and Petya used], it surprises me that so many people haven't patched their systems. Even more, they continue to rely on the legacy AV products which these types of malware evade so easily."
Virus Total, an online tool that analyses the capabilities of antivirus software, found that of 68 programs, almost half failed to correctly identify the file as malicious.
Security researchers continue to monitor the ransomware amid fears of yet another WannaCry and NotPetya style outbreak, attacks that crippled hundreds of thousands of computer networks around the world.
What is Bad Rabbit?
Bad Rabbit is a new strain of ransomware currently targeting eastern Europe and Russia. It's thought to contain similarities to the NotPetya ransomware, including a similar splash screen and encryption methods.
Who has been targeted?
So far two Russian news agencies, Ukraine's Ministry of Infrastructure and Kiev's public transport system are confirmed to have been hit. Odessa international airpot in Ukraine is also reporting issues, although it's unclear whether this is related. Kaspersky reports that the majority of targets are in Russia, although there are also a handful of infections in Turkey and Germany.
How does it spread?
The Bad Rabbit ransomware infects a machine through a malicious install folder, although it requires a user to manually click on a .exe file. So far there's no indication that the ransomware spreads passively.
Can it be stopped?
A quick vaccine has been found to be effective, but requires users to create a custom file that blocks the write permissions of the ransomware. However, once you're infected you have little choice but to pay the ransom or abandon the files.
Dale Walker is a contributor specializing in cybersecurity, data protection, and IT regulations. He was the former managing editor at ITPro, as well as its sibling sites CloudPro and ChannelPro. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.
-
 Anthropic researchers warn AI could 'inhibit skills formation' for developers
Anthropic researchers warn AI could 'inhibit skills formation' for developersNews A research paper from Anthropic suggests we need to be careful deploying AI to avoid losing critical skills
-
 CultureAI’s new partner program targets AI governance gains for resellers
CultureAI’s new partner program targets AI governance gains for resellersNews The new partner framework aims to help resellers turn AI governance gaps into scalable services revenue
-
 The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwise
The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwiseNews Billing itself as the “only place ransomware allowed", RAMP catered mainly for Russian-speaking cyber criminals
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
-
 The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to know
The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to knowNews The group appears to be infecting support and help-desk personnel with remote access trojans and other forms of malware
-
 Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposed
Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposedNews No ransom has been paid, said president and group CEO Atsushi Katsuki, and the company is restoring its systems