Ransomware that uses a fake children's charity for phishing
CryptoMix uses information lifted from children's charities to coerce victims into ransom payments

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
A new strain of ransomware has surfaced that pretends to be working for the good of a children's charity rather than for criminal gain, in an attempt to make handing over cash more palatable for a victim.
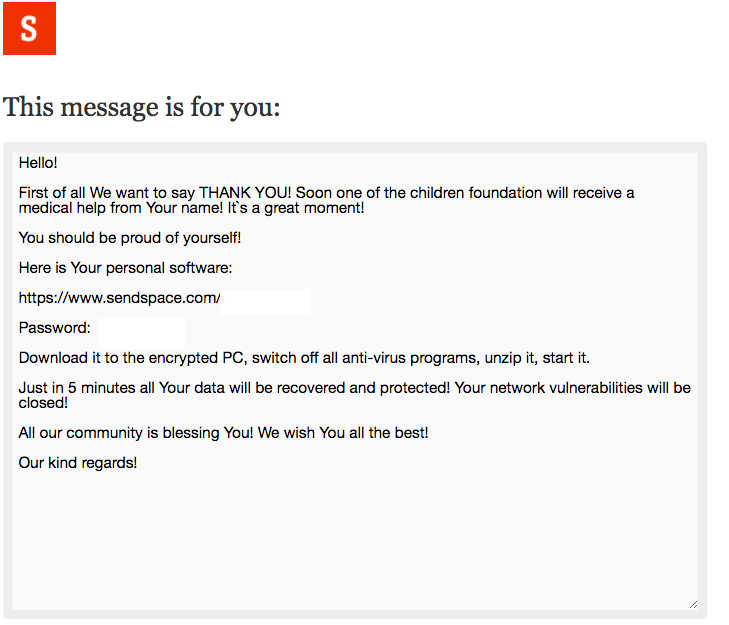
The newly discovered CryptoMix has been found masquerading as a Robin Hood-style of ransomware, providing links to a fictitious charity and an offer to put their name with their donation.
First spotted by cyber security firm Covewave, the ransom notes go so far as to include the names, diagnosis, and even pictures of young children that the ransom payments claim to support which, according to Covewave, the information appears to have been lifted from crowdfunding websites.
"In recent cases, Coveware observed ransom notes and communications that referenced a fictitious charity but real children," the company said. "The ransom communications begin with a .txt file that provides email addresses that the victim may use to contact the ransomware distributor."
Covewave have an example of the email exchange hackers use with this scheme. In the correspondence, they claim to work for a fictitious charity and give a description of a child's diagnosis and the funding amount being raised.
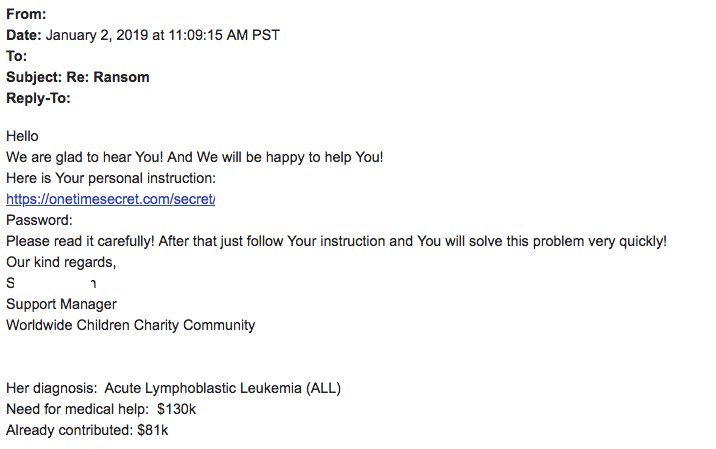
Email of a hacker using CryptoMix - courtesy of Covewave
Disturbingly, the email contained an image of what Croewave said appeared to be a 3-year-old girl lifted off a crowdfunding site.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
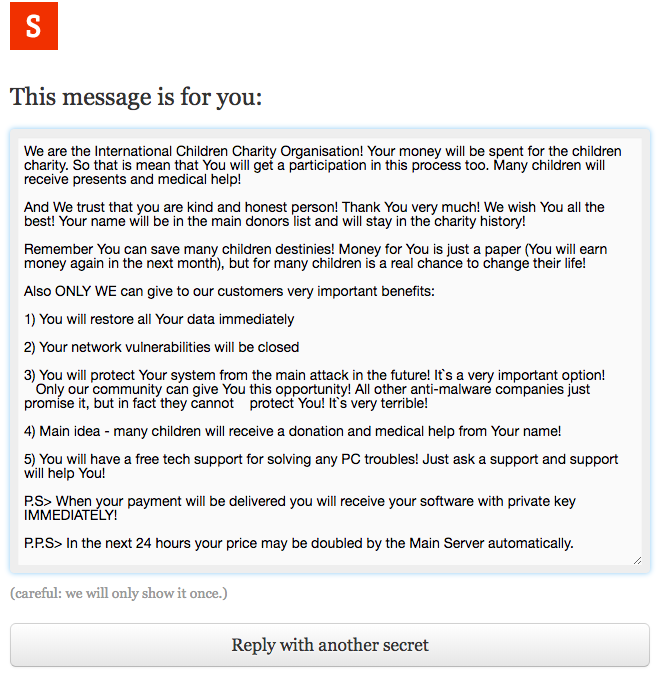
From there, the hacker will direct the victim to view payment information with instructions on a temporary page. This page includes bitcoin wallet payment instructions and more detail on the fake charity.
"We are guessing this tactic is meant to assuage the moral hazard associated with paying a ransom," Covewave explained. "It goes without saying that these cyber criminals did think this through. It is poignantly obvious that the charity is fake, and that the details of the child's case are lifted from other sites."
After paying the ransom, a victim is given more detail about the charity as well as a message suggesting their own name will be used alongside their donation.
CryptoMix has also been identified by Avast as a particularly nasty type of ransomware that can ultimately leaves your files locked even if you pay the ransom.
This strain of ransomware was first spotted in March 2016. The spread of this ransomware could be described as a medium level of prevalence and uses exploit kits as its main delivery method.
"Once CryptoMix infects a machine, it tries to communicate with its command and control server to establish a key to encrypt files. However, if the server is not available or if there is a connection issue, such as a blocked communication by a firewall, the ransomware will encrypt files with one of its fixed keys, or 'offline key'," it said.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
-
 AWS exec laments European grid connection woes in data center push
AWS exec laments European grid connection woes in data center pushNews Efforts by AWS to expand data center infrastructure across Europe face severe delays due to sluggish grid connection practices, a senior company figure claims.
-
 Geekom X14 Pro review
Geekom X14 Pro reviewReviews A debut laptop that boasts a fine OLED screen, 32GB of RAM, and a 2TB SSD as standard
-
 Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoing
Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoingNews Thousands of attacker servers all had the same autogenerated Windows hostnames, according to Sophos
-
 Google issues warning over ShinyHunters-branded vishing campaigns
Google issues warning over ShinyHunters-branded vishing campaignsNews Related groups are stealing data through voice phishing and fake credential harvesting websites
-
 The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwise
The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwiseNews Billing itself as the “only place ransomware allowed", RAMP catered mainly for Russian-speaking cyber criminals
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
