250,000 stolen MySQL databases auctioned on the dark web
Hackers are thought to have obtained 7TB of stolen data using the PLEASE_READ_ME ransomware campaign


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
A quarter of a million databases stolen from tens of thousands of breached MySQL servers are being offered for sale on the dark web, according to security researchers from Guardicore Labs.
Hackers are believed to have obtained 7TB of stolen data using the PLEASE_READ_ME ransomware campaign, successfully targeting around 83,000 MySQL database servers.
PLEASE_READ_ME has reportedly been active since January 2020, attacking weak credentials on internet-facing MySQL servers.
Since then, Guardicore Global Sensors Network (GGSN) reported 92 attacks, with numbers rising sharply in October. According to Guardicore researchers, the ransomware attacks originated from 11 different IP addresses, most of which were found to be located in the UK and Ireland.
The ransomware campaign is untargeted, meaning that it attempts to infect any of the five million MySQL servers which are internet-facing. Hackers exploit weak credentials and are able to re-access the network by leaving a backdoor user on the database for persistence.
Guardicore Labs researchers managed to discover two different variants during the lifetime of this campaign. The first, which lasted from January to the end of November, saw attackers leaving their victims a ransom note with their wallet address, the amount of Bitcoin to pay, as well as an email address for technical support, with 10 days being given to make the payment.
The second variant, which began on 3 October and also lasted until late November, got rid of the Bitcoin wallet payments and email communications. Instead, hackers opted for a website in the Tor network to receive payments and used unique alphanumeric tokens, outlined in the ransom notes, to identify the victims.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
In a blog post detailing the discovery, security researchers Ophir Harpaz and Omri Marom said that the “PLEASE_READ_ME operators are trying to up their game by using double extortion in scale”.
“Factoring their operation will render the campaign more scalable and profitable. Guardicore Labs provides an IOCs repository and will keep monitoring this campaign to help organizations protect against it,” they added.
Having only graduated from City University in 2019, Sabina has already demonstrated her abilities as a keen writer and effective journalist. Currently a content writer for Drapers, Sabina spent a number of years writing for ITPro, specialising in networking and telecommunications, as well as charting the efforts of technology companies to improve their inclusion and diversity strategies, a topic close to her heart.
Sabina has also held a number of editorial roles at Harper's Bazaar, Cube Collective, and HighClouds.
-
 AWS CEO Matt Garman isn’t convinced AI spells the end of the software industry
AWS CEO Matt Garman isn’t convinced AI spells the end of the software industryNews Software stocks have taken a beating in recent weeks, but AWS CEO Matt Garman has joined Nvidia's Jensen Huang and Databricks CEO Ali Ghodsi in pouring cold water on the AI-fueled hysteria.
-
 Deepfake business risks are growing
Deepfake business risks are growingIn-depth As the risk of being targeted by deepfakes increases, what should businesses be looking out for?
-
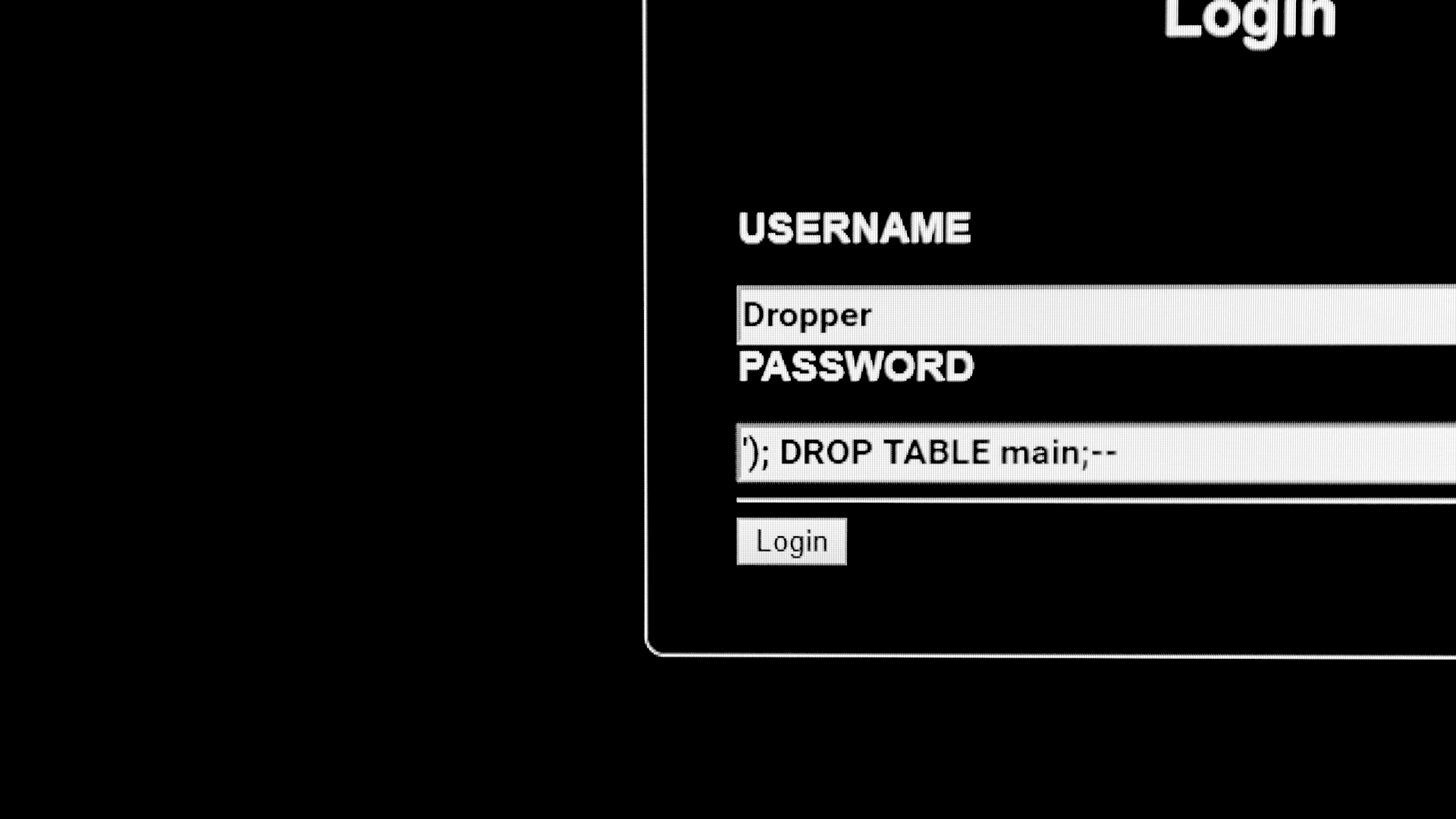 How does a SQL injection attack work?
How does a SQL injection attack work?In-depth Understanding one of the simplest, yet most effective, methods of cyber attack
-
 SQL injection flaw fixed by Drupal
SQL injection flaw fixed by DrupalNews The makers of the open source content management system have fixed troublesome flaw
-
 SQL and DDOS attacks remain priority for hackers
SQL and DDOS attacks remain priority for hackersNews Sensitive data increasingly being gleamed from social networks and through the practice of 'E-whoring', notes Imperva.
-
 Oracle issues 78 vulnerability patches
Oracle issues 78 vulnerability patchesNews Combined with Microsoft and Adobe patches, Oracle has made IT departments' lives a little harder this month.
-
 Oracle quiet on MySQL.com hack claims
Oracle quiet on MySQL.com hack claimsNews Larry Ellison's firm neither confirms nor denies MySQL.com has been hacked again.
-
 MySQL.com hacked again
MySQL.com hacked againNews MySQL.com is found serving malware after the second known hack on the website this year.
-
 MySQL hit by irony attack
MySQL hit by irony attackNews MySQL.com gets hit by an SQL injection attack, and hackers leak some disconcertingly weak passwords onto the net.
-
 Week in review: Skynet here we come!
Week in review: Skynet here we come!News Microsoft has trouble with XP and SQL, HMRC staff are snoops, bloggers speak up on elections and robots learn to carry mugs.
