Twitter investigates possibility that DMs were accessed during Bitcoin hack
Twitter maintains the attack was the result of 'social engineering', although reports suggest an employee may have been bribed


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Twitter is investigating whether hackers gained access to the direct messages belonging to accounts of dozens of high-profile individuals following Wednesday’s hack.
The company has confirmed that approximately 130 accounts were targeted by attackers during the incident, including a handful of instances where hackers were able to send tweets.
Despite being able to access accounts to the degree where sending tweets was possible, Twitter said there’s currently no evidence that attackers accessed user passwords, so resetting these is not considered a necessary measure at this stage.
Although Twitter described the infiltration as a “social engineering attack”, the company is also investigating the possibility that an employee was bribed, according to the New York Times.
The company also hasn’t ruled out whether private data like direct messages had been accessed, although the extent to which the hackers gained access to a handful of the 130 compromised accounts suggests this is entirely possible.
“We’re working with impacted account owners and will continue to do so over the next several days,” Twitter said. “We are continuing to assess whether non-public data related to these accounts was compromised, and will provide updates if we determine that occurred.”
The option to download data from your Twitter account has been switched off during the ongoing investigation. The company also said it is taking “aggressive steps” to secure its systems.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
This story has been updated to reflect new information. The original story is published below
Hackers targeted Twitter employees with access to company tools and internal systems in a “co-ordinated social engineering attack” to seize control of high profile accounts and launch a Bitcoin scam.
Several major account holders began posting suspicious messages last night on a co-ordinated basis, including Elon Musk, Bill Gates, Barack Obama, and Jeff Bezos, which between them have hundreds of millions of followers.
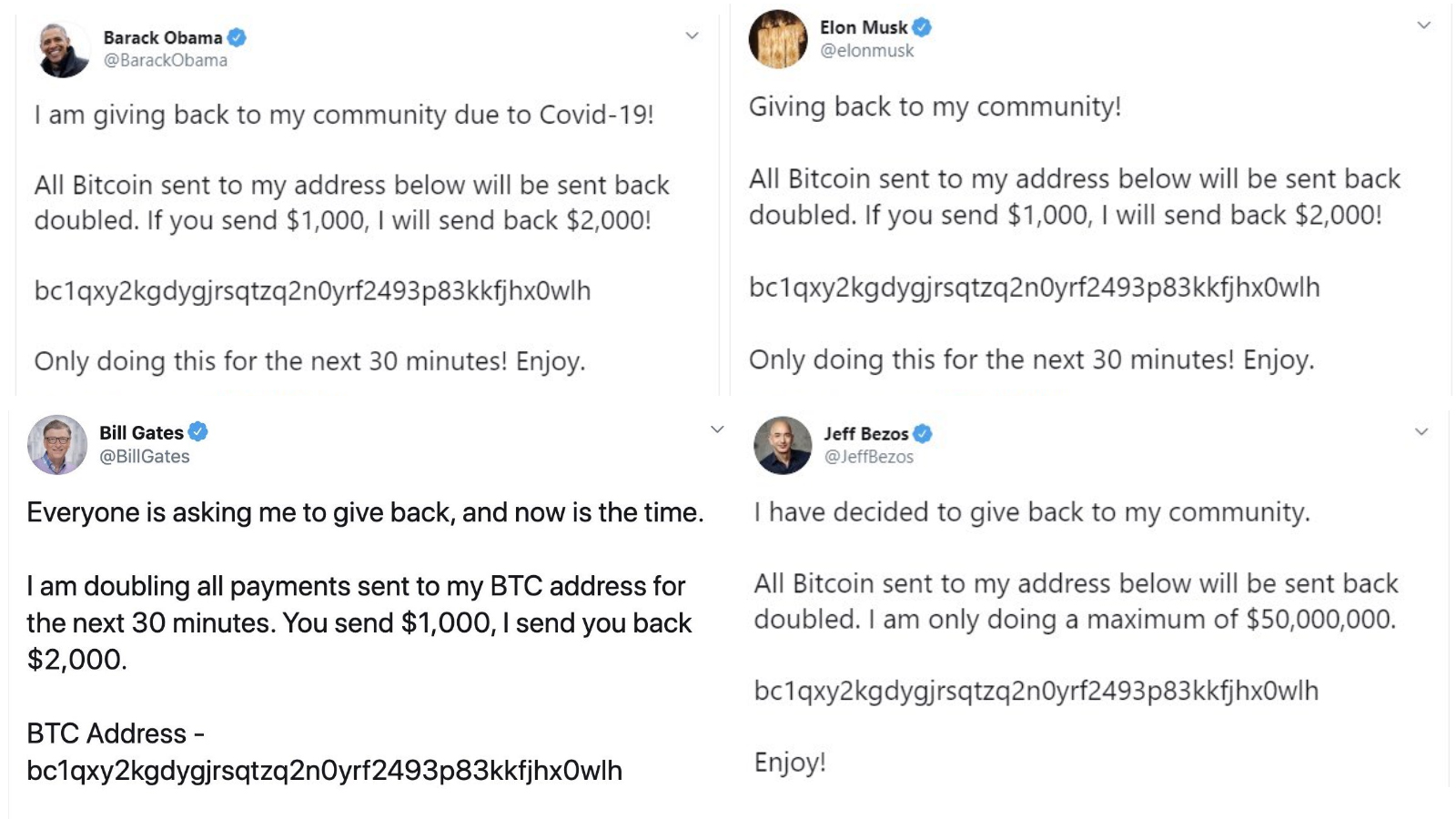
These messages described a scheme whereby all Bitcoin donated to a particular wallet, the same in each fraudulent tweet, would be sent back doubled, in light of that individual deciding to “give back”.
Having tracked the Bitcoin wallet, the hackers have, at the time of writing managed to solicit 376 fraudulent donations to the tune of 12.87 Bitcoin, equivalent to approximately £93,000.
Twitter confirmed at 10:45PM BST that it was aware of a security incident, and would investigate this urgently. The company subsequently placed heavy restrictions on many account holders, especially those who are verified, preventing them from tweeting or resetting their passwords, alongside “some other account functionalities”.
Those accounts that were compromised, having posted the fraudulent message, were also temporarily blocked entirely. These restrictions have been gradually lifted, with a handful of users only regaining the capacity to tweet as normal this morning.
Twitter soon confirmed in the early hours of the morning it had detected what it believed to be a coordinated social engineering attack by people who successfully targeted some of its employees with access to internal systems and tools.
“We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf,” the company said. “We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.
“We also limited functionality for a much larger group of accounts, like all verified accounts (even those with no evidence of being compromised), while we continue to fully investigate this. This was disruptive, but it was an important step to reduce risk. Most functionality has been restored but we may take further actions and will update you if we do.”
The company has confirmed it’s taken “significant steps” to limit access to internal systems and tools during its investigation, although these haven’t been outlined in any great detail.
It also appears employees targeted in the social engineering attack had direct access to users' accounts. For example, fraudulent Bitcoin tweets were often 'pinned', which could normally only be performed by logging into accounts.
Alarmingly, some of those involved in the hack told Motherboard they actually paid a Twitter employee to grant them access to their own account, with the accounts taken over using an internal Twitter tool. Some users have posted screenshots of the tool in question, and have been circulating these images online.
The incident is certainly one of the company’s biggest security breaches in history and follows a string of smaller-scale hacks over the previous few months and years.
Only last month Twitter alerted business customers after flagging a data breach, suggesting their personal details may have been compromised due to an issue with the way Twitter cached data on web browsers. The information of those who were signed up to the company’s advertising or analytics platform may have been accessed by third-parties as a result of the glitch.
This follows an incident in August 2019 in which Twitter found an issue with its privacy settings, meaning musers may have inadvertently been sharing data with third-parties. This, however, was more of a privacy violation than an out-and-out security breach.
The largest breach to date, barring this week’s incident, however, arose in 2018 after a bug allowed company staff to view account passwords in an unencrypted form. The company asked 330 million users, as a result, to change their passwords urgently for fear of their accounts being compromised.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Google issues warning over ShinyHunters-branded vishing campaigns
Google issues warning over ShinyHunters-branded vishing campaignsNews Related groups are stealing data through voice phishing and fake credential harvesting websites
-
 Thousands of Microsoft Teams users are being targeted in a new phishing campaign
Thousands of Microsoft Teams users are being targeted in a new phishing campaignNews Microsoft Teams users should be on the alert, according to researchers at Check Point
-
 Microsoft warns of rising AitM phishing attacks on energy sector
Microsoft warns of rising AitM phishing attacks on energy sectorNews The campaign abused SharePoint file sharing services to deliver phishing payloads and altered inbox rules to maintain persistence
-
 Warning issued as surge in OAuth device code phishing leads to M365 account takeovers
Warning issued as surge in OAuth device code phishing leads to M365 account takeoversNews Successful attacks enable full M365 account access, opening the door to data theft, lateral movement, and persistent compromise
-
 Amazon CSO Stephen Schmidt says the company has rejected more than 1,800 fake North Korean job applicants in 18 months – but one managed to slip through the net
Amazon CSO Stephen Schmidt says the company has rejected more than 1,800 fake North Korean job applicants in 18 months – but one managed to slip through the netNews Analysis from Amazon highlights the growing scale of North Korean-backed "fake IT worker" campaigns
-
 Complacent Gen Z and Millennial workers are more likely to be duped by social engineering attacks
Complacent Gen Z and Millennial workers are more likely to be duped by social engineering attacksNews Overconfidence and a lack of security training are putting organizations at risk
-
 Hackers are abusing ConnectWise ScreenConnect, again
Hackers are abusing ConnectWise ScreenConnect, againNews A new spear phishing campaign has targeted more than 900 organizations with fake invitations from platforms like Zoom and Microsoft Teams.
-
 The Allianz Life data breach just took a huge turn for the worse
The Allianz Life data breach just took a huge turn for the worseNews Around 1.1 million Allianz Life customers are believed to have been impacted in a recent data breach, making up the vast majority of the insurer's North American customers.

