Simple Active Directory tweak helps block BlackMatter ransomware attacks
Security researchers reverse engineer the infamous ransomware strain and discover a way to stymie its file encryption process, even if it reaches a corporate network

Security researchers have discovered a flaw in the logic driving the BlackMatter ransomware family that allows businesses to stop the program from encrypting remote shared folders on an organisation's network.
The findings mean businesses are able to deploy a relatively simple mitigation to protect themselves against a key attack vector in one of the most successful ransomware strains of the past few years.
Despite the ransomware family being highly sophisticated and deploying many anti-debugging techniques, the mitigation can help prevent BlackMatter from searching for other computers in the active directory (AD), according to researchers at Illusive.
By creating a 'dummy' computer account in the AD, and setting the 'dNSHostName' attribute to "not set", BlackMatter will stop searching the AD for other computers to encrypt once it stumbles upon the fake account.
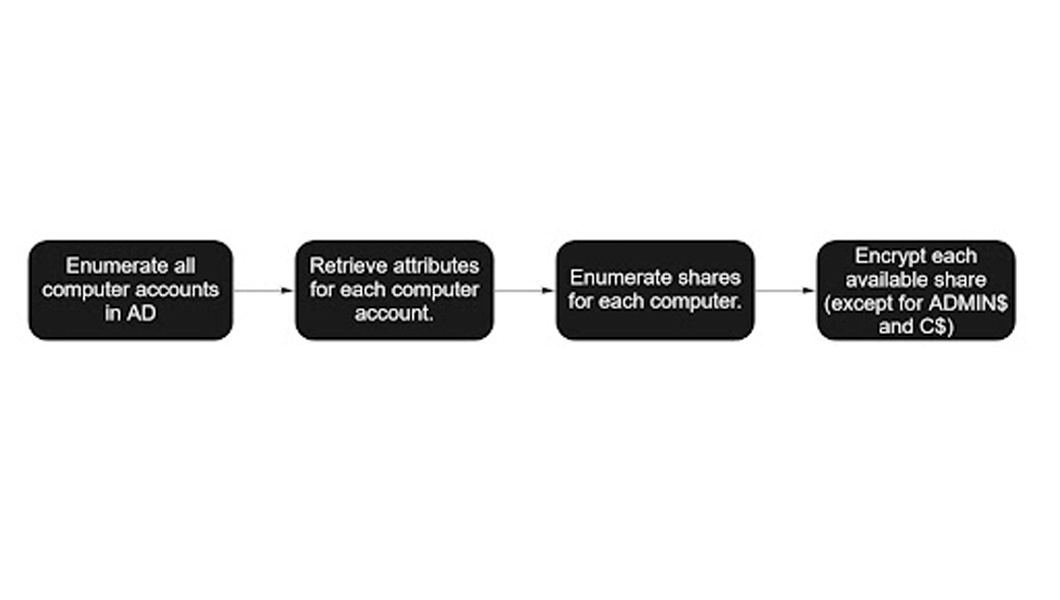
BlackMatter's encryption and computer enumeration process
Researchers said BlackMatter first attempts to enumerate all computer accounts in the AD, scanning all accounts alphabetically. It then retrieves the attributes for each computer account before enumerating shares for each computer and encrypting each available share, except for ADMIN$ and C$.
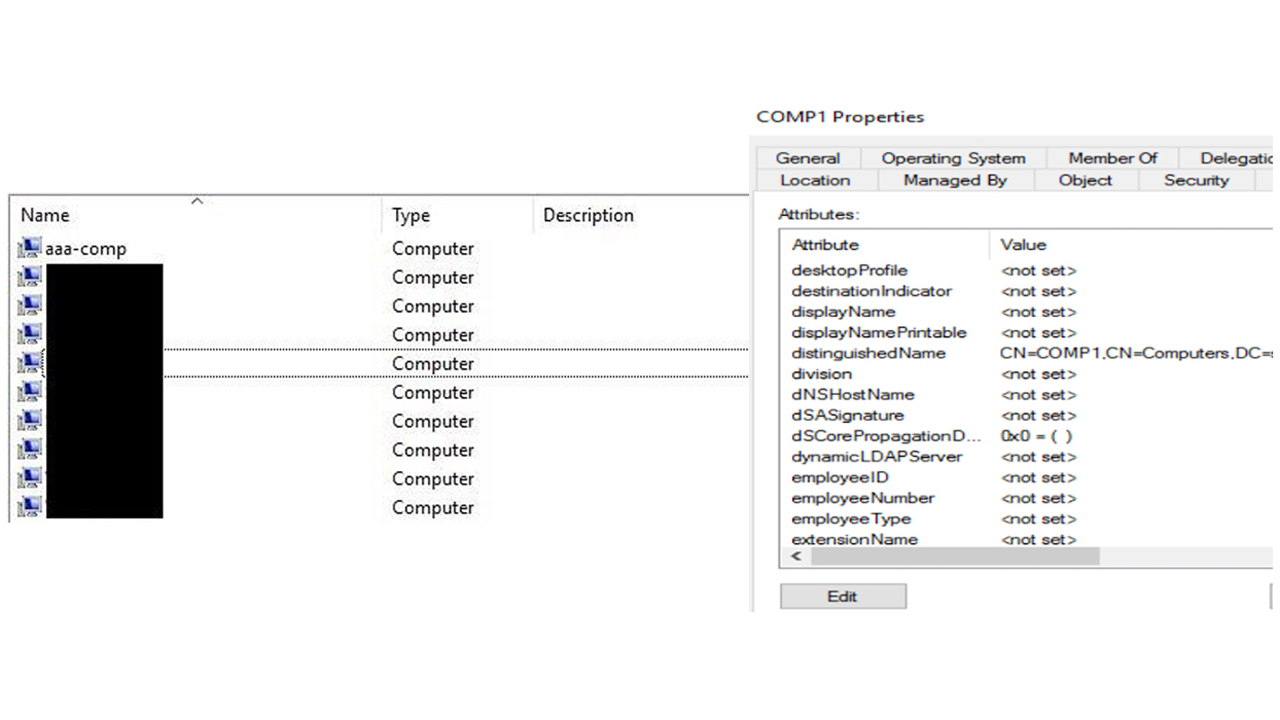
An example of how to set up a computer account to stop the encryption of all machines in an organisation
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
This means by naming a user account 'aaa-comp', for example, and disabling the dNSHostName attribute, system administrators can have that 'dummy' account appear first in the alphabetically organised AD. If BlackMatter started scanning for computers, it would scan aaa-comp first and would stop looking for other computers to encrypt in the AD.
The result would lead to the infection of that single computer account and the machine would become encrypted, but it would prevent BlackMatter from encrypting remote file shares. This dummy 'aaa-comp' account would effectively act like a honeypot, preventing a severe security incident.
The researchers said stopping the search and encryption of remote shared folders is just one attack method BlackMatter uses to inflict damage on victims, and that the mitigation isn't a silver bullet. Other methods, such as local file encryption and mapped drive encryption, are all still viable to BlackMatter, even with the mitigation in place.
It would be "unusual" to configure a computer account without a dNSHostName set, Shahar Zelig, security researcher at Illusive, told IT Pro. Computers normally have the dNSHostName attribute when joining the AD.
Asked why BlackMatter stops searching when it encounters such an account, Zelig said: "we cannot be certain about the reason, but having a computer account lacking the dNSHostName attribute is not something that appears naturally in an Active Directory environment, so it seems likely that the BlackMatter group considered it as an edge-case that they should not handle."
Preventing BlackMatter from encrypting remotely accessible folders can lower the amount of damage the attack can achieve. The mitigation may not prevent encryption of the computers on which it's executed, but can help protect public folders containing business-critical data.
"This finding is significant since encrypting remote shared folders might cause huge [disruption] to an organisation, whether this is a shared folder on an employee's computer or a file server that serves the entire organisation with important data," said Zelig. "In a scenario where BlackMatter is distributed to only a part of the network, remote share encryption is significant, since it can affect accessible shares even though the ransomware itself was not executed on the target device."
Technical overview of BlackMatter
Once it gains access to a machine, BlackMatter attempts to retrieve all computers from the AD, but it only searches the built-in 'Computers' container and not objects found in other organisational units (OUs). Once it identifies all computers in the AD, it uses lightweight directory access protocol (LDAP) requests to retrieve attributes of those computers.
BlackMatter uses three standard API functions to enumerate computers in the AD and store them for further use: ADsOpenObject, AdsBuildEnumerator, ADsEnumerateNext.
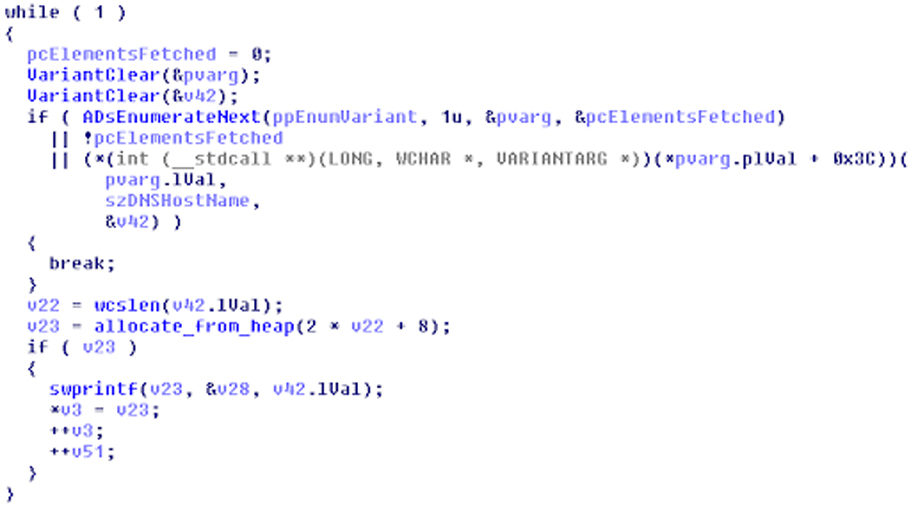
The latter of the three is called for each iteration of the loop and the loop breaks if either ADsEnumerateNext fails, no elements are returned by ADsEnumerateNext, or if it's unable to get the dNSHostName attribute. The loop is broken if dNSHostName is not set.
After computers have been enumerated, BlackMatter then uses the NetShareEnum function to map what shares each computer has, which creates a NetShareEnumAll request over remote procedure call (RPC). BlackMatter will then attempt to access the shares via server message block (SMB), ignoring C$ and ADMIN$, and ignoring types STYPE_DISKTREE and STYPE_SPECIAL, before encrypting the files.
BlackMatter background
RELATED RESOURCE

BlackMatter is a family of ransomware that has claimed many high-profile victims in the past 12 months, including the massively disruptive attack on Colonial Pipeline.
Iowa and Minnesota-based farms were also successfully targeted by ransomware operators using BlackMatter, which led CISA, FBI, and NSA to publish a joint advisory warning US businesses of the threat it faced. The US government later offered a $10 million reward to anyone who could aid the investigation into those behind the attack on Colonial Pipeline.
Despite the sophisticated nature of BlackMatter and how devastating it has proven to be as a ransomware strain, Illusive's findings don't mark the first time a cyber security outfit has found flaws in its code.
Following an investigation of BlackMatter in October 2021, researchers at Emisoft found that an encryption flaw used by the ransomware could be exploited so that victims wouldn't have to pay the ransom in order to restore access to their files. The company claimed the finding has helped companies save millions in ransom payments.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Will autonomous robotics leap forward in 2026?
Will autonomous robotics leap forward in 2026?In-depth Connectivity and cost benefits remain barriers, despite breakthroughs in physical AI
-
 AWS and NTT Data team up to drive legacy IT modernization in Europe
AWS and NTT Data team up to drive legacy IT modernization in EuropeNews Partnership between AWS and NTT DATA aims to boost AWS European Sovereign Cloud capabilities
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
-
 The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to know
The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to knowNews The group appears to be infecting support and help-desk personnel with remote access trojans and other forms of malware
-
 Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposed
Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposedNews No ransom has been paid, said president and group CEO Atsushi Katsuki, and the company is restoring its systems
-
 The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'
The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'News Media Land offers 'bulletproof' hosting services used for ransomware and DDoS attacks around the world