TITUS Aware for Microsoft Outlook review
TITUS Aware for Microsoft Outlook is designed to stop email data leakage at the desktop, while educating and involving users at the same time. Does it achieve these commendable goals? Dave Mitchell thinks it's a remarkably simple solution to a serious problem.
Businesses that have standardised on Microsoft Outlook in the workplace will find TITUS Aware a simple and cost effective method of preventing data leaks. By actively involving users and helping them resolve policy breaches it can reduce support overheads and will also educate them about their responsibilities in protecting confidential information.

The XML files are also used to maintain lists of unacceptable words or phrases and patterns such as social security or credit card numbers. If required, you can add advisory headers and footers to outbound messages along with metadata that may be used by security appliances to check that TA message processing has occurred.
The Administration Tool is simple to use and groups all policy components under a set of nested folders. The controls in the Global Options tab let you enable or disable TA and modify general settings such as loading a splash screen for Outlook users. A useful option is support for Outlook's calendar and tasks, so appointments and job assignments can also be included in DLP policies.
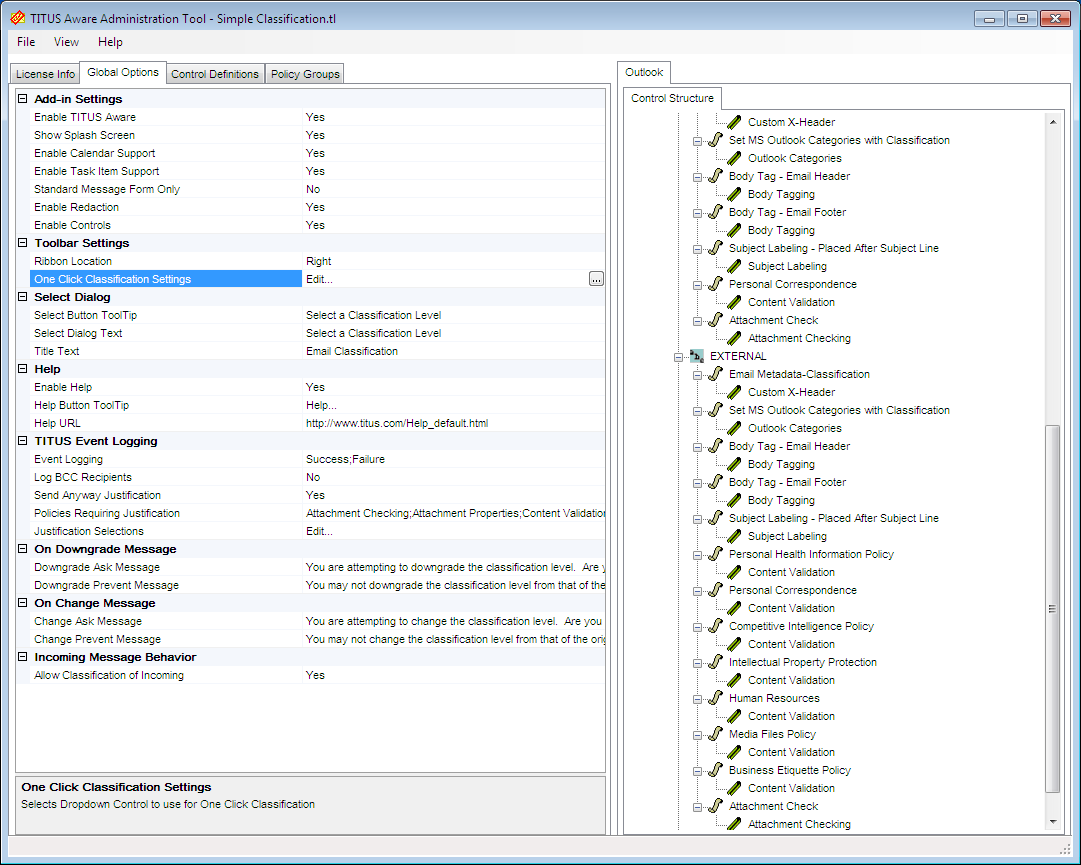
The Global Options are used to activate features for the TA Outlook agent and control how it behaves.
From the user's perspective TA presents a shallow learning curve. When we next loaded Outlook on our clients we found a new set of icons in the Ribbon with the first providing quick access to TA's content checker.
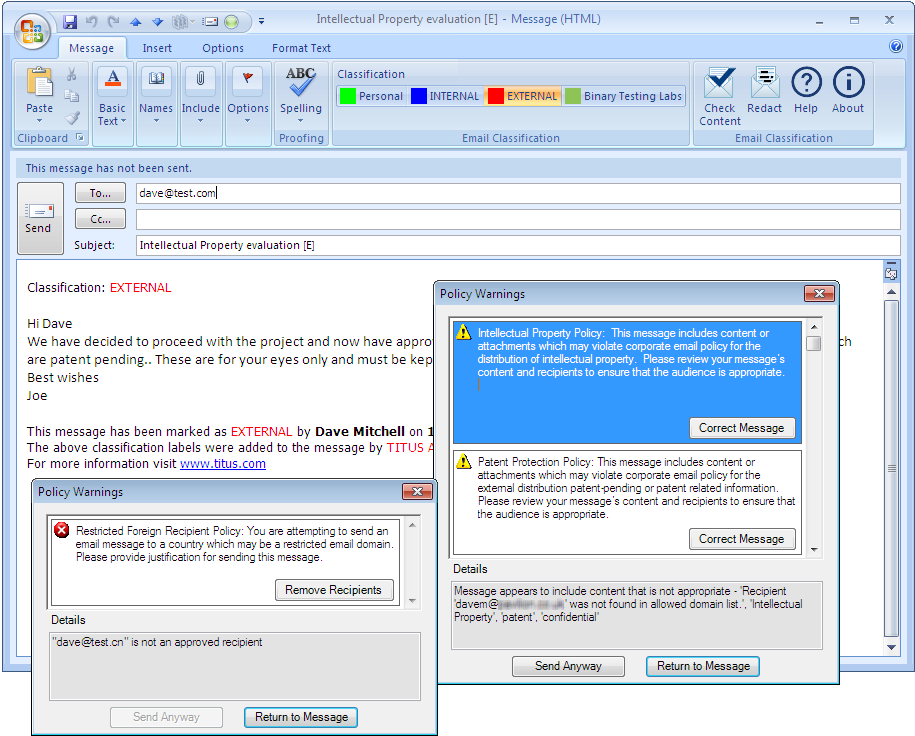
Users can classify messages from the Outlook Ribbon and if they infringe a policy plenty of remediation assistance is provided.
Selecting this applies the active policy and the user will be advised if the message fails. A pop-up window warns the user of a policy failure and shows the reasons for this. They can then opt to correct the message and TA provides a wizard showing them what needs to be done. Parts of the message can be automatically redacted so they can't be read. If the user chooses to send the message without verifying it first, it will still be subject to the same policy checks.
TA's justification feature can be used to give some users more leeway with their message content. If this is enabled in the policy settings, the user may ignore validation failures and sent the message anyway. If they do, TA loads a dialogue box asking them to provide a reason which will be logged.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"
Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"News OpenAI models and tools will now be embedded within the Snowflake Intelligence and Cortex platforms
By Ross Kelly Published
-
 What security teams need to know about the NSA's new zero trust guidelines
What security teams need to know about the NSA's new zero trust guidelinesNews The new guidelines aim to move an organization from discovery to target-level implementation of zero trust practices
By Emma Woollacott Published
-
 Amazon’s rumored OpenAI investment points to a “lack of confidence” in Nova model range
Amazon’s rumored OpenAI investment points to a “lack of confidence” in Nova model rangeNews The hyperscaler is among a number of firms targeting investment in the company
By Ross Kelly Published
