Thecus N5200XXX review
The provocatively named N5200XXX is one of a range of new NAS appliances from Thecus and claims to be extreme in every way. It hits the spot when it comes to price and in this review Dave Mitchell finds out whether it’s on target for performance and features as well.
The N5200XXX may not be as featured packed as QNap’s excellent TS-559 Pro II, but it's much value with a 5TB model costing nearly £400 less. Performance is on a par with most Atom based desktop appliances and its extensive NAS and IP SAN features makes it a good network storage choice for small businesses on a tight budget.

The appliance supports iSCSI targets but prior to RAID array creation, you must decide how much space you want to keep aside for these. Target creation is simple and iSCSI thin provisioning is supported so you can create targets that only use a small amount of space on the appliance but appear much larger to the host. As more data is stored on the target, the appliance dynamically allocates extra space to it.
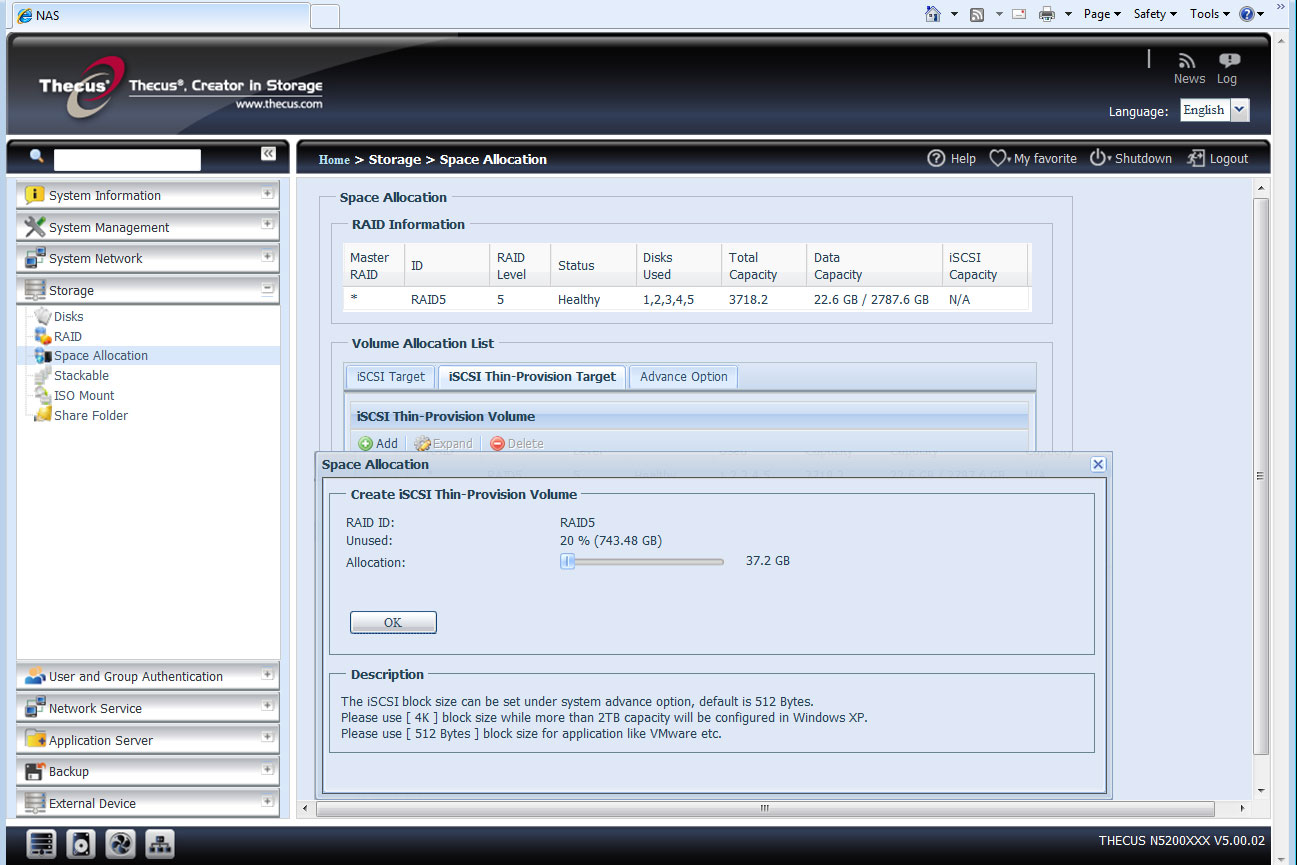
IP SAN support extends to thinly provisioned iSCSI targets for better storage usage.
For workstation backup Thecus includes a single-user copy of Acronis True Image Personal which does not support Windows Server. It takes manual backups of files and folders or entire drives as images to the appliance and can create a bootable disaster recovery disk. However, this is a heavily stripped down version so if you want job scheduling, disk cloning, incremental backups and more you must upgrade.
Other backup options include support for Rsync where the appliance acts as a target for other appliances. A free add-on module allows it to replicate to other targets and another enables scheduled backups to locally connected USB and eSATA devices. The appliance's operating system is also protected by Thecus' dual-DOMs. The second DOM automatically maintains a backup copy which is called upon if the primary one fails and you can schedule regular backups too.
Many vendors are adding cloud-based services to their appliances but Thecus isn't one of them. So far, the best example we've seen of this feature is QNap's MyCloudNAS service which allows you to use the appliance to provide your own secure cloud backup, multimedia and file sharing services to remote workers.
The N5200XXX delivered respectable results in our performance tests. Using a Broadberry dual Opteron 4162-equipped rack server running Windows Server 2008 R2 64-bit, drag and drop copies of a 2.52GB video clip returned read and write speeds of 89MB/s and 86MB/s. Our 17.4GB collection of 10,500 files was also handled well with this folder copied to the appliance at a rate of 60MB/s.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
By Emma Woollacott Published
-
 Infosys teams up with AWS to fuse Amazon Q Developer with internal tools
Infosys teams up with AWS to fuse Amazon Q Developer with internal toolsNews Combining Infosys Topaz and Amazon Q Developer will enhance the company's internal operations and drive innovation for customers
By Emma Woollacott Published
-
 Lisa Su says AI is changing AMD’s hiring strategy – but not for the reason you might think
Lisa Su says AI is changing AMD’s hiring strategy – but not for the reason you might thinkNews AMD CEO Lisa Su has revealed AI is directly influencing recruitment practices at the chip maker but, unlike some tech firms, it’s led to increased headcount.
By Ross Kelly Published
