GFI WebMonitor 2011 R3 review
GFI's WebMonitor software focuses on providing stiff web content security and costs a lot less than an appliance. Dave Mitchell loads it up in the lab to see if it can keep your users out of trouble and your network safe.
Businesses and educational establishments that want quality web content management and monitoring, but don’t want to pay a premium for an appliance, should consider GFI’s WebMonitor. Host hardware requirements are quite reasonable, the software is easy to deploy and it has a good range of top performing security measures and reporting tools.

The WebMonitor console is a tidy affair that provides a top level dashboard of graphs and tables showing current web activity. Options are provided for viewing general web traffic, blocked sites, the most popular categories and so on. Each panel can be moved around using drag and drop.
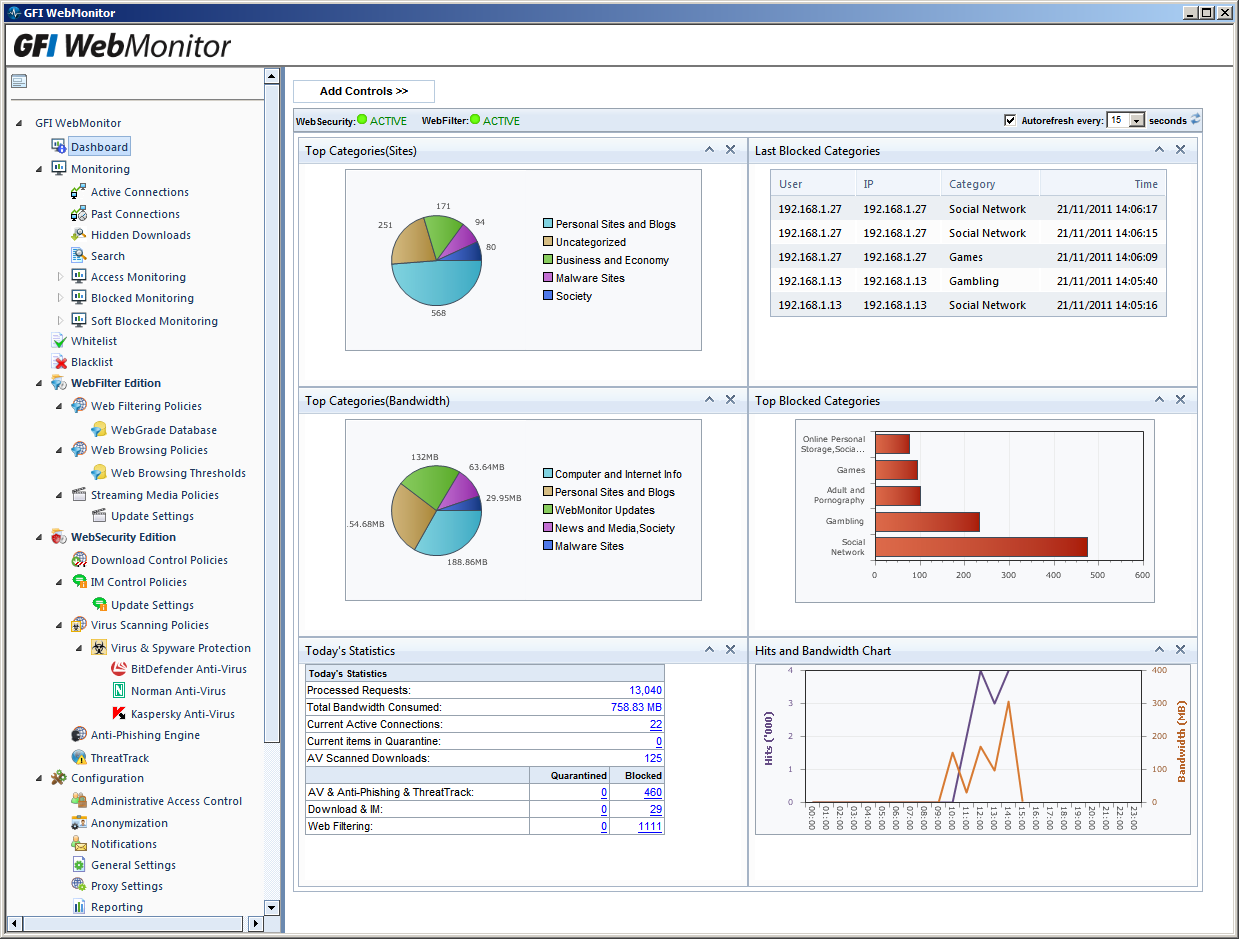
The Dashboard provides plenty of detail on real time web activity and can be customised using drag and drop.
Web access is controlled with policies applied to users, groups and IP addresses. Separate policies are used to manage web content access, browsing periods, anti-virus scanning, streaming media, file downloads and IM apps.
For web filtering you can choose from over seventy WebGrade categories. For each one you can block or allow them, or use the quarantine option which blocks access to a site and makes the user wait for administrative approval.
Selected users and groups may be permitted to browse certain categories or web sites, but time-based policies can be used to restrict how long they can access them for. These limits can be based on daily, weekly or monthly usage or you can apply download limits in KB or MB for these periods instead.
HTTPS scanning comes as standard and WebMonitor provides a wizard that runs through certificate creation. The host system can also cache downloaded files and web content to improve response times.
Virus scanning policies are accessed from the WebSecurity console section. You can choose from a list of file types, pick the engines for scanning and decide whether to delete or quarantine infected files. When downloading files, users can be redirected to a web page showing their progress and only when the file is deemed to be safe will they be allowed to save it to their system.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Microsoft says 100% of its global electricity consumption is now matched by renewable energy
Microsoft says 100% of its global electricity consumption is now matched by renewable energyNews The tech giant is among the largest corporate purchasers of renewable energy
By Emma Woollacott Published
-
 Sam Altman just said what everyone is thinking about AI layoffs
Sam Altman just said what everyone is thinking about AI layoffsNews AI layoff claims are overblown and increasingly used as an excuse for “traditional drivers” when implementing job cuts
By Ross Kelly Published
-
 A single compromised account gave hackers access to 1.2 million French banking records
A single compromised account gave hackers access to 1.2 million French banking recordsNews FICOBA has warned that “numerous” scams are already in circulation following the data breach
By Emma Woollacott Published
