
Davey Winder
Davey is a three-decade veteran technology journalist specialising in cybersecurity and privacy matters and has been a Contributing Editor at PC Pro magazine since the first issue was published in 1994. He's also a Senior Contributor at Forbes, and co-founder of the Forbes Straight Talking Cyber video project that won the ‘Most Educational Content’ category at the 2021 European Cybersecurity Blogger Awards.
Davey has also picked up many other awards over the years, including the Security Serious ‘Cyber Writer of the Year’ title in 2020. As well as being the only three-time winner of the BT Security Journalist of the Year award (2006, 2008, 2010) Davey was also named BT Technology Journalist of the Year in 1996 for a forward-looking feature in PC Pro Magazine called ‘Threats to the Internet.’ In 2011 he was honoured with the Enigma Award for a lifetime contribution to IT security journalism which, thankfully, didn’t end his ongoing contributions - or his life for that matter.
You can follow Davey on Twitter @happygeek, or email him at davey@happygeek.com.
-

Tools like ChatGPT will boost cyber crime and cyber security equally
Opinion Like all tools, generative AI services like ChatGPT or GPT-4 can be used to do harm, or prevent it
By Davey Winder Published
Opinion -

Mastodon vs Twitter
In-depth If you’re thinking about leaving Elon Musk’s Twitter for Mastodon, there are several privacy-related issues to bear in mind
By Davey Winder Published
In-depth -

There's only one way to avoid credential stuffing attacks
Opinion PayPal accounts were breached last year due to a credential stuffing attack, but can PayPal avoid taking responsibility?
By Davey Winder Published
Opinion -

What is attack surface management?
In-depth Instigate attack surface management to anticipate where cyber attackers might strike and avoid falling prey
By Davey Winder Published
In-depth -

What is spell-jacking?
In-depth Spell-jacking vulnerabilities are threatening to unwittingly leak data to third parties, undermining any drive to protect privacy
By Davey Winder Published
In-depth -

Lab-based cyber attacks are no serious threat – yet
Opinion There’s no need to fret when it comes to research-based cyber security threats, but the future is a different matter
By Davey Winder Published
Opinion -

How to react to a data breach
In-depth Every business should have a data breach response plan, but when building one it can be difficult to know where to start
By Davey Winder Last updated
In-depth -

The rising tide of no-hook phishing
In-depth Not all phishing attacks rely on links or attachments, which means you’ll have to be extra careful
By Davey Winder Published
In-depth -

Six cyber security holes you need to plug now
In-depth We shine a light on the easily overlooked cyber cracks that can turn into major sinkholes exposing your business
By Davey Winder Last updated
In-depth -
The sooner the FIDO Alliance can shut down passwords, the better
Opinion Passwords aren’t going anywhere, but that hasn’t stopped the dream of a passwordless future – and it seems that Apple, Google and Microsoft agree
By Davey Winder Published
Opinion -

Google’s Project Zero is frightening and reassuring in equal measure
Opinion This crack team of security researchers are doing work we should all be grateful for
By Davey Winder Published
Opinion -

Brave pushes the boundaries of privacy by design
Opinion It’s quite a big step to abandon the big three of Chrome, Edge and Safari for a niche option that doesn’t just tack privacy on top
By Davey Winder Published
Opinion -

QR codes are just as insecure as anything else
Opinion A browser locked down tighter than a duck’s derriere won’t save you from phishing attacks – but getting to grips with the latest advice and best practice might
By Davey Winder Published
Opinion -

How secure is Gmail?
Tutorials The practical steps you should take to secure your Gmail account, from implementing 2FA to performing regular checkups
By Davey Winder Published
Tutorials -

Using Google Takeout to reclaim your data
In-depth Everyone knows your data drives the Google machine, but now you can find out exactly what it holds on you
By Davey Winder Published
In-depth -

Vulnerability hunters are cut from a different cloth – they’re naturally inquisitive
Opinion So, you want to be a hacker? We share the best advice and resources for getting started
By Davey Winder Published
Opinion -

DDoS attacks are still a key weapon for corporate extortion
In-depth Ransomware isn’t the only rotten fruit, with DDoS attacks deployed both as an extra twist of the knife – and on their own
By Davey Winder Published
In-depth -

Skip the three words thing, go straight for the ‘use a password manager, dammit’ jugular
Opinion Why you can do so much better than the three-random-word rule that’s still being churned out by the NCSC
By Davey Winder Published
Opinion -
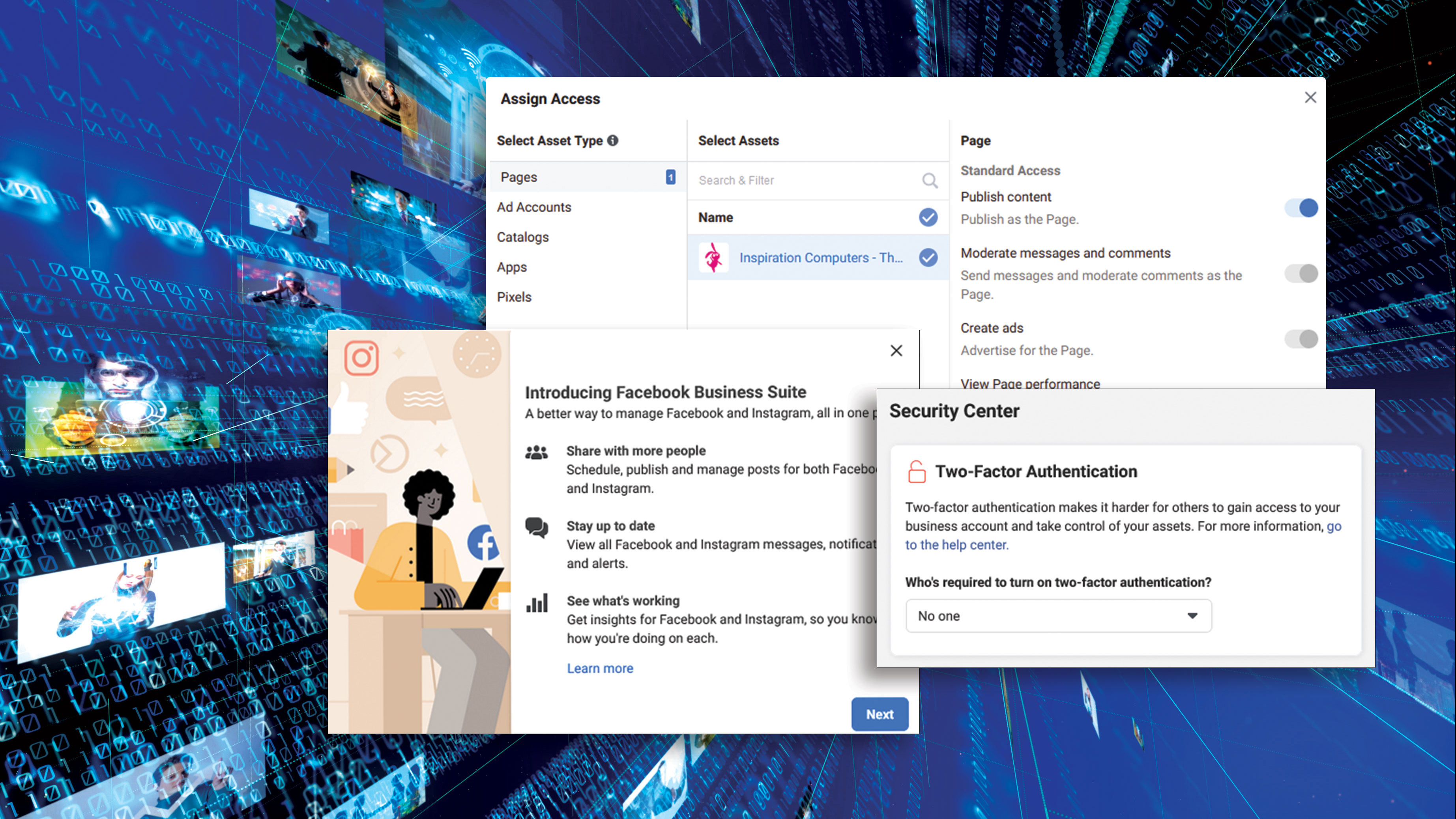
Facebook for business: know the risks
In-depth The social media giant has some great features for businesses, but there are hazards too
By Davey Winder Published
In-depth -

The truth about ransomware
In-depth Data-stealing malware can bring the biggest business to its knees – but what is the real ransomware risk, and how do you safeguard against it?
By Davey Winder Last updated
In-depth -

Secure your Wi-Fi against hackers in 10 steps
In-depth Lock down your Wi-Fi network and find devices that are stealing your bandwidth – and, potentially, your data
By Davey Winder Last updated
In-depth -

What is NoOps?
In-depth There are numerous approaches to in-house development; we explore one that focuses squarely on efficiency
By Davey Winder Published
In-depth -

Why and how I enrolled in Google’s Advanced Protection Program
In-depth Physical security keys are at the heart of the company’s efforts to protect high-profile targets
By Davey Winder Published
In-depth -

Remote support is a fact of life…
In-depth Now you need to deal with the security risk
By Davey Winder Published
In-depth
