FBI and Justice Department accuse Apple of stalling terrorist probe
US government found al Qaeda connections on terrorist’s iPhone without Apple’s help

US law enforcement officials have accused Apple of stalling an investigation into a Saudi aviation student who killed three people at a Florida Naval base last year.
Second Lt. Mohammed Alshamrani, a member of the Saudi air force, had been communicating with al Qaeda operatives for years. The discovery was made using information recovered from his two iPhone devices.
Officials have since accused Apple of stalling the probe by refusing to unlock the shooter’s devices.
What makes the iPhone a business phone? The iPad and apps: Can the tablet top the iPhone? Is Orange's network fit for the iPhone? The iPhone 4G: What to expect
Ultimately, the FBI had to bypass Apple’s security features to access the information on the gunman’s phones. The information uncovered on the devices led to a counterterrorism operation against Abdullah al-Maliki, an associate of Alshamrani, Attorney General William Barr said. Unfortunately, Apple was of little help during the FBI’s investigations.
“We received effectively no help from Apple," FBI director Christopher Wray stated during a news conference, adding that the struggle to unlock the encrypted devices caused months-long delays and jeopardized public safety.
Apple, on the other hand, disagrees with Barr and the FBI’s assessment.
“The false claims made about our company are an excuse to weaken encryption and other security measures that protect millions of users and our national security,” Apple shared in a statement provided to The Wall Street Journal.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“It is because we take our responsibility to national security so seriously that we do not believe in the creation of a backdoor—one which will make every device vulnerable to bad actors who threaten our national security and the data security of our customers.”
Despite its condemnations of the company, the Justice Department is no closer to convincing Apple to provide backdoor access to its tech. At this time, Barr and Wray have also declined to comment on how they unlocked the devices.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses
-
 Android bug prevents users from calling emergency services
Android bug prevents users from calling emergency servicesNews Google has confirmed that the glitch is affecting devices that have Microsoft Teams installed
-
 BlackBerry thwarts mobile phishing attacks with new AI tools
BlackBerry thwarts mobile phishing attacks with new AI toolsNews The company's Protect Mobile platform alerts users to potential malware before a link is clicked
-
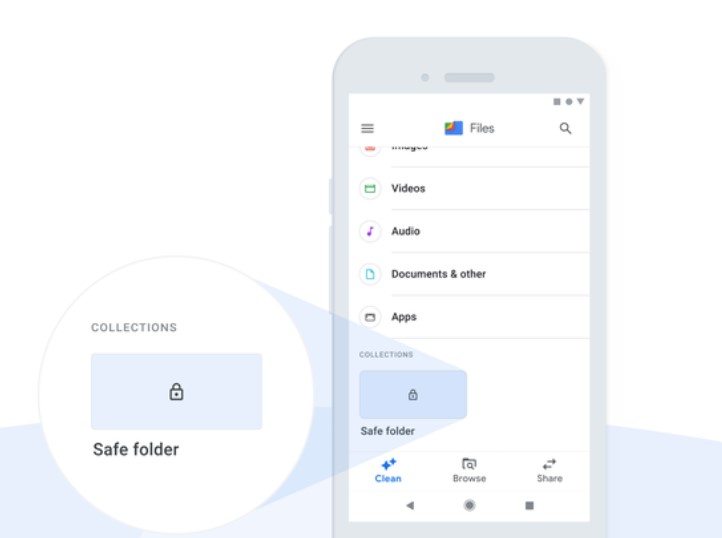 Secure files on your smartphone with Google Safe Folder
Secure files on your smartphone with Google Safe FolderNews Automatically locks itself once you navigate from the app
-
 Apple is tracking iPhones stolen by looters
Apple is tracking iPhones stolen by lootersNews Firm is using GPS technology to track and disable devices that were stolen from Apple Stores
-
 Nokia 9 PureView fingerprint scanner 'can be fooled with a packet of gum'
Nokia 9 PureView fingerprint scanner 'can be fooled with a packet of gum'News The latest software update has seemingly exacerbated pre-existing issues with Nokia's biometric security
-
 Security is the main concern for business smartphone deployment
Security is the main concern for business smartphone deploymentNews HMD research also finds the majority of large companies use outdated devices
-
 Apple's 'USB Restricted Mode' closes security loophole on locked iPhones, thwarting police data extraction
Apple's 'USB Restricted Mode' closes security loophole on locked iPhones, thwarting police data extractionNews The new software feature will by default protect against iPhone-hacking tool GrayKey
-
 BlackBerry Motion review: Running in place?
BlackBerry Motion review: Running in place?Reviews A functional, no-frills phone with little to entice