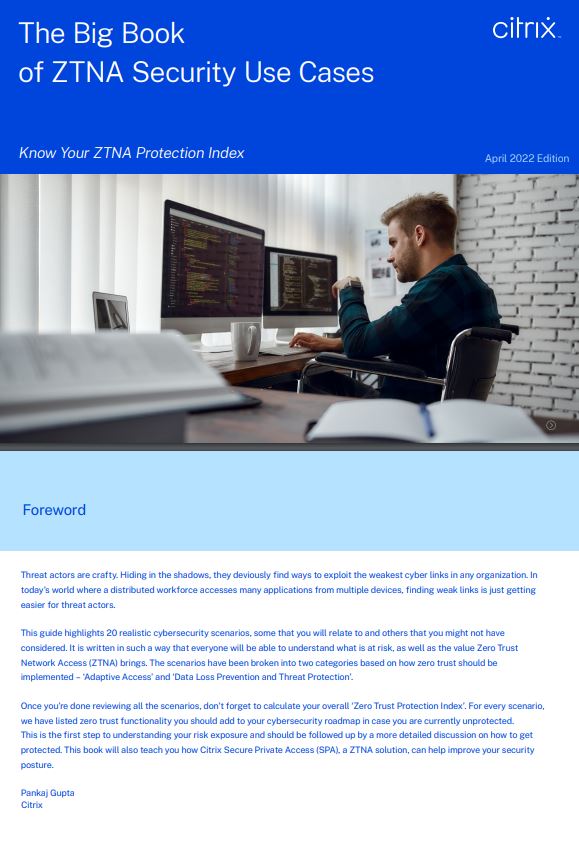
The big book of ZTNA security use cases
Know your ZTNA protection index

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
In a new hybrid world of work, distributed workforces and remote access points to business networks are prime targets for cybercriminals, looking to exploit the weakened security measures of multiple unmanaged devices.
This guide shares relatable cyber security breach examples, highlighting key areas at risk, and how Zero Trust security measures could reduce risk exposure and support your current cyber security measures.
Download this white paper now to fully understand your own risk exposure, and learn why additional protection measures—including zero-trust architectures—are critical to stop data breaches.
Provided by

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
ITPro is a global business technology website providing the latest news, analysis, and business insight for IT decision-makers. Whether it's cyber security, cloud computing, IT infrastructure, or business strategy, we aim to equip leaders with the data they need to make informed IT investments.
For regular updates delivered to your inbox and social feeds, be sure to sign up to our daily newsletter and follow on us LinkedIn and Twitter.
-
 DIY hackers are turning to ‘flat-pack’ malware components to speed up attacks and cut costs
DIY hackers are turning to ‘flat-pack’ malware components to speed up attacks and cut costsNews While these malware campaigns are very basic, researchers noted “they still work”
-
 Russian DDoS: what’s the threat to businesses?
Russian DDoS: what’s the threat to businesses?In-depth The UK National Cyber Security Centre (NCSC) has issued a warning that Russian-aligned hacktivist groups are targeting organizations
-
 IDC InfoBrief: Sustainability doesn’t need to be all stick and no carrot
IDC InfoBrief: Sustainability doesn’t need to be all stick and no carrotwhitepaper CIOs are facing two conflicting strategic imperatives
-
 Untethered: How CIOs and CISOs are paving the way for the new hybrid workforce
Untethered: How CIOs and CISOs are paving the way for the new hybrid workforceWhitepaper Effective techniques to transition from exposed legacy infrastructure to an effective zero trust strategy
-
 Delivering fast and secure digital experiences for the modern hybrid workforce
Delivering fast and secure digital experiences for the modern hybrid workforceWhitepaper A new approach to digital experience monitoring that can monitor the health of all systems
-
 More than a number: Your risk score explained
More than a number: Your risk score explainedWhitepaper Understanding risk score calculations
-
 Rushing digital transformation will create cyber security ‘bear traps’ – here’s how to avoid them
Rushing digital transformation will create cyber security ‘bear traps’ – here’s how to avoid themIn-depth Although digital transformation brings many benefits, rushing projects may result in unforeseen cyber security risks
-
 Employees are choosing how they work
Employees are choosing how they workWhitepaper And with the right secure digital strategy, this could be a great thing for your business: today and far into the future
-
 Creating a proactive, risk-aware defence in today's dynamic risk environment
Creating a proactive, risk-aware defence in today's dynamic risk environmentWhitepaper Agile risk management starts with a common language
-
 A guide to ESG reporting frameworks
A guide to ESG reporting frameworksWhitepaper Guidelines to assist with your approach to ESG reporting
