Bristol City Council launches phishing attacks against own staff
Colleagues are being targeted by spoof ‘spam’ emails that link to cyber security training


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Staff at Bristol City council have unleashed a wave of spoof phishing attacks on their own colleagues as part of wider efforts to bolster the organisation's cyber resilience.
The council's cyber security risk is considered "higher than should be expected", according to a report recently prepared for the organisation's resources scrutiny committee.
The reasons for this cited include a lack of investment in appropriate technologies, reliance on in-house expertise and self-assessments, alongside a lack of formal approach to risk management, and a historic lack of focus.
As a result, the council has taken the extraordinary step of targeting its own staff through a phishing attack exercise, in which IT staff are sending emails to staff to see how users react to this form of cyber attack.
Anybody who succumbs to one of these council-borne phishing emails will be redirected towards targeted training via a link, the report said. The outcome of this exercise will then inform how the council improves its non-technical controls and training in future.
"Like all organisations, we face increasingly sophisticated and varying threats to our digital systems," a Bristol City Council spokesperson told IT Pro.
"This report provides assurance that of the threats we are aware of, measures are in place to maintain the security of our systems.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
"We continue to work closely with a range of organisations to ensure our systems can effectively respond to the risk of cyber- attacks and that all data remains safe and secure."
The resources scrutiny committee oversees Bristol City council's digital transformation programme and IT infrastructure, as well as back-office functions like finance and human resources.
Its members were updated on the council's increased cyber security threat, among other risks being monitored, for the third quarter of 2018/19 at a meeting in late February.
The council's novel strategy to combat cyber threats makes sense in the context that employees themselves are often considered a threat to any organisation's cyber resilience. Analysis by Coalfire, for instance, demonstrated that human error was the weakest security link in an organisation given the prevalence of phishing attacks.
Although Bristol City Council's cyber security risk had been deemed 'red' for the last four quarters, this consistently scored "3x5=15" using the council's own metric - where '3' on a scale of one to four is likelihood and '5' on a scale of one to seven is the impact.
But the risk increased to '3x7=21' for the last three months of 2019. This means while the likelihood of the council suffering an attack has remained the same, the potential fallout of any cyber threat is now considered much greater.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 What might cause the 'AI bubble' to burst?
What might cause the 'AI bubble' to burst?In-depth If a bubble is really forming, what happens to the businesses caught up in the AI craze when it pops – and why things might not be as bad as they seem
-
 London set to host OpenAI's largest research hub outside US
London set to host OpenAI's largest research hub outside USNews OpenAI wants to capitalize on the UK’s “world-class” talent in areas such as machine learning
-
 C-suites consider quantum a serious threat and "amazing" deepfake attacks are just 'months away'
C-suites consider quantum a serious threat and "amazing" deepfake attacks are just 'months away'News Deepfake technology has matured at a rapid rate, and video scams are likely to be a on par with the more convincing voice-only campaigns very soon, one expert says
-
 Shiseido reportedly suffers data breach
Shiseido reportedly suffers data breachNews The Japanese cosmetics company has been accused of failing to notify affected staff of the leak
-
 Almost a quarter of all spam emails were sent from Russia in 2021
Almost a quarter of all spam emails were sent from Russia in 2021News Last year's spam emails mostly centred around money and investment, Bond and Spider-Man movie premieres, and the pandemic
-
 HMRC issues scam warning ahead of Self Assessment deadline
HMRC issues scam warning ahead of Self Assessment deadlineNews The department stated that 2021 has already seen 797,010 tax-related scams reported
-
 Ofcom report reveals alarming uptick in smishing attacks
Ofcom report reveals alarming uptick in smishing attacksNews Text-based scams now more common than phone calls among young adults
-
 Smishing attacks increased 700% in first six months of 2021
Smishing attacks increased 700% in first six months of 2021News Which? has urged businesses to play their part to protect people from text message scams
-
 Delivery scams become most common form of smishing
Delivery scams become most common form of smishingNews Cyber security provider Proofpoint finds a major increase in the number of threat actors impersonating postal services
-
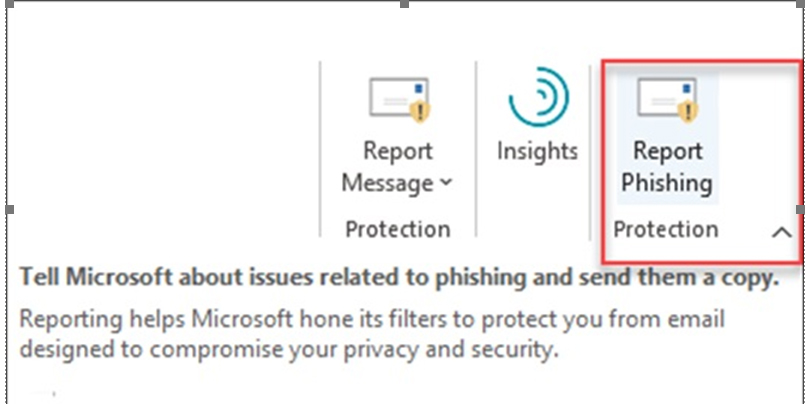 NCSC simplifies Outlook scam-reporting tool
NCSC simplifies Outlook scam-reporting toolNews Users are now able to report phishing emails with just one click