Ukrainian ethical hackers targeted by Russian malware attacks
Cisco Talos researchers say the IT Army of Ukraine's Telegram channel is being hit with malicious links


Cyber criminals are preying on ethical hackers supporting the IT Army of Ukraine by deceiving them into downloading information-stealing malware.
Opportunistic cyber criminals are posing as genuine representatives of the IT Army of Ukraine and pretending to provide them with tools to deliver distributed denial of service attacks (DDoS) that ultimately turn out to be malware, according to researchers at Cisco Talos.
The IT Army of Ukraine is a group that mobilise via the Telegram platform and was originally assembled at the start of the conflict by a Ukrainian Minister to recruit as many supporters as possible to fight Russia in cyber space.
The group currently has more than 300,000 members and posts daily ‘hit lists’ - lists of target .ru URLs for tech-savvy supporters of Ukraine to knock offline. Recent targets include Russian electronic signature services and importers of technology for the Russian military.
Criminals are targeting these ethical hackers using Telegram channels that are seemingly related to the real IT Army of Ukraine group, but are not genuine.
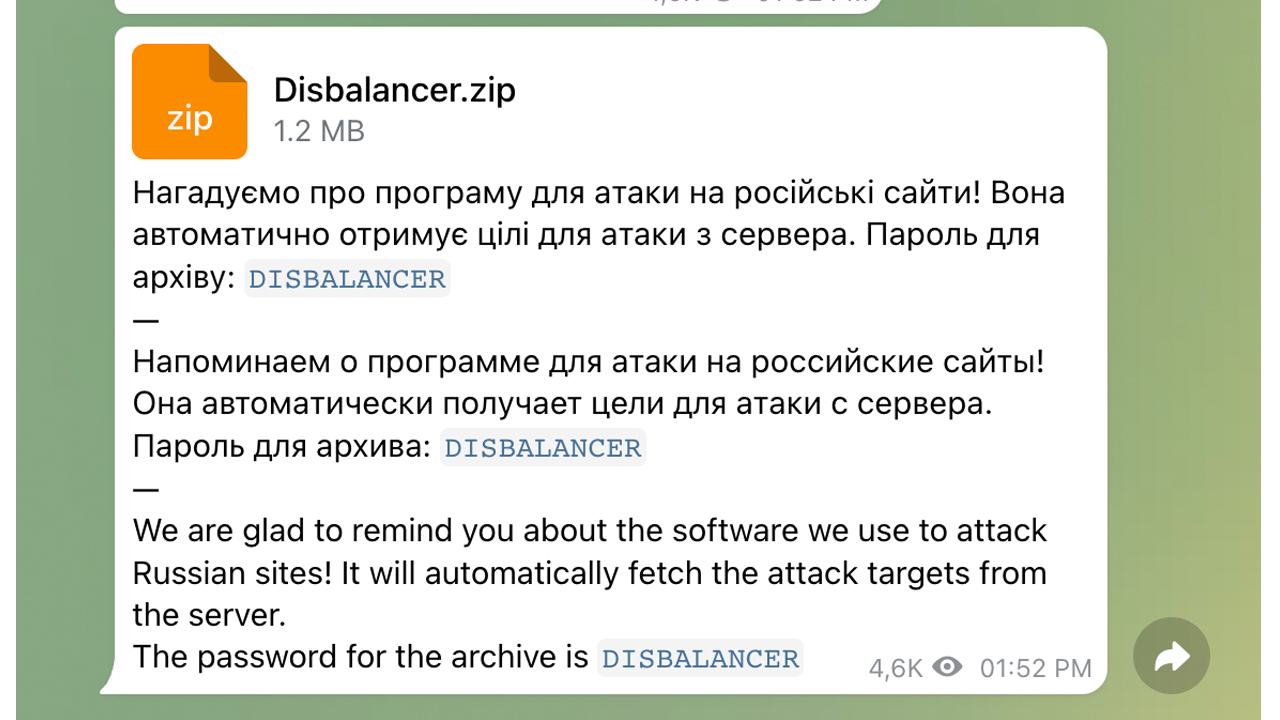
Cisco Talos researchers saw cases of adverts for inauthentic versions of genuine DDoS tools, such as the real Disbalancer Liberator tool, which when clicked infect the user's system with information-stealing malware that harvests credentials and cryptocurrency information.
The information stealer gleans information from browsers such as Chrome and Firefox, and scans other locations on the file system for key information before relaying it back to a Russian IP address.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“This is an example of one of the many ways opportunistic cybercriminals are attempting to take advantage of the Russian invasion by exploiting sympathisers on both sides of the conflict,” the researchers said.
RELATED RESOURCE

Edge to cloud security: A new WAN and security edge
A practical guide to adopting a secure access service edge (SASE) architecture
“Such activity could take the form of themed email lures on news topics or donation solicitations, malicious links purporting to host relief funds or refugee support sites, malware masquerading as security defensive or offensive tools, and more. Users must carefully inspect suspicious emails before opening them and validate software or other files before downloading them.”
Cisco Talos said evidence suggests the threat actors behind the campaign have been distributing infostealers since “at least November 2021” but have now pivoted to targeting hacktivists siding with Ukraine.
It also said it expects the information-stealing activity to continue and diversify as the global interest in the conflict creates a potentially massive pool of targets for threat actors to prey on.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Morgan Stanley research warns AI is having a huge impact on jobs
Morgan Stanley research warns AI is having a huge impact on jobsNews Analysis of five sectors highlights an "early warning sign" of AI’s impact on jobs
-
 AI is “forcing a fundamental shift” in data privacy and governance
AI is “forcing a fundamental shift” in data privacy and governanceNews Organizations are working to define and establish the governance structures they need to manage AI responsibly at scale – and budgets are going up
-
 Why the Space Force wants white hats to attack a satellite
Why the Space Force wants white hats to attack a satelliteCase study Authorities hope the first-of-its-kind competition could bring benefits to the cyber sector
-
 OpenAI to pay up to $20k in rewards through new bug bounty program
OpenAI to pay up to $20k in rewards through new bug bounty programNews The move follows a period of unrest over data security concerns
-
 New ‘DarkBit’ ransomware gang shuts down Technion, demands $1.7 million ransom
New ‘DarkBit’ ransomware gang shuts down Technion, demands $1.7 million ransomNews A politically charged ransom note suggests DarkBit are one of the newest hacktivist gangs to emerge in recent months
-
 Research: Luxury cars and emergency services vehicles vulnerable to remote takeover
Research: Luxury cars and emergency services vehicles vulnerable to remote takeoverNews A "global API issue" has been highlighted through months-long research into brands such as Ferrari and Mercedes-Benz, leaving owners open to hacking, account takeovers, and more
-
 Podcast transcript: Meet the cyborg hacker
Podcast transcript: Meet the cyborg hackerIT Pro Podcast Read the full transcript for this episode of the IT Pro Podcast
-
 The IT Pro Podcast: Meet the cyborg hacker
The IT Pro Podcast: Meet the cyborg hackerIT Pro Podcast Resistance is futile - offensive biotech implants are already here
-
 SpaceX bug bounty offers up to $25,000 per Starlink exploit
SpaceX bug bounty offers up to $25,000 per Starlink exploitNews The spacecraft manufacturer has offered white hats immunity to exploit a wide range of Starlink systems, with a dedicated report page
-
 Nomad happy to forgive hackers if they return 90% of $190 million that was stolen
Nomad happy to forgive hackers if they return 90% of $190 million that was stolenNews The crypto bridge is offering 'white hat hackers' a 10% bounty following the attack earlier this week