Nvidia confirms data breach as hackers make additional demands
Nvidia has confirmed a rumoured hack on its systems for the first time as the first part of the alleged 1TB of company secrets is made available to download


Nvidia has confirmed the LAPSU$ hacking group successfully breached its systems and that previously unconfirmed reports that the group stole company data are true.
The chipmaker debunked the rumours that ransomware was involved in the security incident and made it clear the hack was in no way related to the current conflict between Russia and Ukraine.
Nvidia previously stated that it was investigating an incident but did not confirm the hack had actually taken place.
“On February 23, 2022, Nvidia became aware of a cyber security incident which impacted IT resources,” said an Nvidia spokesperson to IT Pro. “Shortly after discovering the incident, we further hardened our network, engaged cyber security incident response experts, and notified law enforcement.
“We have no evidence of ransomware being deployed on the Nvidia environment or that this is related to the Russia-Ukraine conflict. However, we are aware that the threat actor took employee credentials and some Nvidia proprietary information from our systems and has begun leaking it online. Our team is working to analyse that information.
“We do not anticipate any disruption to our business or our ability to serve our customers as a result of the incident. Security is a continuous process that we take very seriously at Nvidia – and we invest in the protection and quality of our code and products daily.”
LAPSU$ goes public
The LAPSU$ hacking group has been providing regular, candid updates on its operation via its Telegram channel and on Tuesday, it posted download links for the first part of the 1TB cache of documents it said it stole from Nvidia.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
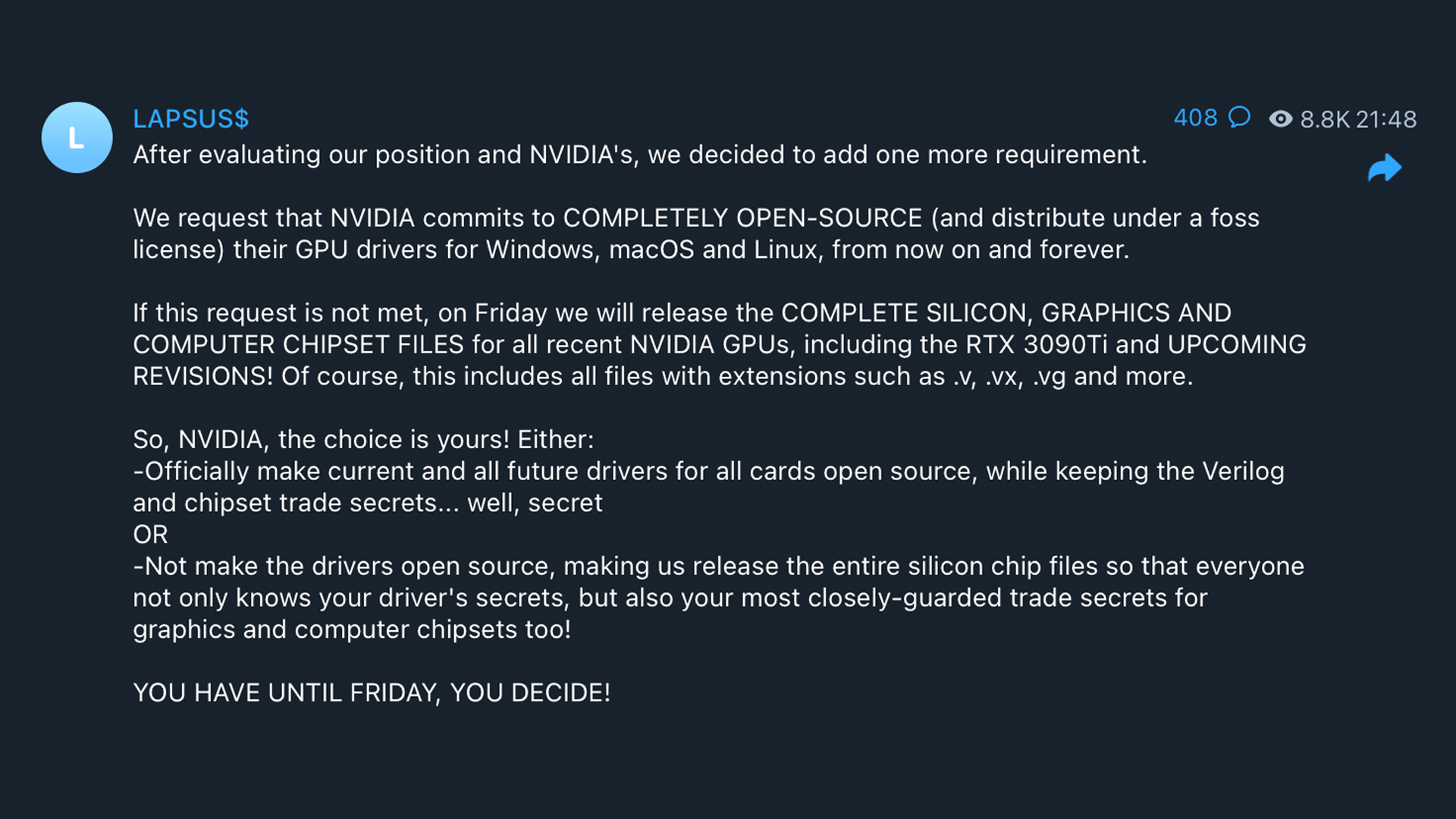
The most recent update shared by the group, posted late Tuesday evening, was an additional requirement it wants Nvidia to honour.
“We request that NVIDIA commits to COMPLETELY OPEN-SOURCE (and distribute under a foss license) their GPU drivers for Windows, macOS and Linux, from now on and forever,” the post read.
LAPSU$ said that if Nvidia does not meet its latest demand, it will release the full set of files it has on the most recent and future models of the company’s flagship graphics cards.
The ultimatum presented to Nvidia is to make the drivers for its graphics cards open source forever or lose access to the trade secrets LAPSU$ said it has stolen from the company.
The reason for the hack, LAPSU$ said, is to help the gaming and cryptocurrency mining community. One of the key technologies on which the group claims to have information is Nvidia’s lite hash rate (LHR) - a technology that aims to reduce a graphics card’s ability to effectively mine cryptocurrency while preserving gaming performance.
RELATED RESOURCE

The best defence against ransomware
How ransomware is evolving and how to defend against it
LAPSU$ said it holds source code and other files relating to LHR but won’t release a bypass directly because they don’t want to release anything that “may brick any card”, but said “any developer with a good brain can compile what we gave you [in part 1 of the leak]”.
It also said it’s ready to sell a piece of software that could bypass LHR but they won’t sell it cheaply. Nvidia previously refused to comment on what type of data had been stolen or who was behind the hack.
LAPSU$ is using a double extortion method of operation, similar to the one that’s becoming increasingly popular with ransomware gangs. It involves compromising a victim and stealing data before encrypting their machine, threatening to leak that data if the ransom isn’t paid.
It aims to further encourage victims to pay the ransom when industry advice dictates to never pay. Europol recently said it observed an uptick in double extortion cases in the past year and Mandiant said one in seven cases results in critical data being leaked.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 CrowdStrike announces integration with Nvidia Enterprise AI Factory
CrowdStrike announces integration with Nvidia Enterprise AI FactoryNews Organizations can now leverage CrowdStrike protection within Nvidia Enterprise AI Factory deployments
-
 Nvidia drives regional sovereign data infrastructure with new partnership
Nvidia drives regional sovereign data infrastructure with new partnershipNews The Nvidia Inception program will shore up data sovereignty concerns for participating organizations
-
 Nvidia's new RTX 4090 is a powerful password-cracking tool
Nvidia's new RTX 4090 is a powerful password-cracking toolNews Hackers using an array of the consumer-grade GPU could see brute force timings halve
-
 IT Pro News In Review: Google acquires Mandiant, new Apple hardware, Lapsus$ leaks Samsung data
IT Pro News In Review: Google acquires Mandiant, new Apple hardware, Lapsus$ leaks Samsung dataVideo Catch up on the biggest headlines of the week in just two minutes
-
 IT Pro News In Review: Compromised Nvidia data, protesters boycott Russian tech, Conti data breach
IT Pro News In Review: Compromised Nvidia data, protesters boycott Russian tech, Conti data breachVideo Catch up on the biggest headlines of the week in just two minutes
-
 Hacking group leaks Nvidia data following alleged ransomware attack
Hacking group leaks Nvidia data following alleged ransomware attackNews LAPSU$ claims to have released Nvidia source code and highly confidential GPU driver data
-
 IT Pro News In Review: Nvidia breaks off Arm deal, FCDO security attack, Microsoft to disable VBA
IT Pro News In Review: Nvidia breaks off Arm deal, FCDO security attack, Microsoft to disable VBAVideo Catch up on the biggest headlines of the week in just two minutes
-
 IT Pro News in Review: Nvidia walks away from Arm, Belarusian train hack, and IBM to sell Watson Health
IT Pro News in Review: Nvidia walks away from Arm, Belarusian train hack, and IBM to sell Watson HealthVideo Catch up on the biggest headlines of the week in just two minutes

