LAPSUS$ returns with Globant breach, leaking trove of data on top global businesses
Experts analysing the data dump told of the 'immense' damage that could be caused with access to such files


The LAPSUS$ hacking group has announced another breach that has led to the source code belonging to the likes of Facebook and Apple being dumped via its Telegram channel.
The group announced the trove of data belonging to some of the world’s top companies in the early hours of Wednesday morning, days after UK law enforcement arrested a number of individuals connected with the group, with investigations still ongoing.
It’s believed the companies’ code was lifted as a result of a hack on Argentine-headquartered software development company Globant since LAPSUS$ also leaked the administrator credential for the company’s GitHub, Jira, and Confluence accounts.
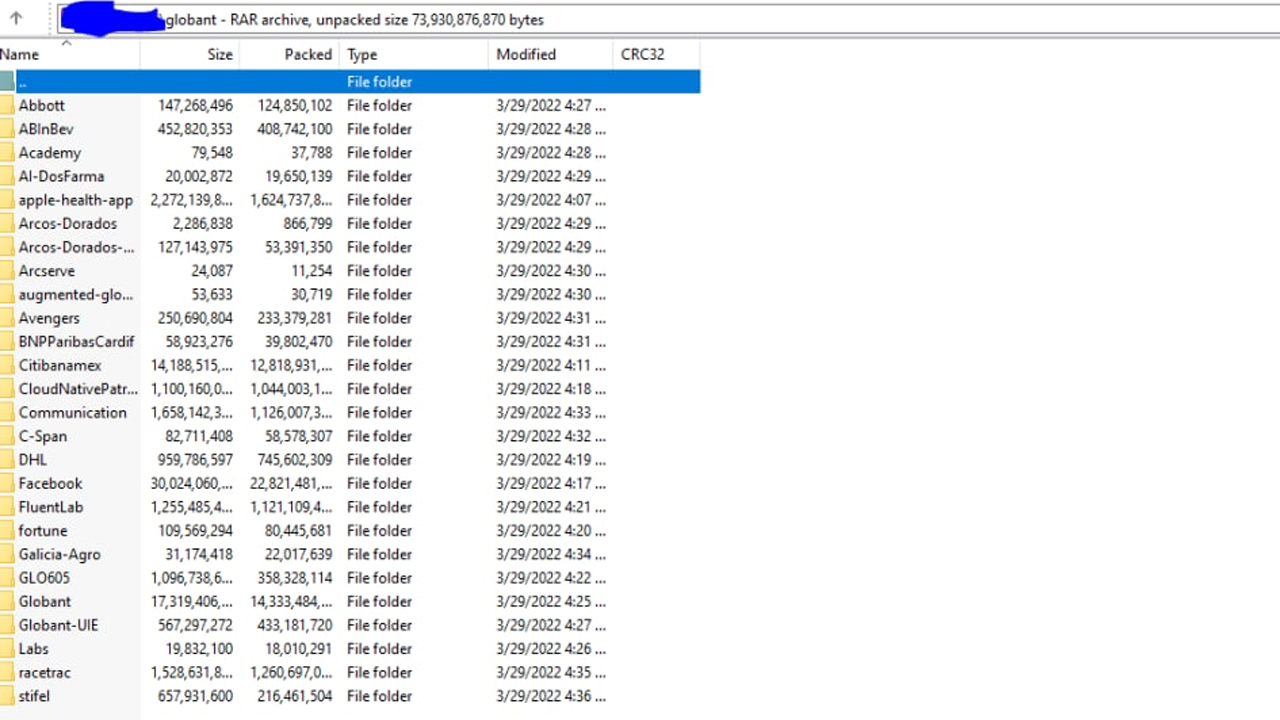
Experts have analysed the data trove and have revealed damning insights from the leaked files. Those who spoke to IT Pro said the files seemed legitimate and corroborated wider experts' views that among the leaked files were the encrypted private keys for certificates used to build iOS apps.
"From the paths I have looked at so far it looks like legitimate source code for mobile apps," said Amir Hadžipašić, CEO and founder of SOS Intelligence to IT Pro. "It looks like there are internal microsites and data for them too, CVs and other personal information.
"That's not all, they have full private keys for certs in most of the directories," he added. "That there would be enough for me to stand up a website and serve their SSL and it be valid."
"The leak appears to contain the server private keys to Globant's Azure machine templates, this could lead to a full compromise of their servers if they are accessible externally via SSH."
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Having access to such files could lead to a complete compromise of the affected companies' customer systems and make the initial entry attempt seem entirely legitimate since the authentication key itself is used.
Numerous high profile companies are affected by the data trove including Citibanamex, the Citigroup-owned bank that's the second-largest in Mexico, among other finance and technology companies.
Other companies affected by the breach include healthcare giant Abbott, beverages multinational AB InBev, BNP Paribas Cardiff, and DHL.
Globant and a number of the affected companies were also contacted by IT Pro for comment on the situation, but neither had replied at the time of publication.
Experts said Globant "is going to have a lot of work on their hands" and will likely involve the resetting of a vast number of tokens and API keys, and passwords will need to be reset and revoked.
The leaked credentials have been described as “very easily guessable and used multiple times” by malware analysis group VX-Underground.
IT Pro has seen the leaked credentials and can confirm most of the passwords would not be considered as ‘complex’ by most standards.
LAPSUS$ has demonstrated varied and changing tactics to break into companies in the cyber criminal group’s short time being active.
RELATED RESOURCE

Identity is key to stopping these five cyber security attacks
Many attacks begin with the same weakness: user accounts
Previously confused as a ransomware group, LAPSUS$ is described by Microsoft as large-scale social engineering and extortion campaign. The group is financially motivated and has been observed destroying victim files or leaking them online to the public.
Social engineering and using initial access brokers have typically been the go-to methods of gaining an initial foothold in their victims’ environments, connecting via remote or virtual desktop infrastructure and elevating privileges from there.
The same method was observed in its most recent hack on Sitel which drew headlines due to data from identity and access management company Okta being leaked as a result, leaked cyber security reports showed.
With its first activity observed in December 2021, LAPSUS$ has claimed successful cyber attacks on Nvidia, Okta, Samsung, LG, and more, including Brazilian government entities.
The group is believed to have members based across the UK and Brazil primarily, with their ages ranging from late teens to early twenties.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 WatchGuard Firebox T185 review
WatchGuard Firebox T185 reviewReviews The Firebox T185 offers a superb range of security measures, smart cloud management, and good performance at a competitive price point
-
 Why digital resilience now belongs in the channel boardroom
Why digital resilience now belongs in the channel boardroomIndustry Insights Digital technologies are placing increased responsibility on channel boardrooms