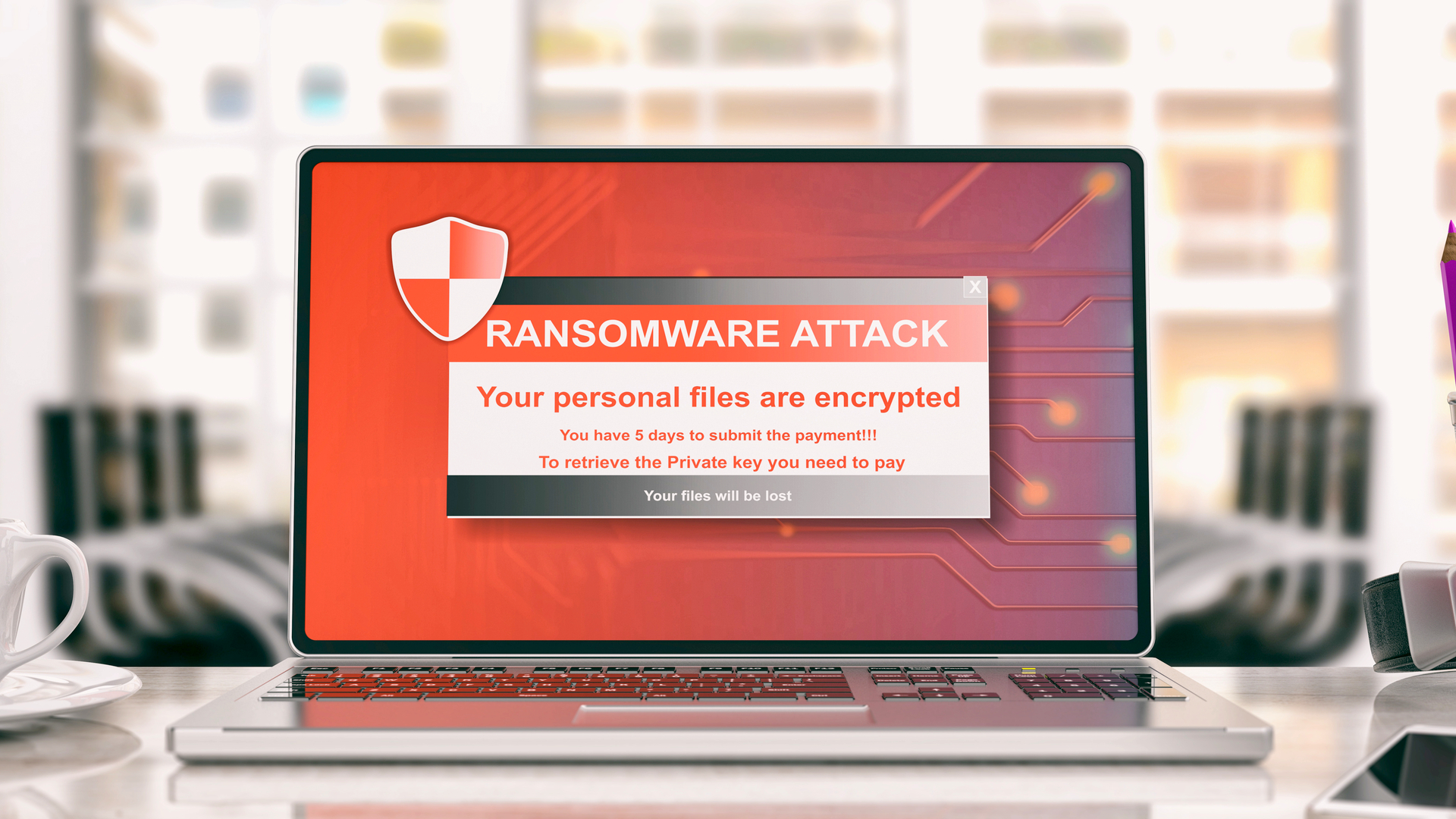
Microsoft issues warning about new PonyFinal ransomware attacks
PonyFinal attackers “looking for targets of opportunity," says Misner
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Microsoft Security Intelligence posted a series of tweets urging companies to implement protections against PonyFinal, a new ransomware that’s been active for the last two months.
PonyFinal, according to Microsoft Security Intelligence, is not an automated threat. Rather, it has humans pulling its reins. Hackers must manually propagate the ransomware via an MSI file containing two batch files and the ransomware payload.
Per the experts, PonyFinal uses a secure encryption scheme, meaning that encrypted files can’t be recovered either. Unfortunately, Microsoft says, these attackers have compromised their targets for several months and been patiently waiting for the perfect opportunity to monetize their cyberattacks.
“PonyFinal is at the tail end of protracted human-operated ransomware campaigns that are known to stay dormant and wait for the most opportune time to deploy the payload,” a tweet from Microsoft Security Intelligence reads.
"These attackers are looking for targets of opportunity," Phillip Misner, Security Program Manager at Microsoft explained in an interview with Dark Reading.
Misner added that PonyFinal operators don’t discriminate when it comes to choosing targets either. PonyFinal has already targeted victims in the U.S., India and Iran. It’s taken aim at the health care and financial sectors specifically.
“So far, the attacks have affected aid organizations, medical billing companies, manufacturing, transport, government institutions and educational software providers, showing that these ransomware groups give little regard to the critical services they impact, global crisis notwithstanding,” researchers explained in April. “These attacks, however, are not limited to critical services, so organizations should be vigilant for signs of compromise.”
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Human-operated ransomware like PonyFinal is nothing new. Ransomware similar to PonyFinal has been growing more popular as attackers try to maximize ransom from individual targets. Other human-operated ransomware campaigns similar to PonyFinal include Bitpaymer, Ryuk, REvil and Samas.
-
 AWS CEO Matt Garman isn’t convinced AI spells the end of the software industry
AWS CEO Matt Garman isn’t convinced AI spells the end of the software industryNews Software stocks have taken a beating in recent weeks, but AWS CEO Matt Garman has joined Nvidia's Jensen Huang and Databricks CEO Ali Ghodsi in pouring cold water on the AI-fueled hysteria.
-
 Deepfake business risks are growing
Deepfake business risks are growingIn-depth As the risk of being targeted by deepfakes increases, what should businesses be looking out for?
-
 Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoing
Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoingNews Thousands of attacker servers all had the same autogenerated Windows hostnames, according to Sophos
-
 Google issues warning over ShinyHunters-branded vishing campaigns
Google issues warning over ShinyHunters-branded vishing campaignsNews Related groups are stealing data through voice phishing and fake credential harvesting websites
-
 The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwise
The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwiseNews Billing itself as the “only place ransomware allowed", RAMP catered mainly for Russian-speaking cyber criminals
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement