Ransomware groups are using media coverage to coerce victims into paying
Threat actors are starting to see the benefits of a more sophisticated media strategy for extracting ransoms


Ransomware gangs are leveraging media coverage of attacks to pile pressure on victims to meet their demands, according to new research.
Analysis from Sophos X-Ops has highlighted the increasingly close relationship between ransomware groups and the media, suggesting that while hackers are traditionally secretive, some now see the potential in using their publicity to enhance extortion techniques.
Victims may be concerned about the reputational damage they might suffer if the data or sensitive information was seized, or even the fines they could incur from bodies such as the Information Commissioner’s Office (ICO) for failing to prevent a data breach.
Sophos X-Ops said some hacking groups are explicit about promoting attacks via media channels to serve as a warning to victims.
The study specifically pointed to the Dunghill ransomware gang, which threatened to “send the data to all interested supervisory organizations and the media” if their demands were not met.
In addition to using media coverage to ratchet up pressure on victims, threat actors are also making use of press coverage to generate positive publicity and boost recruitment, according to Sophos X-Ops’ research.
Ransomware gangs are aware of the coverage of their activities and have been observed to publicly correct outlets who are inaccurate in their reporting, the study noted.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Sophos X-Ops said the trend points toward a concerted effort among some ransomware groups to develop a media strategy in an attempt to professionalize and commodify their image.
Some have been found to publish press-releases and refine their branding to boost credibility with victims and journalists alike. Others, such as Vice Society, have even promoted content listing them as a 'top ransomware group'.
Although increased publicity does also mean ransomware groups are exposed to a higher risk of law enforcement scrutiny, it also adds weight to their threats of leaking sensitive information.
Ransomware groups target better media relations
RELATED RESOURCE

Discover how you can safeguard your organization against ransomware attacks with a zero trust strategy
DOWNLOAD NOW
Sophos X-Ops’ investigation shows threat actors’ attitudes towards the media are shifting with the majority of groups covered in its analysis displaying a marked turn towards collaborating with the media on their public image.
Some ransomware groups granted interviews to journalists in which they shed a positive light on their activities in what may be an attempt to drive recruitment, according to Sophos X-Ops.
The RansomHouse group, for example, features a message on its leak site that directly addresses journalists, offering to share information through a PR channel on Telegram before it is officially published.
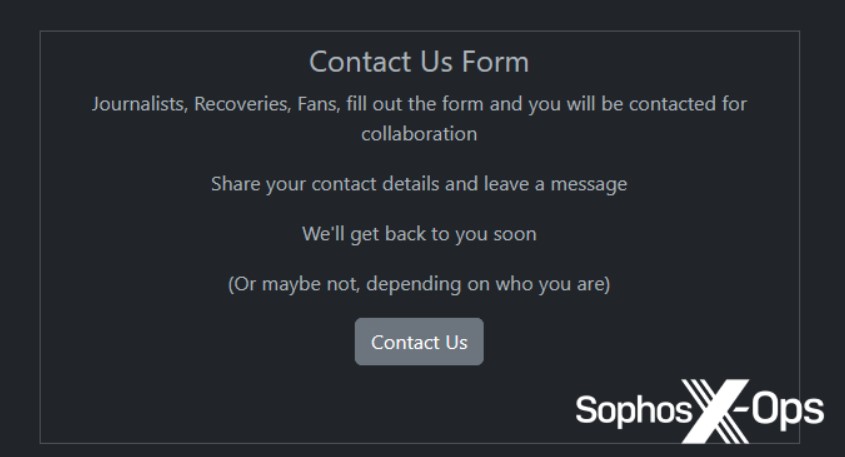
Prominent ransomware group Rhysida’s contact form lists journalists before recoveries on its contact form, suggesting its interest in shaping its public image comes before extracting ransoms from its victims.
Some ransomware gangs are frustrated by media coverage
These groups are not completely embracing the media’s coverage of their attacks, however, with some groups becoming increasingly belligerent towards outlets and journalists deemed to have misreported on incidents involving them.
ALPHV/BlackCat, for example, released a 1,300-word blog post on its leak site criticizing publications for failing to check sources and publishing false information.
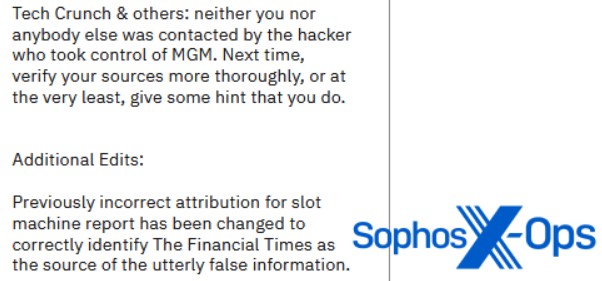
Cl0p were also found to be hostile towards media organizations, appearing to resent outlets challenging the narrative constructed through their own disclosures.
The BBC was called out by Cl0p for misrepresenting the information supplied by the group, who stated “the only story is we want money for our work. If we have your business files you have to pay”.

Solomon Klappholz is a former staff writer for ITPro and ChannelPro. He has experience writing about the technologies that facilitate industrial manufacturing, which led to him developing a particular interest in cybersecurity, IT regulation, industrial infrastructure applications, and machine learning.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses
-
 Ransomware victims are getting better at haggling with hackers
Ransomware victims are getting better at haggling with hackersNews While nearly half of companies paid a ransom to get their data back last year, victims are taking an increasingly hard line with hackers to strike fair deals.
-
 96% of SMBs are missing critical cybersecurity skills – here's why
96% of SMBs are missing critical cybersecurity skills – here's whyNews The skills shortage hits SMBs worse as they often suffer from a lack of budget and resources
-
 Sophos Firewall Virtual review: Affordable network protection for those that like it virtualized
Sophos Firewall Virtual review: Affordable network protection for those that like it virtualizedReviews Extreme network security that's cheaper than a hardware appliance and just as easy to deploy
-
 MSPs are struggling with cyber security skills shortages
MSPs are struggling with cyber security skills shortagesNews A shortage of tools and difficulties keeping pace with solutions were also ranked as key issues for MSPs
-
 Nearly 70 software vendors sign up to CISA’s cyber resilience program
Nearly 70 software vendors sign up to CISA’s cyber resilience programNews Major software manufacturers pledge to a voluntary framework aimed at boosting cyber resilience of customers across the US
-
 Sophos and Tenable team up to launch new managed risk service
Sophos and Tenable team up to launch new managed risk serviceNews The new fully managed service aims to help organizations manage and protect external attack surfaces
-
 History tells us ALPHV will likely recover from recent takedown
History tells us ALPHV will likely recover from recent takedownNews A number of cyber criminal outfits have recovered from police takedowns in recent years, but that doesn’t mean authorities should stop trying
-
 ALPHV leak site seized by law enforcement as decryption tool released
ALPHV leak site seized by law enforcement as decryption tool releasedNews The ALPHV takedown as been described as a "huge win" for law enforcement