Magika, Google's new AI security tool, helps users identify malware at rapid speed - and it's free to access on GitHub
Google hopes its Magika AI security tool will rapidly accelerate malicious file identification, but there are some limitations, according to industry experts


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Google has unveiled the launch of 'Magika', a new AI-powered file identification tool designed to track down and identify malicious files and correspondence in a bid to tackle growing malware threats.
The tool, which Google confirmed will be open sourced, is a custom deep-learning model able to complete “precise file identification” within milliseconds, even when running on a CPU.
Magika outperforms other existing file detections systems by about 20% when evaluated on a 1M files benchmark encompassing over 100 file types, according to Google.
Similarly the tool performs well on textual files, including code files and configuration files, which other tools have traditionally struggled with.
For Melissa Ruzzi, it's another tool in the armory of those who have a stake in the cyber security landscape.
“AI can help improve security by finding patterns and analyzing data much faster than any human can,” Melissa Ruzzi, director of AI at SaaS security company AppOmni, told ITPro.
“With the constant growth in complexity and volume of attacks, humans need the help from AI to keep up,” she added.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
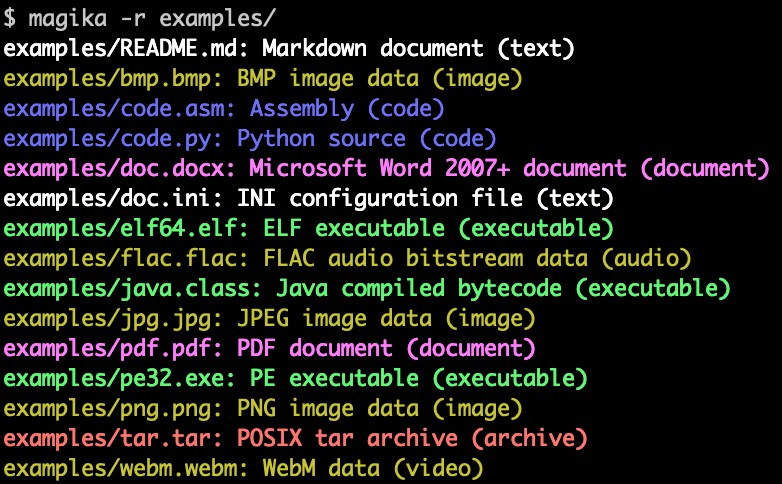
Magika can identify a varied set of files
This new AI offering has already been rolled out internally, according to Google - and so far the results have been promising. Users have reported an improvement of 50% in file identification accuracy based on a weekly average of “hundreds of billions of files” compared to its previous system of file identification.
It’s allowed the tech giant to scan 11% more files and reduce the number of unidentified files to 3%.
"Internally, Magika is used at scale to help improve Google users’ safety by routing Gmail, Drive, and Safe Browsing files to the proper security and content policy scanners," the company said in a blog post.
There are certain limitations to the tool, however. The current threat landscape is varied and companies are often vulnerable on a dizzying amount of levels. As Ruzzi was careful to point out, Magika isn’t going to be a quick fix for every threat out there.
“This is not a silver bullet – a lot of other entry points, like stolen credentials and vulnerabilities, will still be present,” Ruzzi said.
“Attackers often move laterally -- they first steal private credentials and then try using them to log into the workspace, which works a lot of time because people tend to use the same password or similar passwords for their personal and work accounts.”
While Magika could offer a solid rebuttal to the likes of phishing attacks, which have surged in recent years, there are myriad other entry points that cyber criminals and threat actors can leverage to gain unauthorized access.
Magika shows Google is being proactive in AI-powered cyber tools
Though its threat protection is far from comprehensive, Magika is a sign that AI-driven cyber security is increasingly becoming a focus for big players like Google.
By open sourcing the model and making it freely available on GitHub, Google is offering something to the cyber security community as a whole, allowing developers to use and modify Magika with other software.
Google is also looking to integrate Magika with VirusTotal so as to complement its existing code insight function by acting as a pre-filter for file identification.
As security threat mitigation processes go, file identification is a difficult one, with variation in file structures often demanding tailor made systems.
RELATED WHITEPAPER

This can make the construction and implementation of file identification software time-consuming and error prone.
Though cyber security professionals will have to bear in mind the areas which Magika leaves vulnerable, it's still a useful tool in streamlining the file identification process as part of broader cyber security procedures, according to Ruzzi.
“The cyber security domain is very complex and unique, so specific AI needs to be developed for this field,” Ruzzi said.
The more companies use AI for cyber security, Ruzzi said, the better it can get, as companies will benefit from access to a more holistic, more specialized set of tools.

George Fitzmaurice is a former Staff Writer at ITPro and ChannelPro, with a particular interest in AI regulation, data legislation, and market development. After graduating from the University of Oxford with a degree in English Language and Literature, he undertook an internship at the New Statesman before starting at ITPro. Outside of the office, George is both an aspiring musician and an avid reader.
-
 Stop treating agentic AI projects like traditional software
Stop treating agentic AI projects like traditional softwareAnalysis Designing and building agents is one thing, but testing and governance is crucial to success
-
 PayPal appoints HP’s Enrique Lores in surprise CEO shake-up
PayPal appoints HP’s Enrique Lores in surprise CEO shake-upNews The veteran tech executive will lead the payments giant into its next growth phase amid mounting industry challenges
-
 Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documents
Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documentsNews Linwei Ding told Chinese investors he could build a world-class supercomputer
-
 Everything you need to know about Google and Apple’s emergency zero-day patches
Everything you need to know about Google and Apple’s emergency zero-day patchesNews A serious zero-day bug was spotted in Chrome systems that impacts Apple users too, forcing both companies to issue emergency patches
-
 Google wants to take hackers to court
Google wants to take hackers to courtNews You don't have a package waiting for you, it's a scam – and Google is fighting back
-
 Google says reports of a 'huge' Gmail breach affecting millions of users are false, again
Google says reports of a 'huge' Gmail breach affecting millions of users are false, againNews Reports of a major Gmail affecting millions of users have been flooding the web this week – Google says they're "false" and you've nothing to worry about.
-
 This new Android attack could let hackers swipe 2FA codes and snoop on private messages – ‘Pixnapping’ affects Samsung and Google smartphones, but experts warn more could be at risk
This new Android attack could let hackers swipe 2FA codes and snoop on private messages – ‘Pixnapping’ affects Samsung and Google smartphones, but experts warn more could be at riskNews Pixnapping allows attackers to steal two-factor authentication (2FA) codes, private messages, and even financial information.
-
 Google hits back at 'entirely false' reports of major Gmail security breach
Google hits back at 'entirely false' reports of major Gmail security breachNews Reports of a massive Gmail hack affecting billions of users have been denied by Google
-
 Google cyber researchers were tracking the ShinyHunters group’s Salesforce attacks – then realized they’d also fallen victim
Google cyber researchers were tracking the ShinyHunters group’s Salesforce attacks – then realized they’d also fallen victimNews In an update to an investigation on the ShinyHunters group, Google revealed it had also been affected
-
 A flaw in Google’s new Gemini CLI tool could’ve allowed hackers to exfiltrate data
A flaw in Google’s new Gemini CLI tool could’ve allowed hackers to exfiltrate dataNews The company has moved to fix a vulnerability that allowed the execution of malicious code