Microsoft disables VBA macros in Office by default following years of complaints
The move has been widely welcomed by the security industry, though concerns remain over the ease of implementation


Microsoft has announced it will disable all Visual Basic Application (VBA) macros obtained from the internet in Office documents by default in a bid to tackle widespread exploitation of the method used for malware and ransomware delivery.
Cyber security experts have long called on Microsoft to change its approach to VBA macros and the move has been greeted positively by nearly all corners of the industry. The default setting will be applied to five Microsoft Office products - Word, Excel, Powerpoint, Visio, and Access - and will start rolling out to Windows users in April 2022 with the Version 2203 update via the Current Channel (preview).
The change will be available in other update channels at an unspecified later date, including in Current Channel, Monthly Enterprise Channel, and Semi-Annual Enterprise Channel. Office LTSC, Office 2021, Office 2019, Office 2016, and Office 2013 will also eventually all receive the update.
VBA macros are commonly used in Microsoft office products to automate repeat manual functions and are especially commonplace in industries like accounting and finance to expedite tasks in spreadsheets, for example.
Cyber attackers are also commonly drawn to the feature to facilitate the launch of cyber attacks or distribute malware, a technique most commonly used in phishing attacks. A common scenario would see an attacker send a phishing email to an individual's work account containing a seemingly innocuous Office document attached.

Once the document is downloaded and opened, the user would be presented with a document with a notification in the toolbar providing the user to 'enable content' which would see the macro run and whatever malicious payload associated with it downloaded and installed.
Figures from Netskope's January Cloud Threat Report revealed that the use of Microsoft Office documents related to malware downloads increased to 37% by the end of 2021, compared to 19% at the start of 2020.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
"A wide range of threat actors continue to target our customers by sending documents and luring them into enabling malicious macro code," said Tom Gallagher, partner group engineering manager at Office Security. "Usually, the malicious code is part of a document that originates from the internet (email attachment, link, internet download, etc.). Once enabled, the malicious code gains access to the identity, documents, and network of the person who enabled it."
Microsoft is changing the default behaviour of macros in five Office applications so that users will no longer be able to enable them with one click of a mouse. Instead, users will now be presented with a button encouraging them to click and learn more about the potential impacts of enabling macros, and what malicious ones can achieve on a corporate network.
"The default is more secure and is expected to keep more users safe including home users and information workers in managed organisations," Microsoft said.
Community reaction
The cyber security community has come out in droves to support the move from Microsoft, a move that some corners of the industry have requested for some time. As recently as the weekend, the topic resurfaced on social media with experts calling for a change in approach to macros.
Malware campaigns launched through phishing attacks are typically the chief exploiters of VBA macros, such as the newly resurfaced Emotet campaign which relies on the method as a key entry point. Experts believe the move is expected to reduce the number of cyber attacks in businesses significantly.
"The implications of turning Macros off by default is a huge win for security as it significantly reduces the potential victim scope of macro-based attacks for cybercriminals," said Joseph Carson, chief security scientist at Delinea to IT Pro.
"In the past, we relied heavily on users to make security decisions on macros with a warning - this can potentially reduce the risks from curious employees who may just accept the warning and run the macro that could result in stolen credentials or a fully compromised machine. The issue lies in how quickly organisations can upgrade to this version as office upgrades can typically take a long time, though at least those who have moved to cloud solutions should benefit sooner."
Other experts have said malicious macros account for "about 25% of all ransomware entry" - a figure they describe as "conservative" mostly related to larger ransomware organisations like the ones most recently targeted by international law enforcement.
Real-world applicability
Some corners of the industry have raised concerns about how easily it will be for businesses to enforce the new default rules for Office documents given the entrenched culture of macros use in certain industries.
Security experts have said certain users who rely on macros for significant areas of their job, such as accountants, will likely complain to IT departments asking for the default to be reverted back to the one-click functionality of before, despite the risks.
RELATED RESOURCE

The best defence against ransomware
How ransomware is evolving and how to defend against it
Others disagree, saying the difference will only add a small layer of friction to normal processes. Magni Reynir Sigurðsson, senior manager of detection technologies at Cyren said: "this will not affect industries that rely on documents using macros, they will just have to take the extra step of enabling them file by file for specific files they do trust".
"For those industries that heavily rely on macros such as financial or accounting industries, the hope is that Microsoft will, at last, make it simple enough for individuals to turn it on for on-demand purposes on approved documents and scanned documents," added Carson.
Administrator options
There are a number of policies available to system administrators who wish to enable the new macro settings in a custom way, one that's suitable for their business. Such policies include:
- Blocking macros from running in Office files from the Internet - Microsoft recommends enabling this policy and the organisation will not be affected by the default change
- Opening files from a Trusted Location
- Opening files with digitally signed macros and providing the certificate to the user, who then installs it as a Trusted Publisher on their local machine
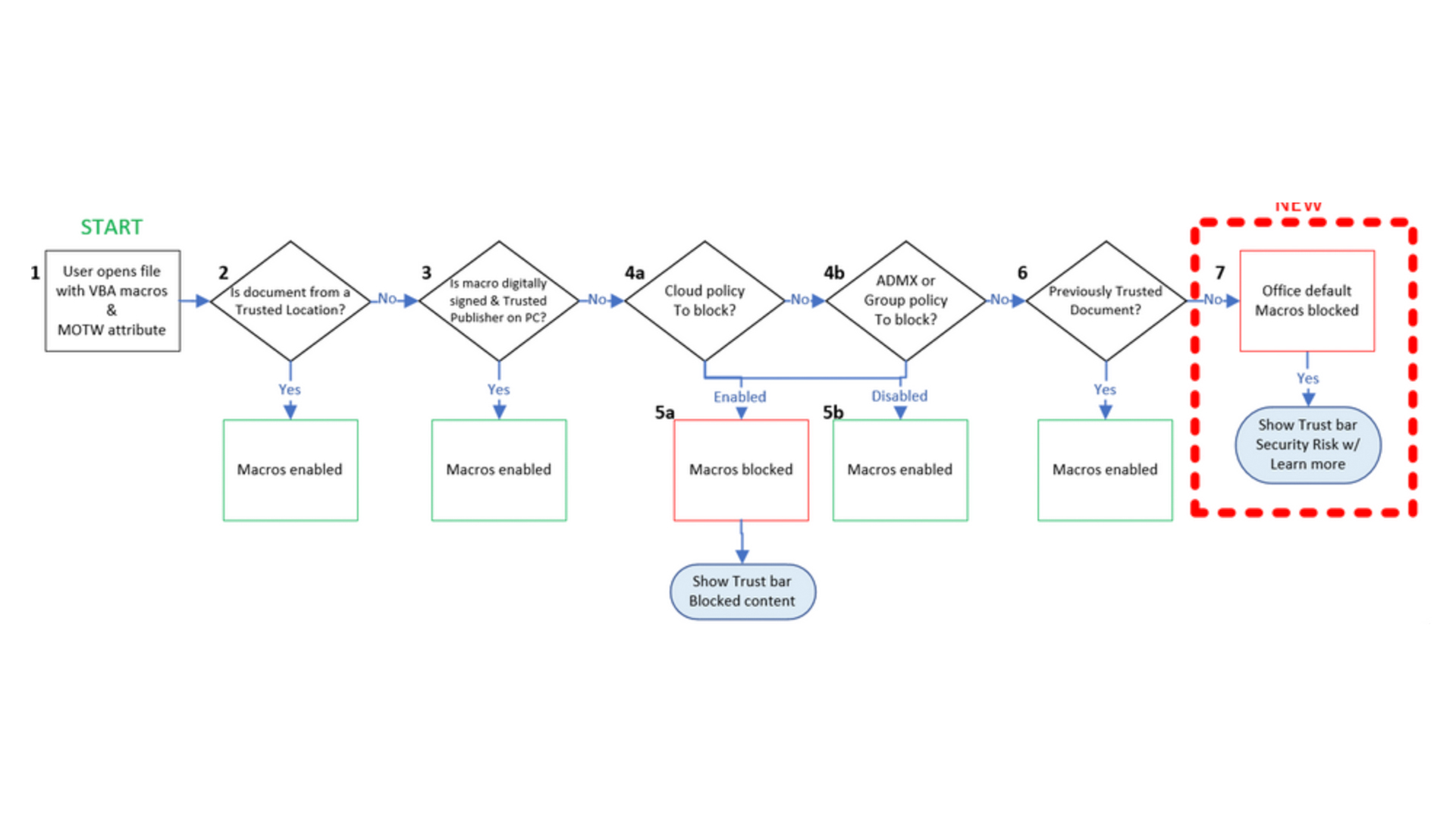
The image above outlines the evaluation flow for Office files with VBA macros and Mark of the Web (MOTW) - an attribute added to files by Windows when it is sourced from an untrusted location.
Administrators can read more about how the change impacts the environments in Microsoft's dedicated article for Office admins.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses