Tailscale review: A perfect mesh VPN for small businesses
Tailscale gives you fast, easy remote access to peer devices
-
+
Provides easy WireGuard implementation
-
+
Supports passkeys
-
+
Free for many use cases
-
+
Support for mobile device users
-
-
Tailscale maximizes security and minimizes the trust you need to give it, but could still be a point of attack/failure

The benefits of the Tailscale VPN are numerous. Imagine you're a remote worker using a self-hosted document management system that you want to interact with while away from home. Or, you're running a self-hosted server that you want colleagues to access, but you don't want them to see anything else on your network. Or you want to make encrypted backups on hard drives at the office of a partner company.
READ MORE

There are point-to-point VPN options to manage this kind of thing. WireGuard is an open-source VPN that runs on your personal devices (including your phone) and a computer at home that acts as a VPN server. It takes a little setting up, and that node on your home network has to stay active to use it effectively or you'll have to set up separate WireGuard VPNs on all your devices. You'll also have to use dynamic DNS for any destination WireGuard servers to ensure that your nodes can find each other when your ISP changes your static home address.
Supporting a handful of remote users can be troublesome enough, but it gets exponentially more complex as you add users. Multiple people would connect to a VPN in a hub and spoke configuration. You can add more WireGuard hubs to manage different physical offices around the country, but this still doesn't allow machines to talk directly with each other; they can only connect with a hub and access centralized resources from there.
Tailscale review: How it works
This is where Tailscale comes in. It's a service to manage WireGuard VPNs in a mesh configuration, enabling them to find each other. Admins set up their Tailscale network (called a tailnet) using Tailscale's centralized service. They register devices to the tailnet by installing Tailscale's client, which contains Wireguard. The client sets up a private/public key pair and gives the public one to Tailscale.
Private keys never leave a device, but Tailscale manages those devices' public keys. It acts only as a control plane, enabling machines to find each other, no matter what their real IP address is. After they connect and authenticate each other using their private keys, their data session takes place outside the Tailscale network, meaning that it doesn't see the data (which is end-to-end encrypted, thanks to Wireguard).
Because Tailscale is just handling the control plane, its network and compute load is far lighter than it would be if it was having to transport the content of an entire data session between clients. That enables it to offer an impressive free service tier supporting up to 100 devices and three users. After that, pricing scales reasonably, placing it within reach of even small businesses that need more scale.
The site manages NAT traversal, and if it does run into problems, it falls back to a network of Tailscale-operated relays using its Designated Encryption for Packets (DERP) software. Like Tailscale's client, this software is open source.
Tailscale review: Setup
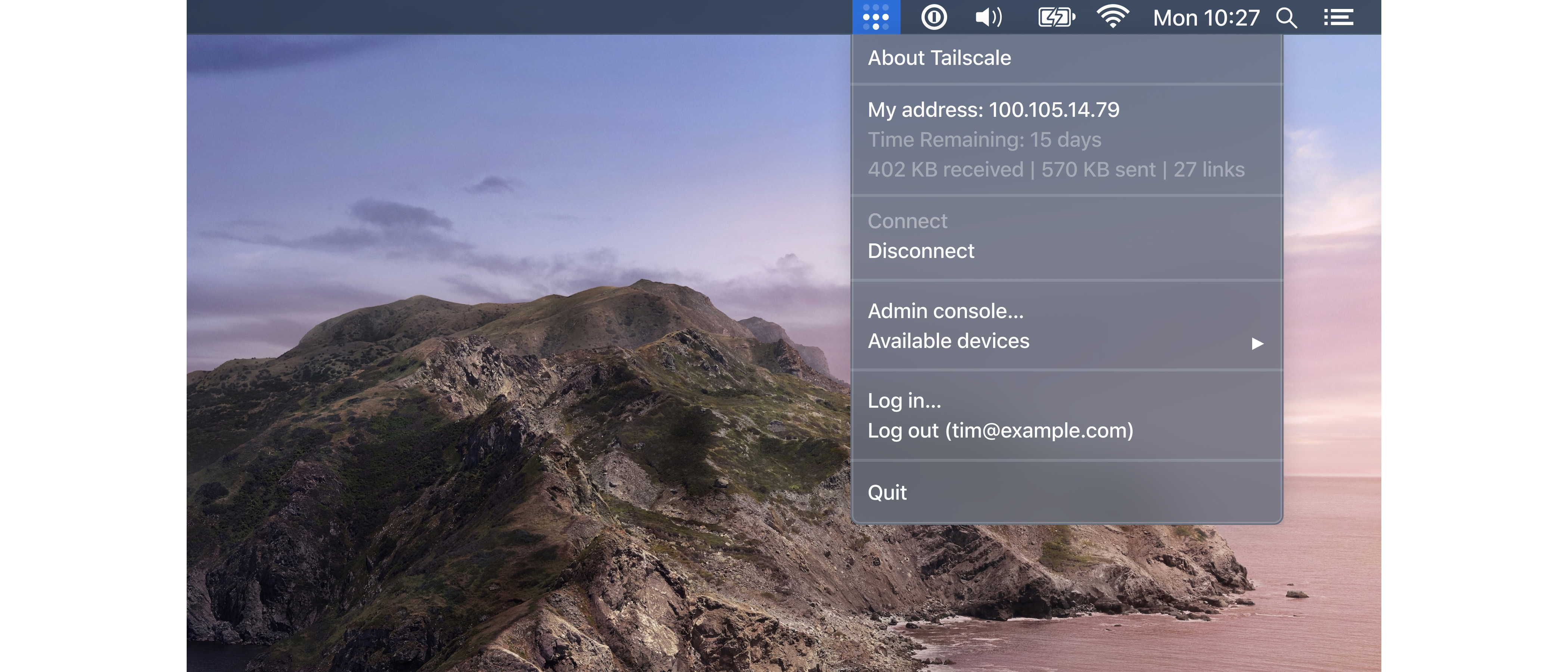
To set up a tailnet, you register with Tailscale using an identity provider like Apple or Google rather than email, and it then asks you to install its client on your device (it supports Android, iOS, Windows, macOS, and Linux). The client will make you log in again, which registers the device. You can see it immediately pop up on the Machines tab on your tailnet's page on the service's web page.
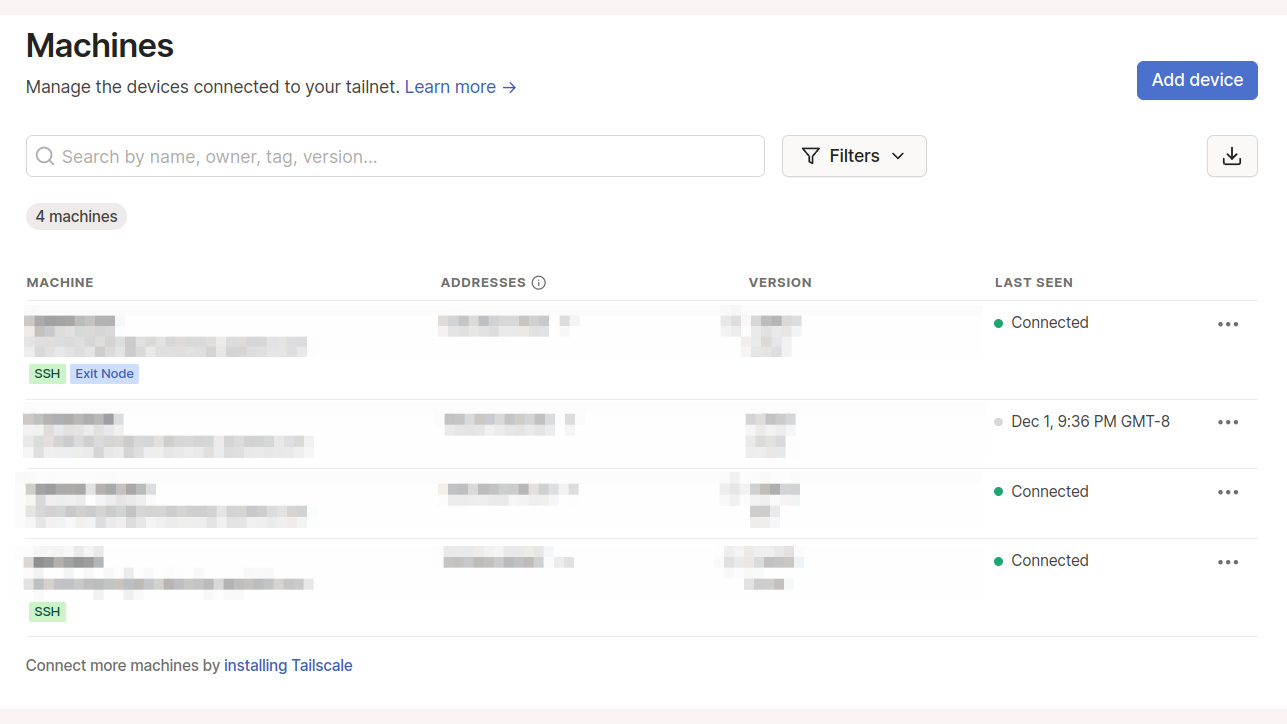
Installing on Linux takes a few terminal commands. Start the service and it displays a URL, which takes you to the registration page.
Once running, it works seamlessly. On an iPhone, bringing up the Tailscale app triggers the phone's VPN icon to show you're using Wireguard, and shows you a list of each device's address on the Tailscale network, which you can copy and paste. So, you can access your document management system, home assistant, NAS box, or other resources easily.
Tailscale review: Services
You can also switch on a feature that collects information on all the services running on your Tailscale devices. This is not only a handy way of monitoring what the machine is exposing and checking whether that service is up, but also provides you with a handy way to copy the service address for easy access. Tailscale doesn't store service information but just passes it to your tailnet dashboard.
One advantage of accessing services directly via the tailnet is that you can close down all the internet-facing ports on your firewall and just access everything via the tailnet, reducing your external attack surface.
The services that Tailscale collects include SSH, and while you can happily use the SSH service address on the tailnet to log in using your regular SSH keys, you can also use the tailnet's own authentication to log in more quickly. To do this, you use a command line option when starting the service on the SSH host, which allows access using the Tailscale private keys that power the Wireguard connection.
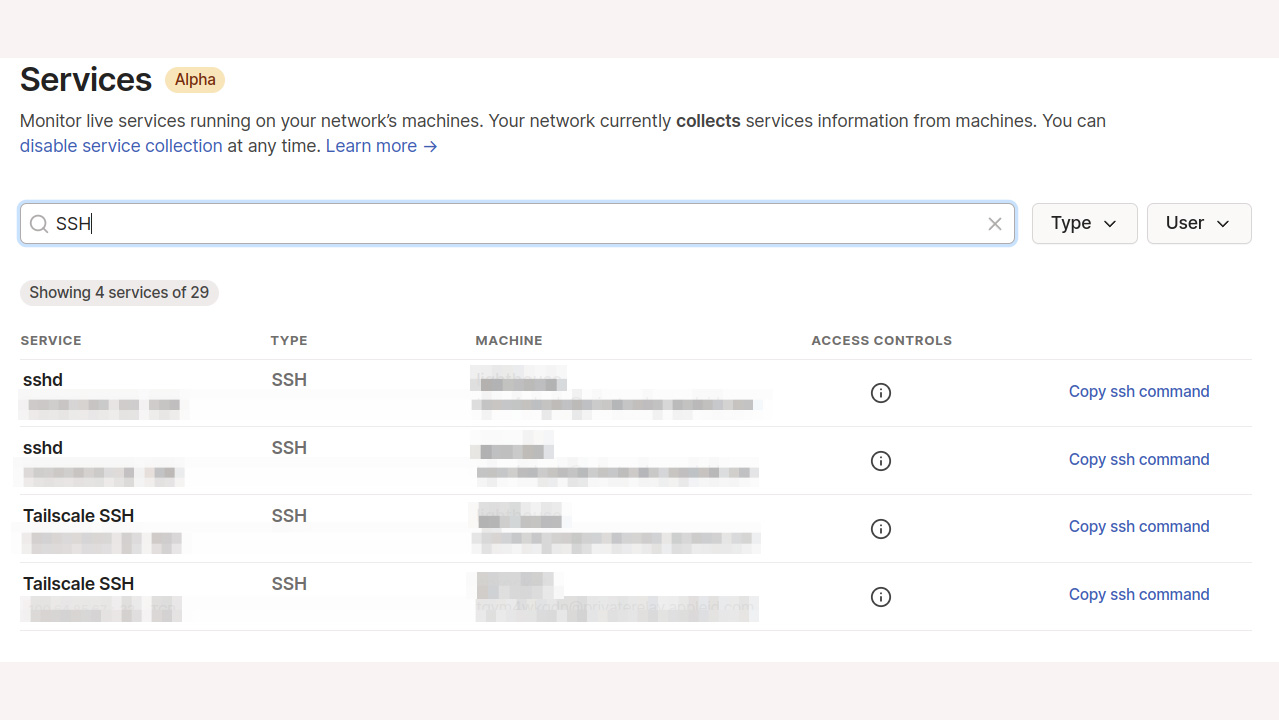
Your tailnet also offers MagicDNS, a service that lets you just use a device's name instead of its IP address on the tailnet, making access more intuitive. That, along with the native tailnet authorization, enables you to simply ssh /mymachine/, and you're in. It's a handy little feature if you're constantly launching shells on remote computer.
Tailscale review: Other functions
Once you've registered all your devices, there are plenty of things you can do with this service. You can turn one of the machines in your network into an exit node for internet access. This enables any machine with access to that device to specify it as such when starting Tailscale. It will then direct all traffic not intended for its Tailscale peers to the exit node.
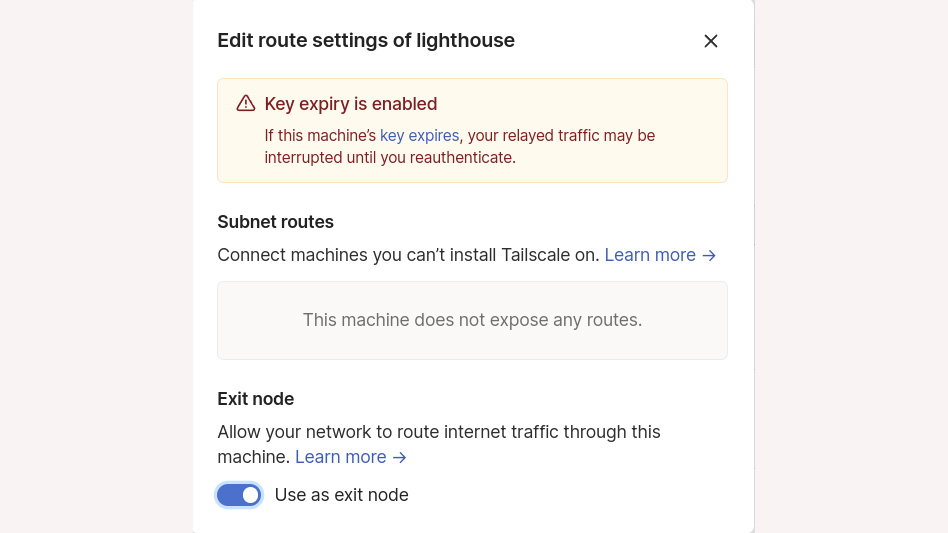
The exit node feature creates a VPN for mobile users, so when you're in an airport or hotel with dodgy open Wi-Fi, you needn't cross your fingers and hope that you're connecting to a legitimate access point or that someone is sniffing your traffic. It also gives you all the protections of your home network, which is handy if you run an ad blocker or traffic scanning service on your LAN.
If you're interested in appearing to be in another country, Tailscale has also partnered with VPN provider Mullvad so that you can use any of its servers as an exit node.
You can also temporarily share nodes privately with a Tailscale user who isn't part of your network. This could be useful for providing ad hoc access to specific files. Tailscale has a walk-through on its website.
Tailscale review: Securing your tailnet
When you add more devices and users to your network, you'll quickly want to restrict access to certain things. None one should be able to look at files on your NAS, for example. Tailscale offers access control lists (ACLs) that enable you to control which users and devices can access, down to an IP address and port level. The ACL starts wide open by default, but once you've edited it (it's written in a human-friendly variant of JSON), it switches to denying access by default, so you have to explicitly open things up.
Tailscale is a useful service for everyone from families with a pet self-hosting geek through to larger businesses, and it already has some impressive corporate customers under its belt. There's really not much to dislike here. The main concern people might have is trusting a single third-party with their infrastructure. However, the company has done its best to require minimal user trust.
For example, one scenario could see an attacker co-opt Tailscale's coordination server and add malicious nodes to the control plane. To protect against that, Tailscale added a facility called tailnet lock, which stops nodes on your tailnet from automatically trusting a new node's public keys.
RELATED RESOURCE

Discover how you can reduce complexity and fill modern data protection gaps
DOWNLOAD NOW
It's still possible that an attacker – perhaps an intelligence agency – could compromise Tailscale's internal systems and push compromised code to production, compromising the client enough to issue compromised keys.
Also possible are legitimate software bugs that could lead to remote code execution, given the level of privilege that the client can be given on machines. Indeed, security researcher Emily Trau expertly highlighted just such a bug a year ago.
The thing is, such things are true of any service (someone might try to compromise Wireguard's own development pipeline, for example). And like Wireguard, Tailscale's client software is open source, enabling the community to scrutinize it.
Tailscale review: Is it worth it?
Security boils down to two things; the company's approach to it, and the user's. On the first point, Trau's blog post is a glowing testimony. She said that people should keep using Tailscale, given that the company fixed the flaw she identified in hours. She added: "The speed and quality of Tailscale's response to our report is unlike any vendor interaction I have experienced, and suggests a deep commitment to keeping their customers safe."
Tailscale works with third parties for security audits, and also seems to have a friendly, non-evil-corporate ethos. Its own code is open source, and it enthusiastically supports open-source versions of itself such as the Headscale project, which develops an independent self-hosted server for people to run their own tailnets. The Tailscale team also makes the service free to open-source projects.
There's a caveat though. Tailscale is funded by venture capital, and VCs can exert influence over company strategy in ways that may cause value creep. Companies that start out with a "don't be evil" ethos often find market requirements changing their culture. Google, where Tailscale's founders previously worked, has been a case in point. So this is worth watching over time.
On the second point - user risk management - any admin should harden their infrastructure as much as possible. If you're nervous about using someone else's software to connect your infrastructure, you can avoid turning on some of the funkier stuff like Tailscale-authenticated SSH. You can set up ACLs and follow basic cybersecurity hygiene principles like keeping your software patched. Tailscale has a tailnet hardening guide here.
For now, we're going to keep using Tailscale. It solves some pressing problems, and the company has been impressively conscientious so far. If you're a small business interested in easy VPN mesh setup, this is definitely worth a look.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Danny Bradbury has been a print journalist specialising in technology since 1989 and a freelance writer since 1994. He has written for national publications on both sides of the Atlantic and has won awards for his investigative cybersecurity journalism work and his arts and culture writing.
Danny writes about many different technology issues for audiences ranging from consumers through to software developers and CIOs. He also ghostwrites articles for many C-suite business executives in the technology sector and has worked as a presenter for multiple webinars and podcasts.
-
 AWS and NTT Data team up to drive legacy IT modernization in Europe
AWS and NTT Data team up to drive legacy IT modernization in EuropeNews Partnership between AWS and NTT DATA aims to boost AWS European Sovereign Cloud capabilities
By Nicole Kobie Published
-
 What the UK's new Centre for AI Measurement means for the future of the industry
What the UK's new Centre for AI Measurement means for the future of the industryNews The project, led by the National Physical Laboratory, aims to accelerate the development of secure, transparent, and trustworthy AI technologies
By Emma Woollacott Published
-
 ‘In the model race, it still trails’: Meta’s huge AI spending plans show it’s struggling to keep pace with OpenAI and Google – Mark Zuckerberg thinks the launch of agents that ‘really work’ will be the key
‘In the model race, it still trails’: Meta’s huge AI spending plans show it’s struggling to keep pace with OpenAI and Google – Mark Zuckerberg thinks the launch of agents that ‘really work’ will be the keyNews Meta CEO Mark Zuckerberg promises new models this year "will be good" as the tech giant looks to catch up in the AI race
By Nicole Kobie Published
