Zero Day Initiative disclosed unpatched Microsoft Jet database flaw
All supported versions of Windows affected by remote code execution bug

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Security researchers have disclosed a remote code execution vulnerability that affects the Microsoft Jet Database Engine.
According to a blog post by the Zero Day Initiative (ZDI), an out-of-bounds (OOB) write in the Microsoft JET Database Engine that could allow remote code execution was initially reported to Microsoft back in May. Microsoft managed to reproduce the bug shortly afterwards.
While Microsoft has patched two other buffer overflow bugs in Jet in its latest Patch Tuesday update, this bug has been left out and will be fully patched in the October update.
"An attacker could leverage this vulnerability to execute code under the context of the current process, however it does require user interaction since the target would need to open a malicious file. As of today, this bug remains unpatched," said Simon Zuckerbraun, a security researcher at ZDI.
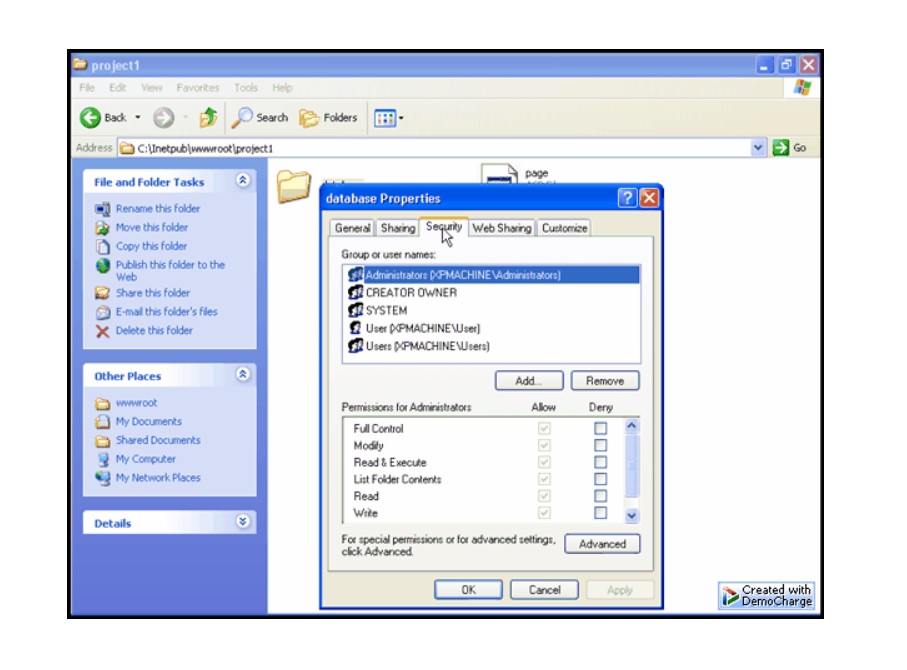
The bug affects all supported Windows versions including server editions. The flaw itself can be triggered by opening a Jet source via a Microsoft component known as Object Linking and Embedding Database (OLEDB).
"To trigger this vulnerability, a user would need to open a specially crafted file containing data stored in the JET database format. Various applications use this database format. An attacker using this would be able to execute code at the level of the current process," said Zuckerbraun.
In a security advisory, ZDI said the issue is in Microsoft Jet's index manager. "Crafted data in a database file can trigger a write past the end of an allocated buffer," stated the advisory.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The advisory said that given the nature of the vulnerability "the only salient mitigation strategy is to restrict interaction with the application to trusted files".
A proof-of-concept exploit code has been posted on GitHub.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 The threat prevention buyer's guide
The threat prevention buyer's guideWhitepaper Find the best advanced and file-based threat protection solution for you
-
 Supply chain as kill chain
Supply chain as kill chainWhitepaper Security in the era Zero Trust
-
 Microsoft under fire for “negligent” security practices in scathing critique by industry exec
Microsoft under fire for “negligent” security practices in scathing critique by industry execNews Microsoft took more than 90 days to issue a partial fix for a critical Azure vulnerability, researchers found
-
 Apple patches zero day linked to spyware campaign
Apple patches zero day linked to spyware campaignNews Kaspersky researchers were the first to report a zero day used in a sophisticated attack chain
-
 MOVEit cyber attack: Cl0p sparks speculation that it’s lost control of hack
MOVEit cyber attack: Cl0p sparks speculation that it’s lost control of hackNews The hackers return with their second major data-extortion attack of 2023, but may have bitten off more than they can chew
-
 Microsoft says it knows who was behind cyber attacks on MOVEit Transfer
Microsoft says it knows who was behind cyber attacks on MOVEit TransferDozens of organizations may have already lost data to hackers exploiting the critical flaw
-
 Trend Micro security predictions for 2023
Trend Micro security predictions for 2023Whitepaper Prioritise cyber security strategies on capabilities rather than costs
-
 Windows, macOS, and Tesla exploits debuted at Pwn2Own hacking contest
Windows, macOS, and Tesla exploits debuted at Pwn2Own hacking contestNews Researchers took home more than $375,000 in winnings on the first day of the competition


