WatchGuard XCS-770 review
WatchGuard makes a big play for the web and message content security market with its new XCS appliance family. In this review we see how the mid-range XCS-770 stands up.
WatchGuard’s new XCS appliances deliver an impressive range of data protection and content security features. Its anti-spam and web filtering capabilities are extremely good and the deep scanning technologies allow email usage to be closely controlled. Our only issues are that the web interface could be more intuitive and we can’t quite see the point of the transparent mode.

WatchGuard XCS-770
WatchGuard XCS-770
WatchGuard XCS-770
WatchGuard XCS-770
WatchGuard XCS-770

WatchGuard XCS-770
WatchGuard has traditionally focused on the firewall, UTM and SSL-VPN markets but its latest XCS (extensible content security) appliances signal a move into web and email content security territory. This comes about as a direct result of its acquisition of Borderware Technologies last year and the end result is a family of six new appliances.
The XCS-770 on review targets mid-sized business and this 1U low-profile rack server has enough grunt to handle up to 4,000 users. It offers three Gigabit interfaces and can be deployed behind an existing firewall, in parallel with it or in a DMZ.
The appliance also supports a transparent mode but we found this is largely redundant. Choosing this mode requires two of the ports to be designated as inbound and outbound but in this mode it can't filter email traffic making it rather pointless.
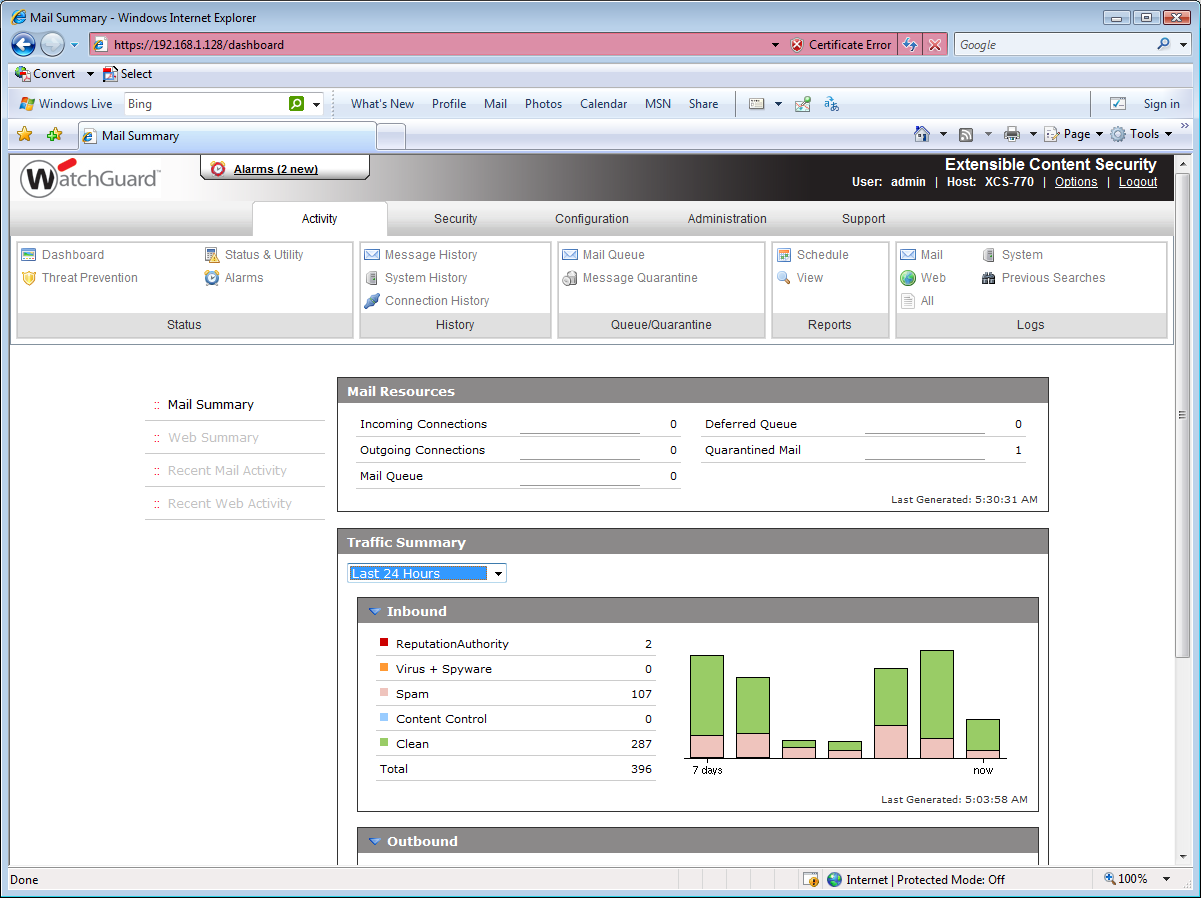
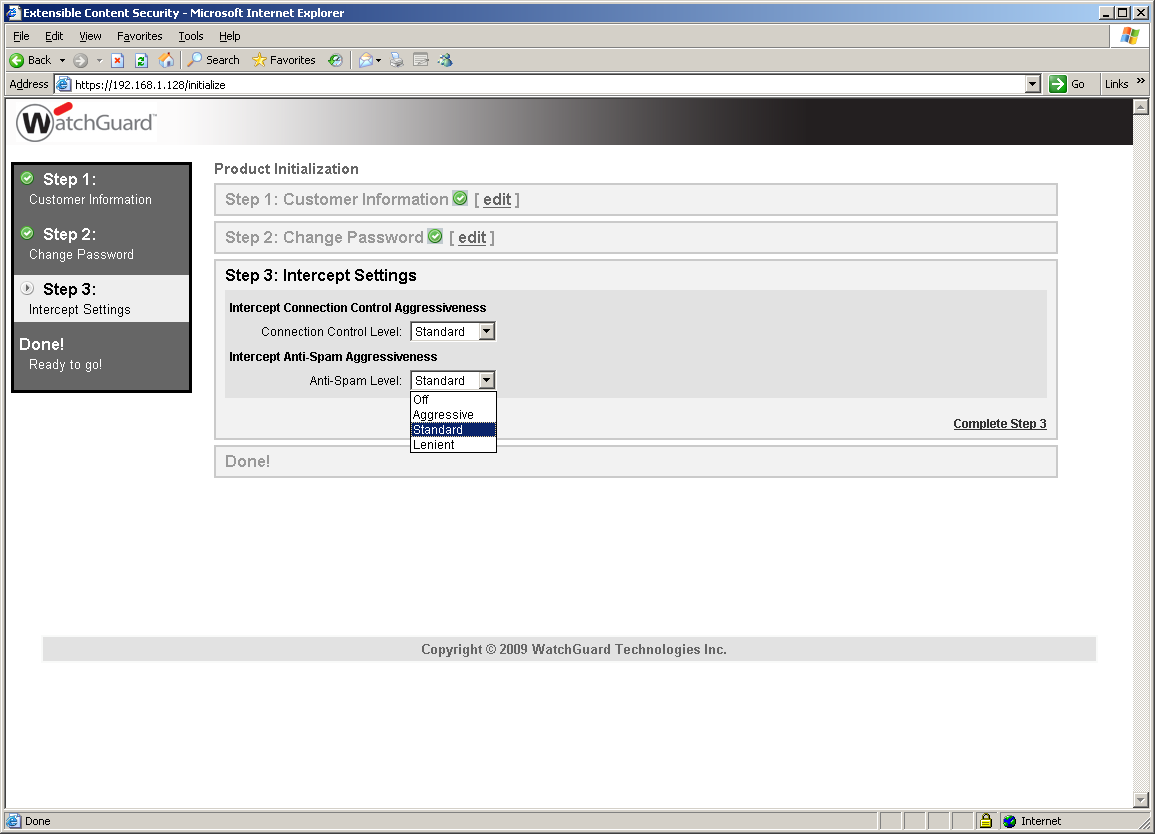
We opted to deploy the XCS-770 behind the lab's firewall and configured our test clients to use it as their proxy. On first contact with its web interface you run a quick start wizard which asks how aggressive you want the Intercept scanning services to be. Intercept gathers all the anti-spam technologies under one roof and offers three settings of aggressive, standard and lenient.
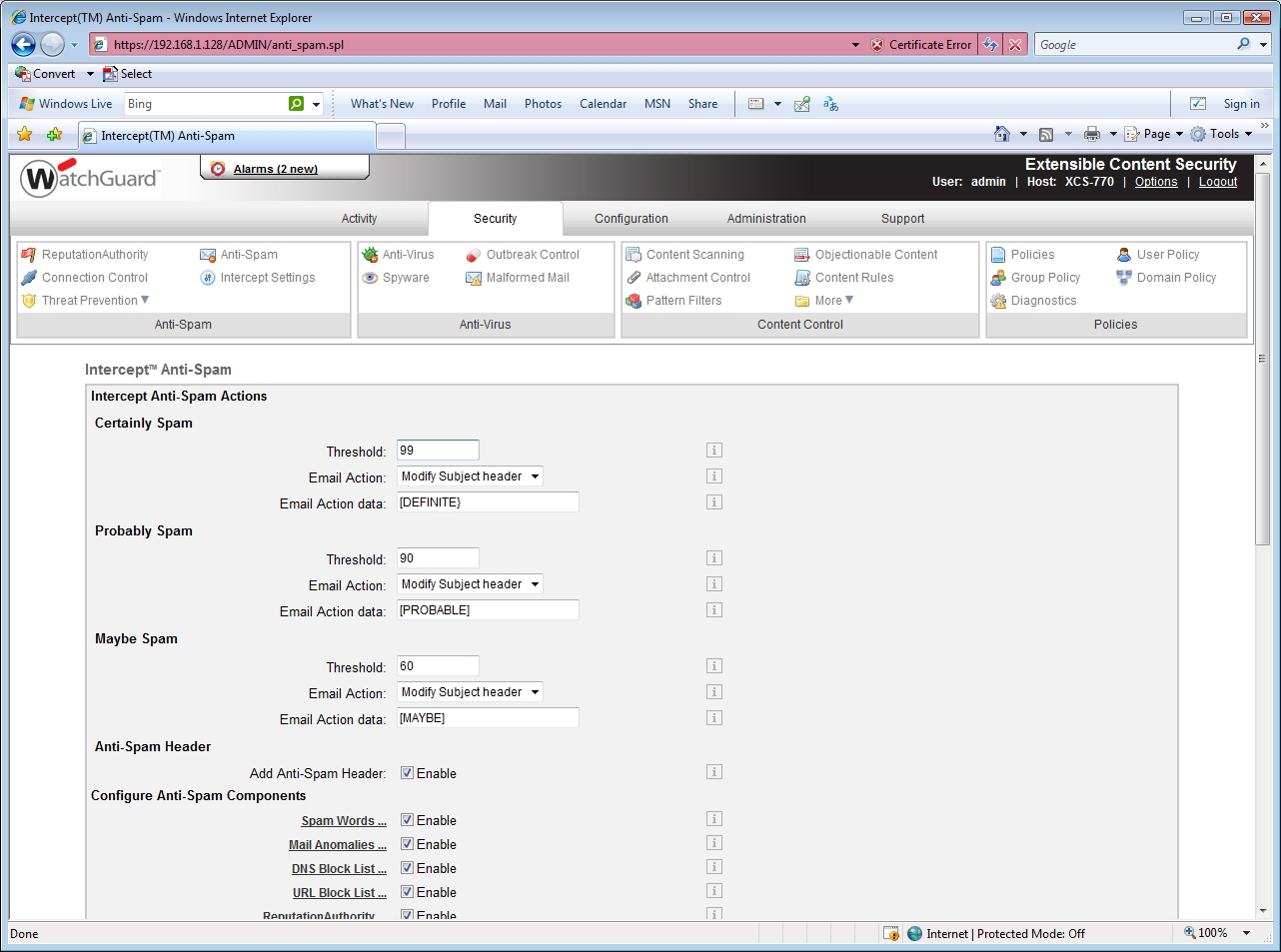
For anti-spam you have a range of features including spam word dictionaries, DNS RBLs, message content analysis, block lists and WatchGuard's ReputationAuthority component. The latter uses behavioural analysis to determine whether inbound web and mail traffic can be trusted. It checks on the reliability of mail senders and uses information from WatchGuard's installed base of XCS appliances to check their reputation.
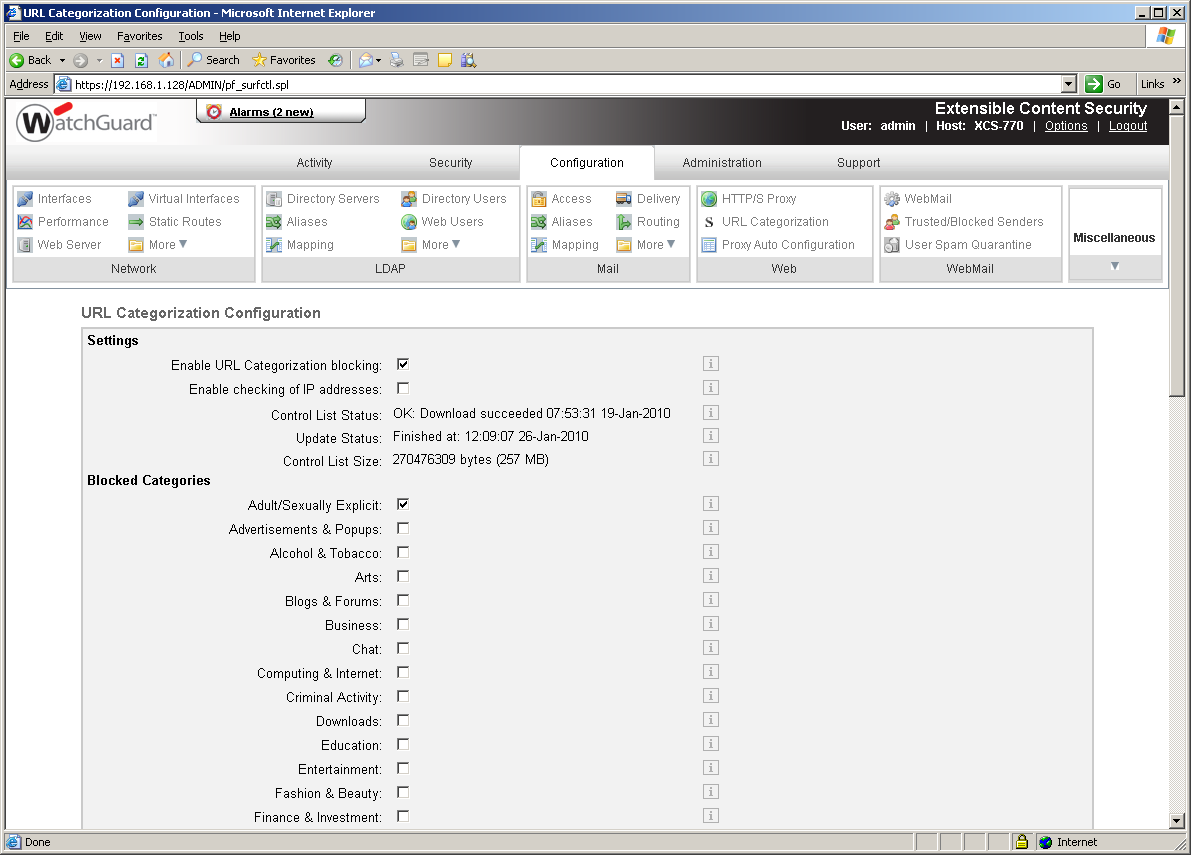
WatchGuard's policies allow strict security measures to be applied as along with global settings and the default policy, you can apply custom policies to domains, groups and users. These are applied in strict order of priority so a user policy would take precedence over a domain policy.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 ‘Not a shortcut to competence’: Anthropic researchers say AI tools are improving developer productivity – but the technology could ‘inhibit skills formation’
‘Not a shortcut to competence’: Anthropic researchers say AI tools are improving developer productivity – but the technology could ‘inhibit skills formation’News A research paper from Anthropic suggests we need to be careful deploying AI to avoid losing critical skills
By Nicole Kobie Published
-
 CultureAI’s new partner program targets AI governance gains for resellers
CultureAI’s new partner program targets AI governance gains for resellersNews The new partner framework aims to help resellers turn AI governance gaps into scalable services revenue
By Daniel Todd Published
-
 Imperial College wants to train larger, more complex AI models – so it's teaming up with Digital Realty on a UK-first project
Imperial College wants to train larger, more complex AI models – so it's teaming up with Digital Realty on a UK-first projectNews Digital Realty’s Woking data center has been selected to run the project
By Emma Woollacott Published
