Fujitsu and Keio University partner on automated internet 'trust layer'
The pair want to create an interface that draws information from different sources, like experts or physical tools like sensors, to verify the authenticity of data posted on the internet


Fujitsu and a Japanese university research institute have published research on the concept of a 'Trustable Internet', which aims to make it easier to verify the authenticity of data on the internet.
RELATED RESOURCE

CIO Priorities: 2020 vs 2023
Zero Trust, SaaS Security, and its impact on SD-WAN being a priority
The Japan-based tech company teamed up with the Keio Research Institute at Keio University to publish a whitepaper on the Trustable Internet concept. The companies said that the verification of large amounts of information on the Internet remains a difficult task, highlighting the need for a more general-purpose method to prove the authenticity of data.
The pair's proposal would aim to help verify the authenticity of data by adding an interface, which they have dubbed the 'Endorsement Layer', which would theoretically help users confirm the credibility of various data based on additional information related to the generation and processing of data.
This includes information on confirmation and evaluation by third parties that have viewed the data, and information on physical spaces related to the data including from sensors, for example.
“This enables users to judge the credibility of data from a variety of perspectives to ultimately prevent the use of unverified data and the spread, unintentional or otherwise, of false and unverified information ('fake news'),” said the companies in the research.
An example that the companies gave in a video was a person seeing a river swollen by heavy rain and consequently posting on social media that a flood is about to occur.
The companies said the message could be misinterpreted that a flood is about to occur, or has occurred, generating anxiety among the general public as well as triggering social and economic confusion.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
If the companies’ technology was applied in this case, it could inform the users reading the message about the source of the data and the process by which it was generated, as well as extra information like the actual water level of the river, collected from sensors, or the fact that no evacuation is needed since no message has been issued from the authorities.
“In this way, a chain of verifiable data is established, reinforcing the certainty of the data,” said the narrator in the video. “The confirmed data is then presented to the viewer in a way that is easy to be understood. Viewers can compare the posted message to the confirmed data and act with common confidence without confusion.”
The two companies suggested the proposed Endorsement Layer should sit between the existing 'Internet Layer' and the 'Web/App' layer. This configuration can be implemented without impacting the existing internet, they said, and allows users to use the internet and applications as usual.
If necessary, they could also obtain additional information to verify the authenticity of data and information.
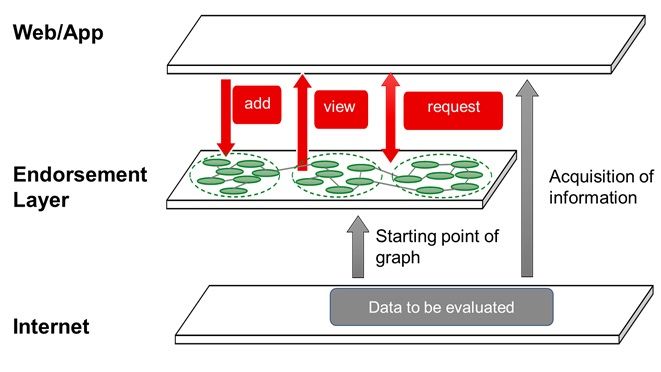
The additional information can be used to verify the authenticity of data and can be provided by people and devices at the time of data generation, including information on the name, affiliation, and qualifications of the creator of the data, such as the person or company, or the device used, place, and date and time.
Extra information also includes verifications and evaluation from third parties such as independent experts and information obtained from physical spaces including sensor measurements that can be added after the data is generated.
Users would be able to search and check additional information necessary to verify the authenticity of data on the internet in the Endorsement Layer, where information would be stored as graph data.
Through this, the companies hope users would be able to evaluate data authenticity from a different perspective, to make data-driven decisions more accurate, and help to prevent the spread of unverified data.
“By providing a mechanism that enables users to verify and judge the reliability of data available on the internet from various perspectives, we contribute to the health of society and economic activities,” the companies stated. “This is what we are aiming for a trustable internet that people can use information securely.”
Zach Marzouk is a former ITPro, CloudPro, and ChannelPro staff writer, covering topics like security, privacy, worker rights, and startups, primarily in the Asia Pacific and the US regions. Zach joined ITPro in 2017 where he was introduced to the world of B2B technology as a junior staff writer, before he returned to Argentina in 2018, working in communications and as a copywriter. In 2021, he made his way back to ITPro as a staff writer during the pandemic, before joining the world of freelance in 2022.
-
 Phantom firms: The rise of fraudulent cybersecurity vendors
Phantom firms: The rise of fraudulent cybersecurity vendorsIndustry Insights Channel partners need systematic vendor vetting to combat rising phantom firm scams
-
 Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"
Snowflake and OpenAI are teaming up to help enterprises capitalize on their "most valuable asset"News OpenAI models and tools will now be embedded within the Snowflake Intelligence and Cortex platforms
-
 AI inferencing with AMD EPYC™ processors
AI inferencing with AMD EPYC™ processorswhitepaper Providing an excellent platform for CPU-based AI inferencing
-
 Green Quadrant: Enterprise carbon management software 2022
Green Quadrant: Enterprise carbon management software 2022Whitepaper Detailing the 15 most prominent carbon management software vendors to see if they fit your requirements
-
 Accenture bolsters industrial AI services with Flutura acquisition
Accenture bolsters industrial AI services with Flutura acquisitionNews Bangalore-based AI specialist will help “power industrial AI-led transformation” for Accenture’s global clients
-
 Baidu unveils 'Ernie' AI, but can it compete with Western AI rivals?
Baidu unveils 'Ernie' AI, but can it compete with Western AI rivals?News Technical shortcomings failed to persuade investors, but the company's local dominance could carry it through the AI race
-
 Robotic process automation
Robotic process automationWhitepaper A no-hype buyer's guide
-
 The increasing need for environmental intelligence solutions
The increasing need for environmental intelligence solutionsWhitepaper How sustainability has become a major business priority and is continuing to grow in importance
-
 Why developers are turning to ultra-powerful workstations for more creative freedom at less cost
Why developers are turning to ultra-powerful workstations for more creative freedom at less costWhitepaper The market for AI applications is immense and their economic value even greater
-
 2022 Magic Quadrant for data integration tools
2022 Magic Quadrant for data integration toolsWhitepaper Using research to evaluate suitable vendors for their existing and upcoming data integration use cases
