Wimbledon to provide personalised mobile experience via IBM
IBM debuts revamped Android & iOS apps and makes Henman Hill the event's social media hub

IBM has refreshed its Android and iOS apps, and will debut a host of enhanced analytics and social media capabilities for the 2014 Wimbledon Championships.
Alexandra Willis, content and communications manager at Wimbledon, explained the All England Lawn Tennis Club (AELTC) wants fans to get an immersive experience regardless of whether they are using the website or mobile applications.
"We wanted to create a clean and beautiful experienceto give our users the ability to say I'm most interested in this today'," Willis said at the launch event.
Mobile users can download the apps across iPads, iPhones or Android devices from today and get a curated feed based on their favourite events (singles/doubles/mens/womens), players or countries when the tournament starts.
You'll receive content in a live, personalised feed.
IBM will also introduce a Social Command Centre this year. Powered by its SoftLayer cloud technology this will allow the AELTC to see which topics and matches are being discussed, allowing it to tailor content for its website.
The opinions of those sitting on the much-loved Henman Hill will now be pulled together via a social media hub. The thoughts of those inside the ground will be compared with the rest of the world via Twitter. Questions will be flashed up on the big screen during games and answers will the shown in the format of #Hill vs #The World.
A myriad of interesting information will also be available to viewers via this hub including heat maps, photos and key player facts.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
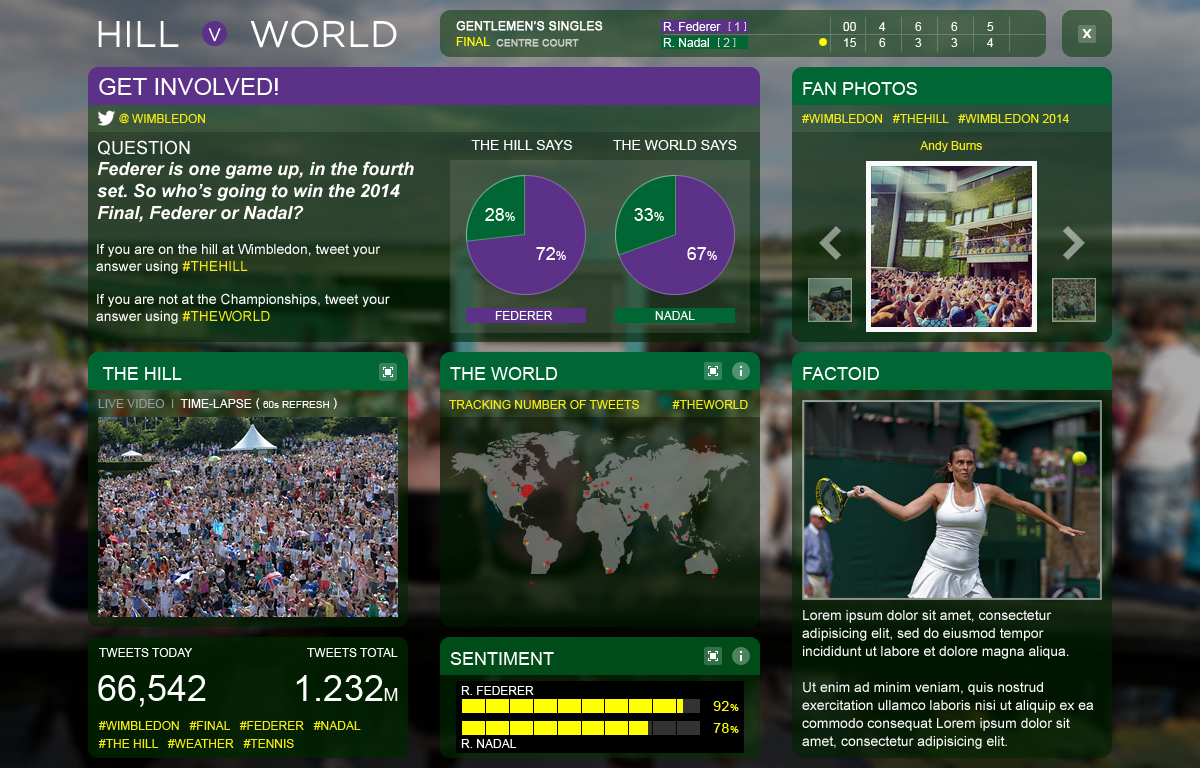
Using the algorithms, the AELTC will also be able to analyse the brand sentiment in real-time, so it can engage with fans.
Meanwhile, IBM's Watson platform will capture relevant data from multiple sources including tablets, smartphones and desktops to predict traffic to Wimbledon.com.
The website typically spikes to 20 million page views during the tournament and every 90 minutes, IBM will monitor usage, explained Sam Seddon, Wimbledon client & program executive for IBM. This will ensure that IBM dedicates an optimal level of resources from its three datacentres in North America to ensure uptime and retain cost efficiency.
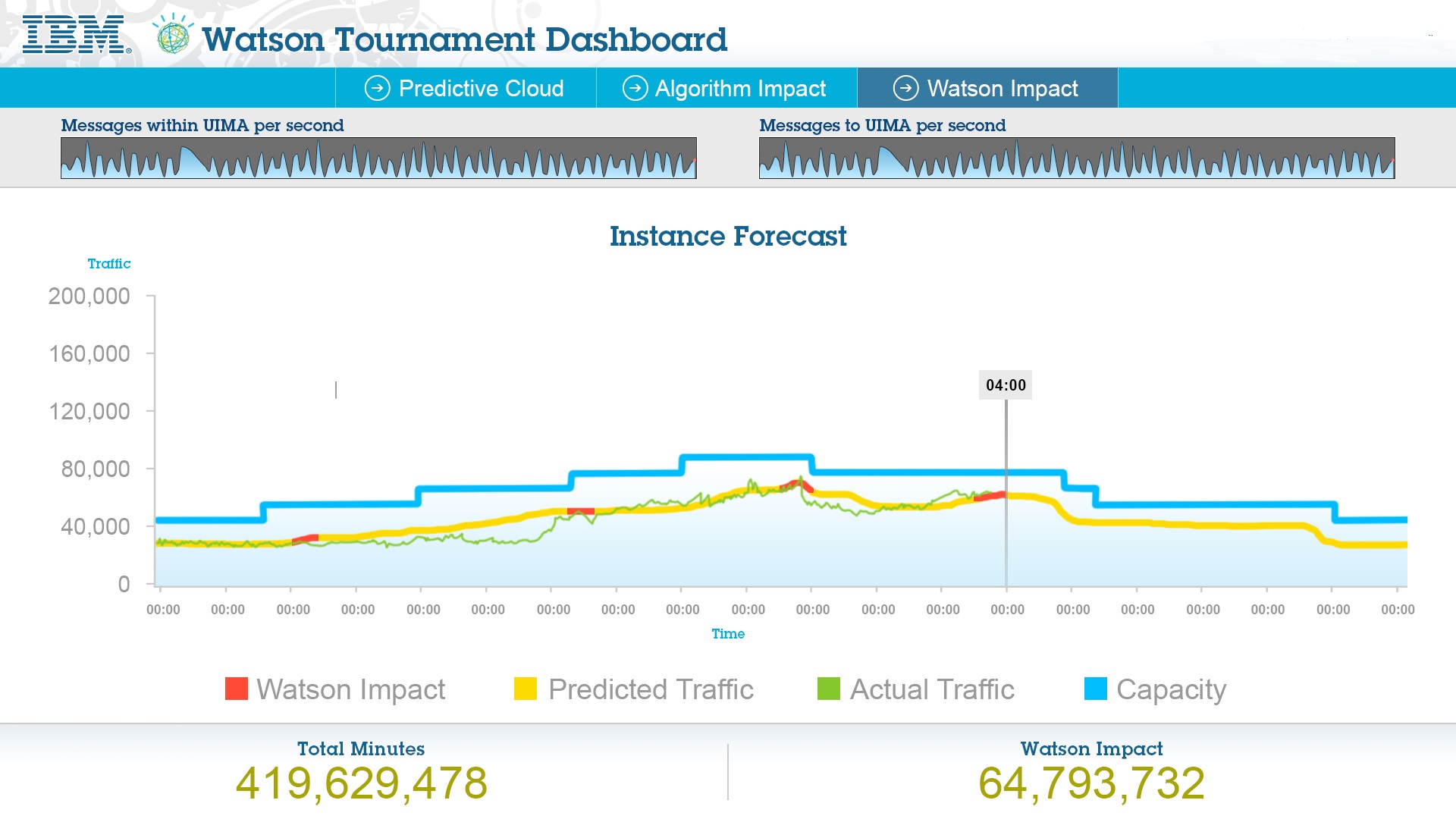
For the first time BBC commentators will also be able to analyse "aggressive play" and viewers will see 3D graphics on Centre Court matches.
-
 IBM Sovereign Core targets AI and cloud data residency gains for European enterprises
IBM Sovereign Core targets AI and cloud data residency gains for European enterprisesNews The new IBM Sovereign Core service allows organizations to build, manage, and deploy their own AI-ready sovereign workloads
-
 IBM and SAP expand partnership to drive generative AI capabilities
IBM and SAP expand partnership to drive generative AI capabilitiesNews The new Value Generation initiative aims to deliver greater client productivity gains through generative AI solutions
-
 Driving business innovation through application modernization and hybrid cloud
Driving business innovation through application modernization and hybrid cloudwebinar Transform with IBM Z
-
 Building an intelligent, modern, sustainable enterprise
Building an intelligent, modern, sustainable enterpriseWhitepaper Accelerate your SAP transformation with IBM and AWS
-
 Tangible business value from cloud transformation remains elusive
Tangible business value from cloud transformation remains elusiveWhitepaper Discover the top five secrets to mastering cloud for business
-
 Cloud-enabled manufacturing
Cloud-enabled manufacturingWhitepaper Operations and IT leaders turn ambition into advantage
-
 DCIG: Top five enterprise Storage as A Service solutions
DCIG: Top five enterprise Storage as A Service solutionsWhitepaper Operations and IT leaders turn ambition into advantage
-
 Amplify business transformation with business intelligence
Amplify business transformation with business intelligenceWhitepaper Four key benefits of moving your operations to the cloud

