Ixia ThreatARMOR review
Ixia’s ThreatARMOR gives your firewalls a helping hand


ThreatARMOR is an elegant solution that immediately reduces the load on your firewalls and can easily pay for itself by negating the need to upgrade critical security hardware
-
+
Simple deployment, Instant protection, Detailed rap sheet reports, Local and cloud management
-
-
Irritatingly noisy fans

Enterprise security systems are at breaking point as they face an ever-increasing assault from cyber-attacks. Firewalls and security appliances aren't the only things collapsing under the pressure either as understaffed and overworked support departments are having to deal with a daily barrage of security alerts.
Ixia's ThreatARMOR provides a simple solution as it's designed to work with existing security products and make them much more effective by taking some of the load from them. The appliance fronts the network perimeter and blocks traffic coming from known bad IP addresses and untrusted countries.
Ixia has plenty of experience in this area as ThreatARMOR utilises its Application and Threat Intelligence (ATI) Research Center services. Used by Ixia's security and testing products, this subscription service provides intelligence on threats including hijacked IP address ranges, malware, botnets, C&C servers and more.
The appliances maintain the database locally which is updated as often as every five minutes. The list is not signature based so there are no issues with false positives and Ixia's ATI team rescans all IP addresses in the list at least once a day so sites that have cleaned up their act are removed.
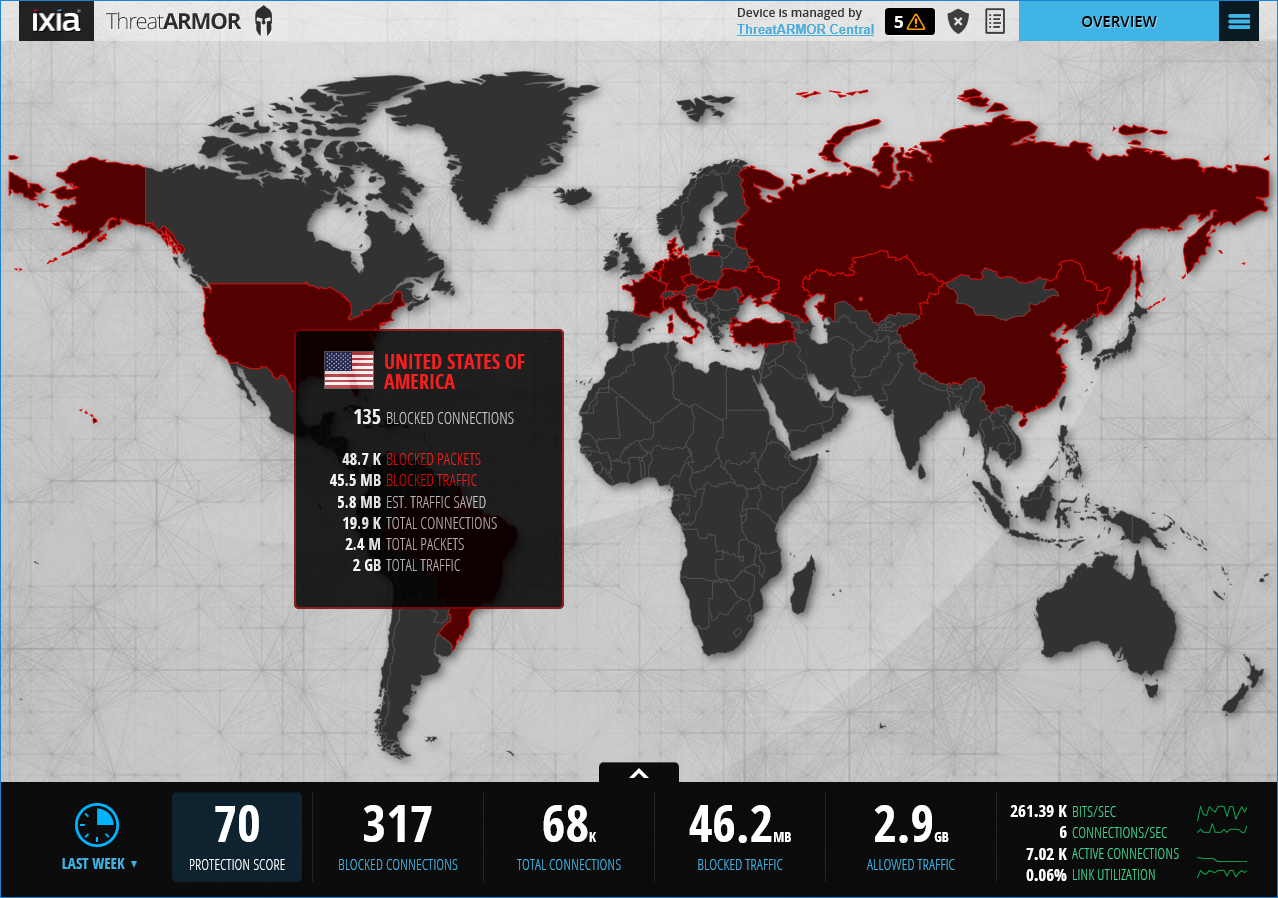
The console's Overview page shows you all you need to know about where bad traffic is coming from
Lightning deployment
On review is the ThreatARMOR 1G which has four Gigabit data ports and an extra pair of ports for local management and update downloads. Ixia also offers a 10G model offering four 10-Gigabit SFP+ data ports.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The data ports incorporate hardware bypass switches so hardware failures won't interrupt Internet access. We tested in a live environment and simply plugged our external Internet feed into the first data port and connected the second to the WAN port on our firewall.
We then linked the second pair inline between our LAN and firewall. This allowed the appliance to report on blocked traffic originating from the LAN and provide the device's real IP address.
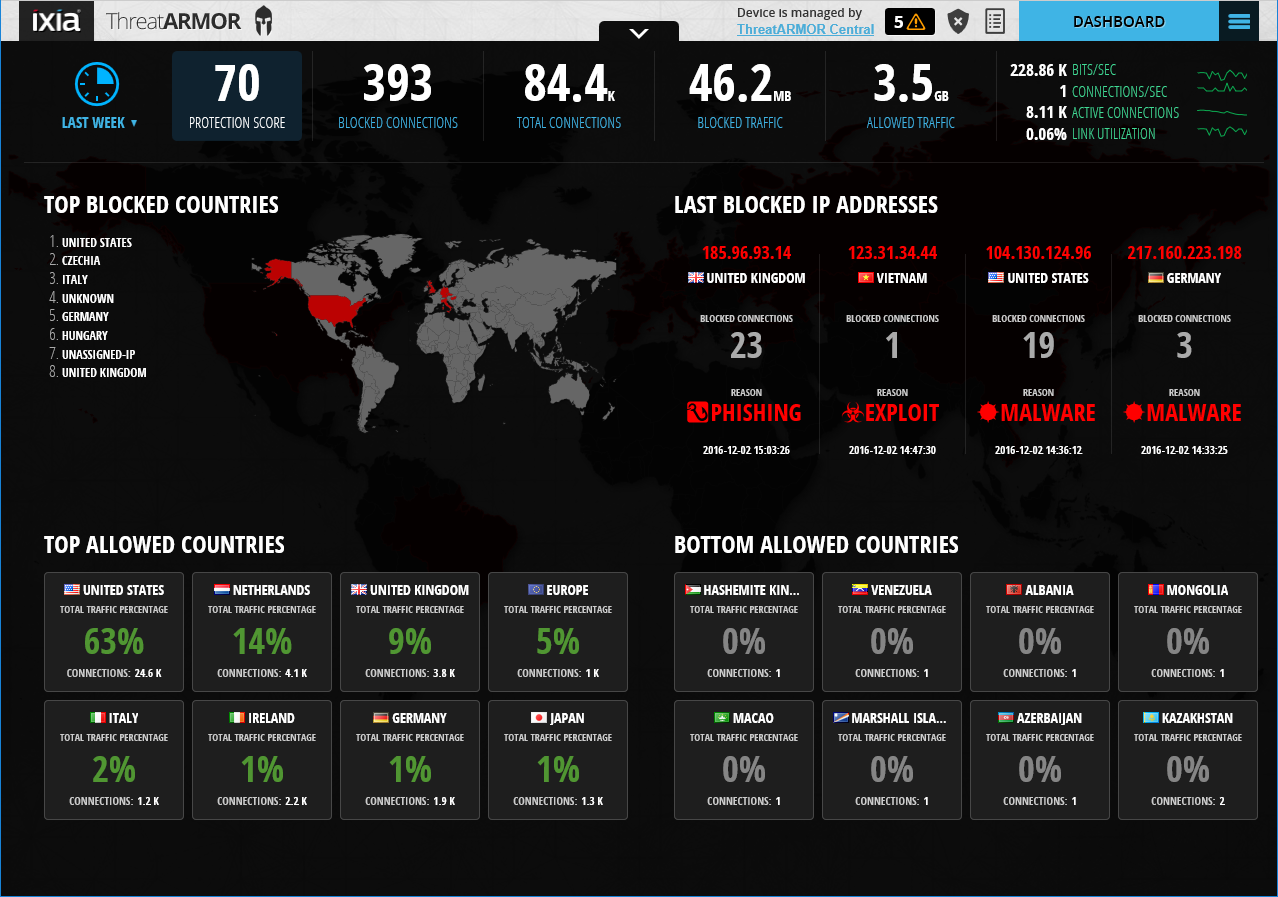
The Dashboard provides plenty of information about blocking activities and detected threats
Go forth and block
Ixia is so sure of the ThreatARMOR's simple deployment that it hasn't even written a user guide. This confidence isn't misplaced as we found it remarkably easy to use.
The home page global map shows blocked countries highlighted in red while a table below reveals a performance score along with total and blocked connections and traffic. The performance score is derived from the number of blocks relative to overall traffic volume.
For most environments, a score of 50 tells you all is working well. A much lower score suggests that the appliance hasn't been deployed correctly whereas a score closer to 100 indicates an attack or malware infection.
The Dashboard view has a smaller global map with a list of the top blocked countries alongside. To its right is a list of the last four blocked countries, IP addresses and detected threats while below are summaries of the most and least allowed countries.
The appliance defaults to a passive reporting mode which can be changed to active blocking from the Settings page. If you're worried the appliance is causing a problem you can trigger the hardware bypasses from here as well.
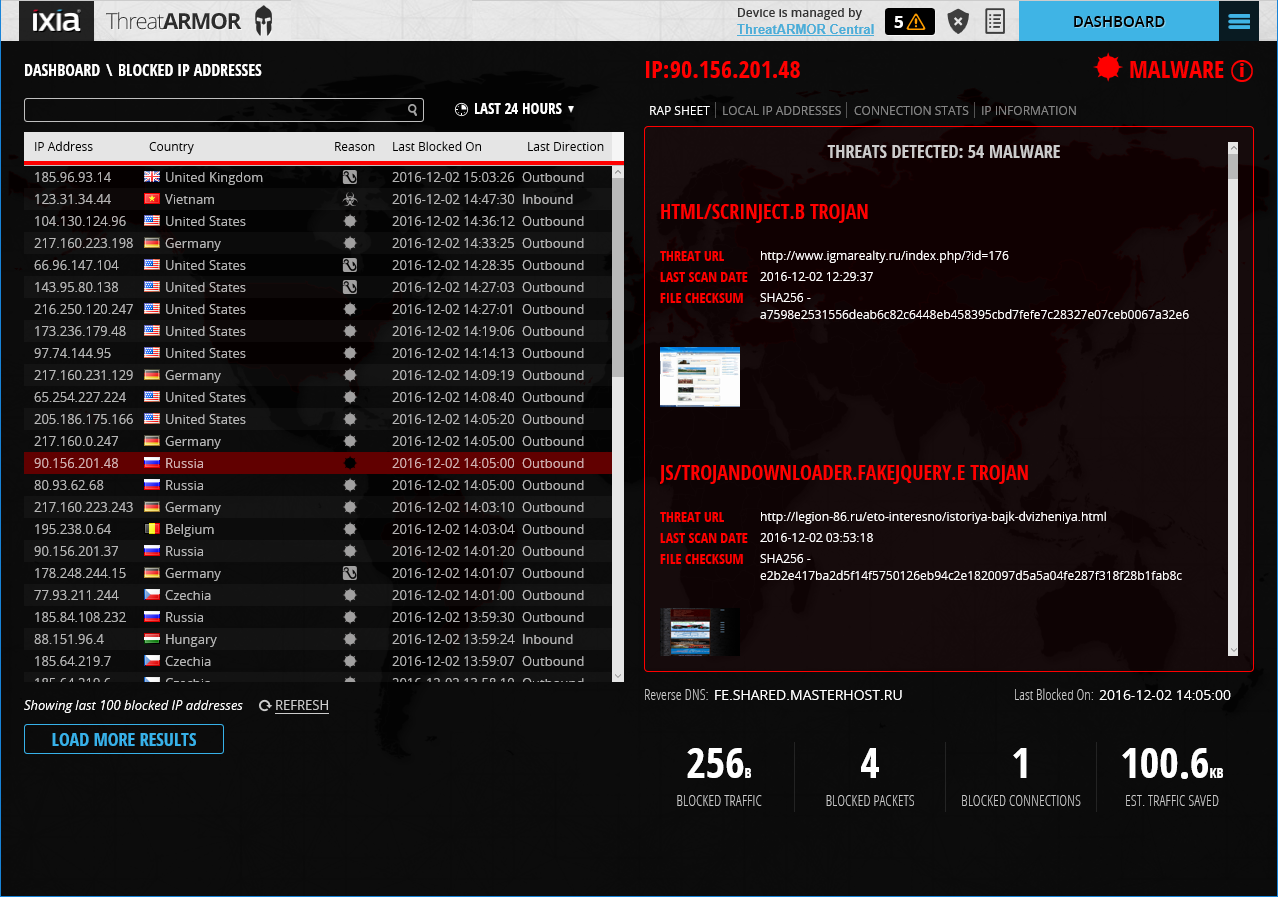
Ixia's rap sheet leaves you in no doubts as to why traffic is being blocked
Rap sheet
For testing, we ran our standard script on a LAN system which calls on around 3,500 dubious websites. Within seconds of starting it, the Dashboard began registering blocked IP addresses and showed the number of blocked connections and the reason.
ThreatARMOR uses five threat classifications malware, phishing, botnet, exploit and hijacked. Each blocked entry tells you which type it is and clicking on one in the Dashboard takes you to the Ixia rap sheet.
This provides forensics information explaining precisely why the connection was blocked. The rap sheet shows details such as the threat URL, a breakdown of attempted Trojan activities, brute force attack credentials, file checksums and even a screenshot of the offending website where applicable.
As we had two inline ports behind our firewall, we could see the local IP address of the system making the outbound connection. Other information available are connection statistics plus reverse DNS lookup results and you can permanently block or allow traffic from specific IP addresses or countries with a couple of clicks.
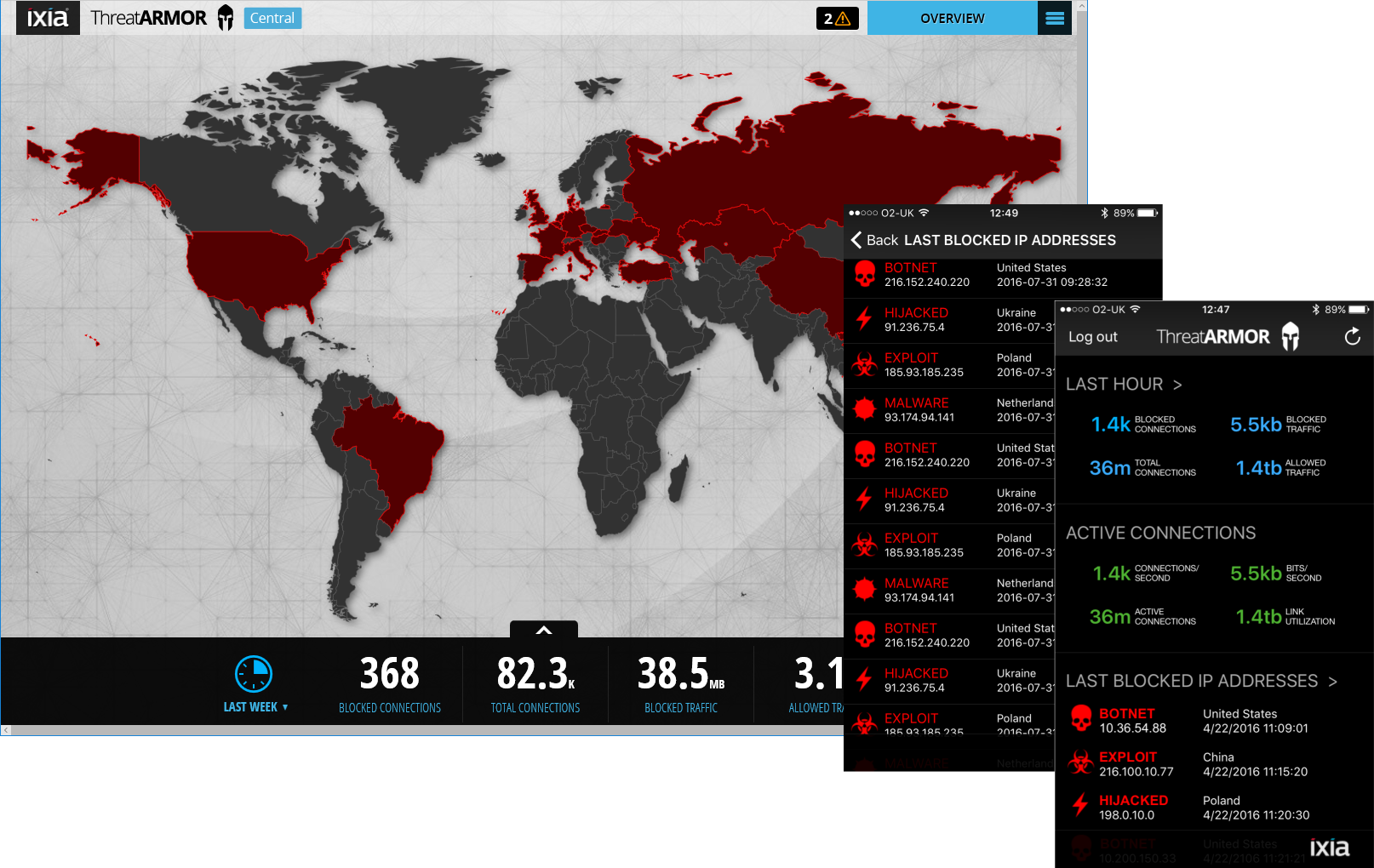
The cloud portal manages multiple appliances and links up with Ixia's iPhone app
ThreatARMOR Central
The ThreatARMOR Central portal allows you to monitor multiple appliances from the cloud. It gathers information from all centrally managed appliances and presents it in its global map and Dashboard views.
We linked the appliance to our account where it provided most of the features available from the local console. We could change the operation mode remotely but options such as network configuration, update status checks and logging can only be accessed from the local console.
The cloud portal provides a web link for each appliance which you'll need to use to see their individual protection scores. This is also required to see to see the rap sheet details on local IP addresses and connection stats.
Ixia offers an iOS app for iPhones which provides real-time statistics on the move. It can show blocked and active connections along with a list of the last blocked IP addresses and their threat classifications.
Conclusion
Enterprises suffering from a daily onslaught of cyber-attacks will find Ixia's ThreatARMOR can take the heat off their security systems and support staff. Blocking traffic from known bad IP addresses before they reach your network eases the load on critical security systems and will significantly reduce alerts.
We were impressed with the ThreatARMOR during testing (apart from its noise levels) as it provided plenty of information about blocking manoeuvres with its at-a-glance maps and dashboards. Ixia's ATI rap sheet told us all we needed to know about each blocked threat and deployment really is a piece of cake.
Verdict
ThreatARMOR is an elegant solution that immediately reduces the load on your firewalls and can easily pay for itself by negating the need to upgrade critical security hardware
Chassis: 1U rack
Storage: 200GB Intel S3610 SSD
Network: 4 x Gigabit data ports with hardware bypasses
Other: 2 x Gigabit management ports, RJ-45 serial
Management: Web browser, ThreatARMOR Central
Power: 2 x 275W hot-plug PSUs
Support: £3,158 ex VAT per year
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsers
Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsersNews Defenders advised to use runtime behavioral analysis to detect and block malicious activity at the point of execution, directly within the browser
By Emma Woollacott Published
-
 AI coding is taking off in the US – but developers in another country are “catching up fast”
AI coding is taking off in the US – but developers in another country are “catching up fast”News Developers in the United States are leading the world in AI coding practices, at least for now
By Nicole Kobie Published
-
 Veeam ramps up growth plans with trio of leadership hires
Veeam ramps up growth plans with trio of leadership hiresNews The data resilience vendor has reshaped its senior leadership team to deepen partner engagement and streamline customer success in the AI era
By Daniel Todd Published
