Remote access to businesses sold for huge profit in growing dark web operation
Researchers told IT Pro the lucrative business model is reaching 'full maturity' but has opportunities to become even more profitable in the near future


New figures indicate a rise in dark web services providing easier ways for cyber criminals to breach organisations' defences and launch cyber attacks without a significant amount of technical knowledge.
The growth of initial access brokers (IABs) has risen by 57% throughout 2021 with the business model "approaching full maturity", according to Digital Shadows, which has been tracking such underground businesses since 2014.
IABs play a significant role in modern cyber attacks "by doing the technical, dirty work" for prospective hackers, allowing them to pay only for the level of access they need to a target organisation's system and only for the amount of time they need to launch the attack and get out.
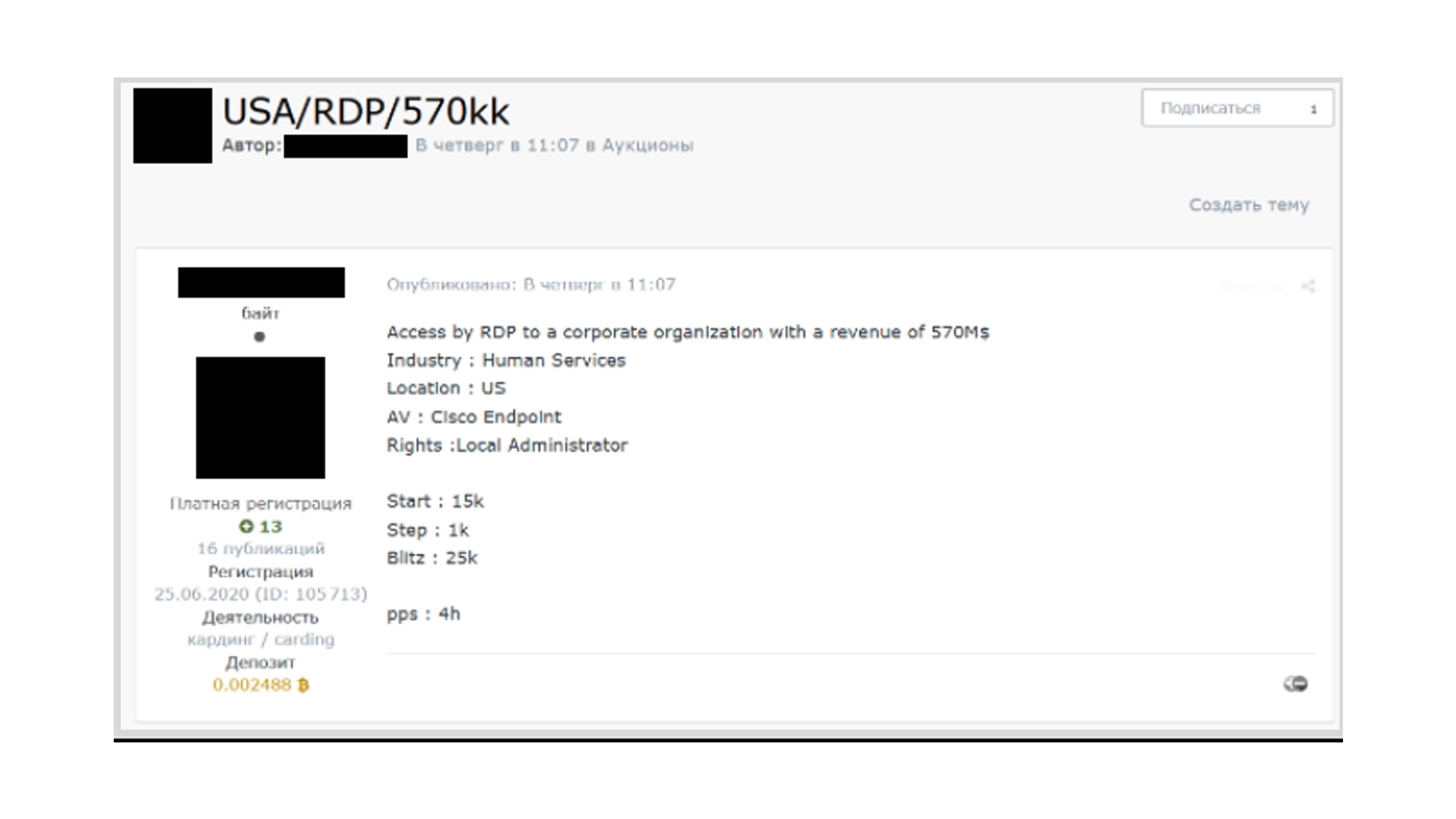
These customer and victim-agnostic brokerages typically gain access to organisations through compromised remote desktop protocol (RDP) and/or virtual private network (VPN) applications, achieved using stolen credentials or by conducting brute force attacks. They then sell access to victim's machines or company-wide systems for a fee.
This method of access was by far the most popular method identified by the cyber security company - 62.8% of all cases involved RDP and/or VPN products.
"The use of RDP and VPN has greatly expanded since the beginning of the pandemic, without any major security improvements," said Digital Shadows. "Consequently, threat actors have been able to compromise these applications and drive more malicious activity."
Pricing of the service varies depending on the level of access and access method. For example, RDP access was one of the more common types of access available to purchase, typically costing less than $1,000, and this comparatively low price can indicate access to low-level machines in an organisation.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
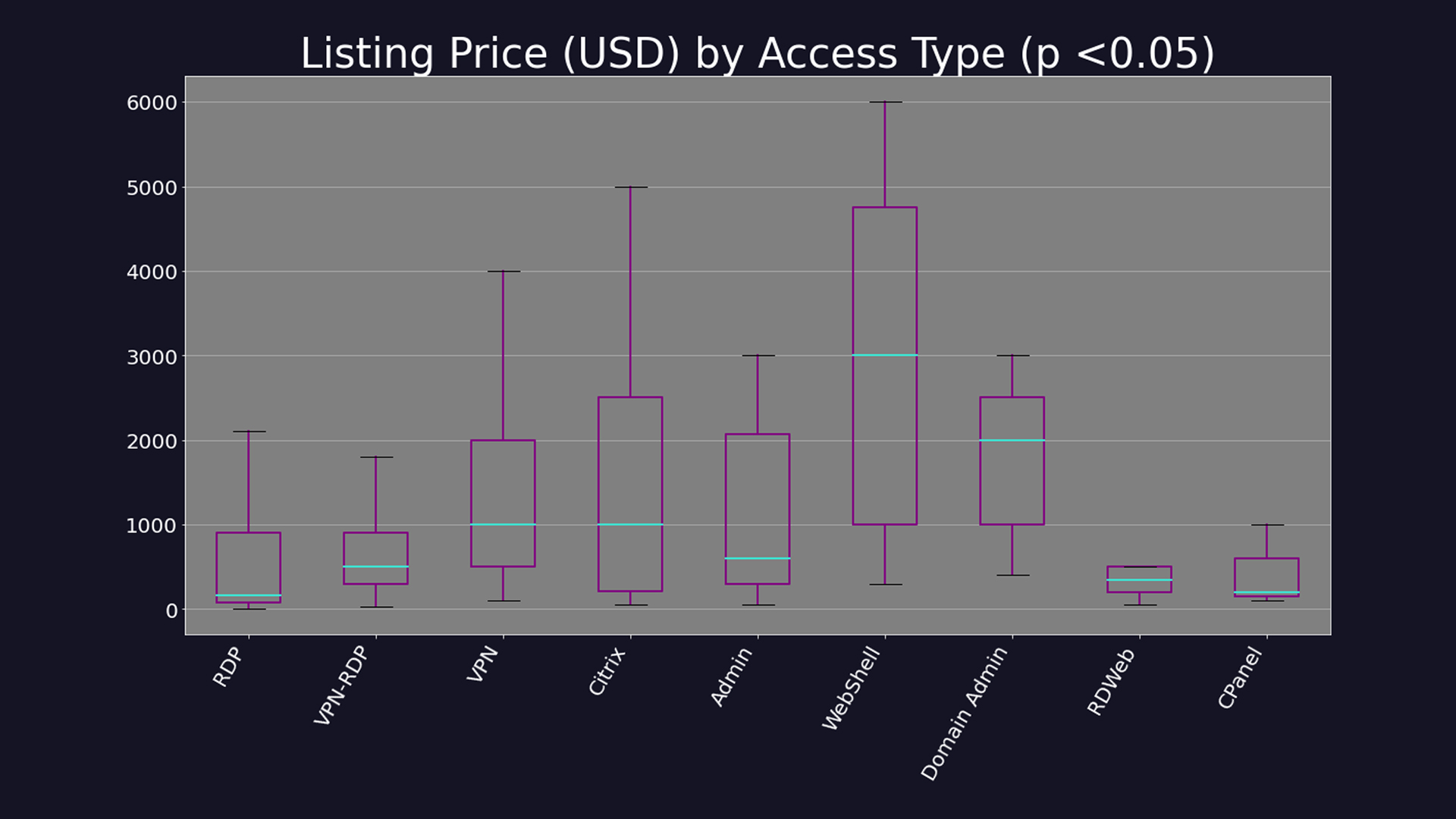
WebShell access was by far the most expensive type available to buy with listings regularly charging up to $5,000 per customer and increasing to $6,000 in some cases. The higher price and price spread (prices start as low as $200) indicated a broad range of privileges on offer depending on the machine or organisation, the researchers said.
Retail was revealed to be the most targeted industry for the second year running, according to the report, and the reason has been attributed to e-commerce sites employing weak security measures, making it easier for IABs to target them.
They also make for attractive targets given the information these types of organisations hold is easier to monetise, such as selling credit card details on dark web marketplaces.
The technology sector and industrial goods comprised the second and third-most targeted industries respectively.
"Access to tech companies can be used in a variety of ways, including to acquire sensitive data and move laterally to networks of connected organisations, similar to what happened with REvil and Kaseya," said Digital Shadows.
"Companies in industrial goods are also at risk from IAB operations given the high number of Operational Technology (OT) and Industrial Control System (ICS) devices that may be vulnerable to offensive attacks."
The researchers said the most targeted sectors are rarely the most valuable and when looking at the average price for access per sector, the figures paint a different picture.
Governmental organisations were among the least available to purchase access via IABs but the price was naturally the highest given the sensitive level of information held by such institutions. These were followed by financial services, retail, and then technology organisations.
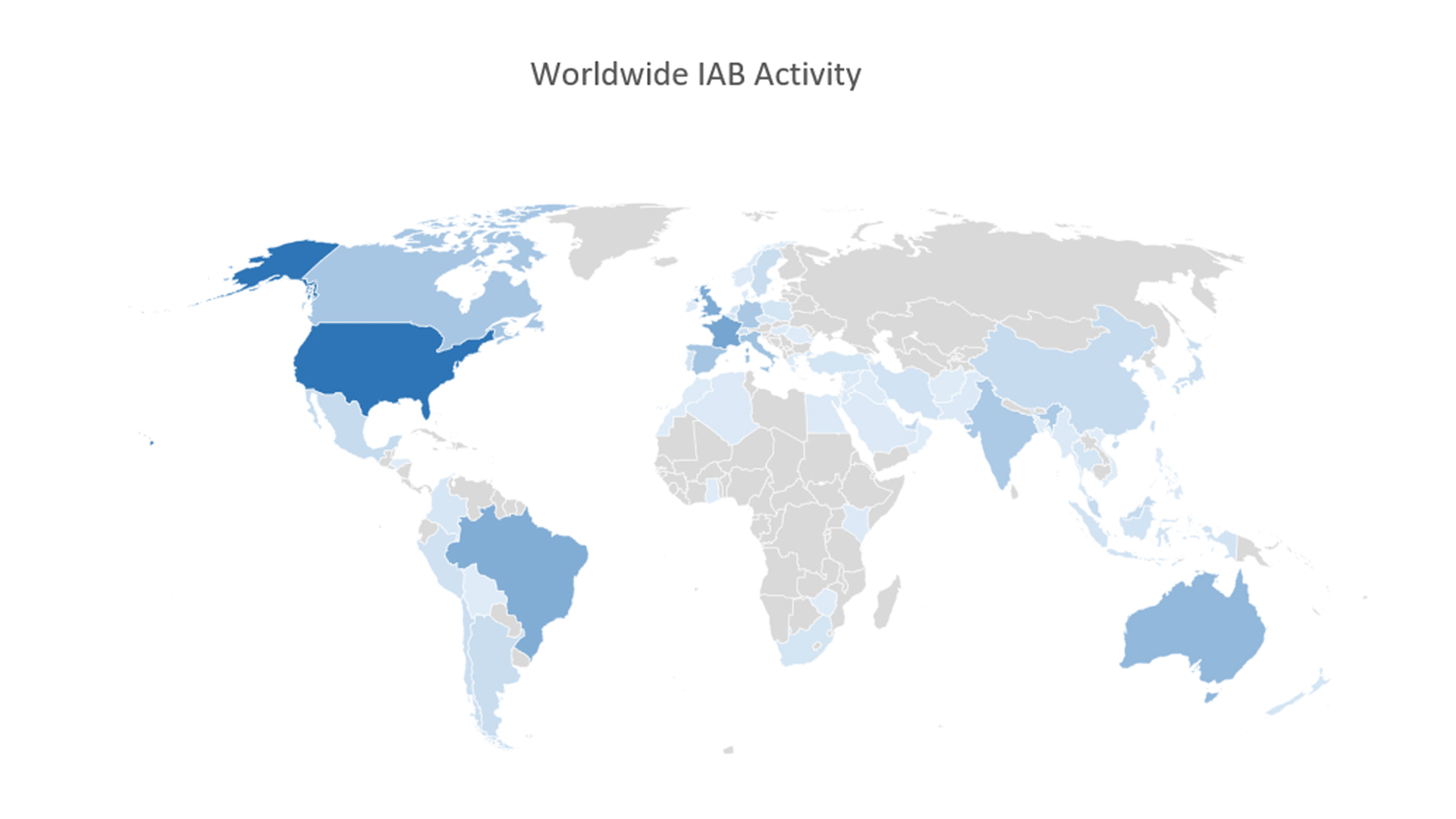
The US was the most targeted country, with France, the UK, Brazil, and Australia also among the most targeted nations. The researchers noted that most countries belonging to the Commonwealth of Independent States (CIS) were unaffected by IABs in 2021 because most operate on Russian-language cybercriminal forums and these forums formally prohibit their members from targeting CIS-based organisations.
Such forums also presented difficulties for IABs last year in the wake of high-profile ransomware attacks like the one on Colonial Pipeline. Criminal forums such as XSS, Exploit, and RaidForums all banned ransomware from their platforms after realising the massive fallout of DarkSide's attempt on US critical infrastructure.
The decision impacted IABs' most profitable clients, Digital Shadows said, but the ban has not been policed strictly so IABs have been allowed to continue operating largely undisturbed. In some cases, these brokers divulged fewer victims' data to avoid alerting security researchers and law enforcement authorities.
Method of operation
Digital Shadows has been tracking IABs since 2014 but said the business model has really taken off in the past two years, driven significantly by the pandemic and businesses investing in VPN technology to facilitate remote access.
IABs offer a unique service to cyber criminals allowing them to complete their objectives without having to go through the process of probing a target's network for entry points, and devising an attack chain to gain a foothold in the network.
These brokers have already done the 'leg work' and have devised a business model that allows them to repeatedly profit off the work, rather than attack a company once themselves and receive a reward in that way.
Trend Micro published similar findings in December 2021, noting that IAB popularity had increased and RDP/VPN connections were the most common method of access. After examining more than 1,000 underground IAB adverts, Trend Micro concluded the most common targets were schools and universities, and echoed Digital Shadows' findings that descriptions of the victims were vague; one example was simply 'big German energy company'.
RELATED RESOURCE

The best defence against ransomware
How ransomware is evolving and how to defend against it
"Right now, IABs’ market is as mature as ever," said Digital Shadows. "In 2021, we observed access listings targeting a wider number of sectors and countries than any previous year. Additionally, although the usual suspects remain at the top of the list, IABs seem to be experimenting with exploiting a bigger number of software and applications to gain—and then sell—initial access to victims’ environments."
Asked about the potential for future growth opportunities for IABs, Stefano De Blasi, threat researcher at Digital Shadows told IT Pro that these businesses may seek to scale their operations by removing the reliance on services like underground forums.
"Currently their business model is still heavily reliant on manual, time-consuming communication processes to buy IAB access which relies on private communications and the use of third party forums to converse with customers," he said. "Should they remove some of these barriers and make their process more scalable – in a fashion similar to those used for Automated Vending Carts, then the problem could increase and additional threat actors could come into the market."

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
-
 The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to know
The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to knowNews The group appears to be infecting support and help-desk personnel with remote access trojans and other forms of malware
-
 Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposed
Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposedNews No ransom has been paid, said president and group CEO Atsushi Katsuki, and the company is restoring its systems
-
 The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'
The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'News Media Land offers 'bulletproof' hosting services used for ransomware and DDoS attacks around the world
-
 A notorious ransomware group is spreading fake Microsoft Teams ads to snare victims
A notorious ransomware group is spreading fake Microsoft Teams ads to snare victimsNews The Rhysida ransomware group is leveraging Trusted Signing from Microsoft to lend plausibility to its activities