Lenovo ThinkPads vulnerable to privilege escalation exploit, researchers warn
A component running on the popular business computers is vulnerable to a chained exploit that grants full access to attackers


Users of Lenovo's range of ThinkPad workstations have been warned to patch their systems following the discovery of flaws that allows hackers to launch privilege escalation attacks.
It's believed that two separate flaws can be chained together to target the ImControllerService component and change a user's access level to a system, according to security researchers at NCC Group.
The ImControllerService is a component present on Lenovo's ThinkPad hardware range and controls tasks such as system power management and app and driver updates.
The vulnerability can be triggered by exploiting two flaws, tracked as CVE-2021-3922 and CVE-2021-3969, affecting the way in which the ImControllerService handles the execution of highly privileged child processes, NCC Group said.
The normal running of a system will have the ImControllerService periodically start child processes that open named pipe servers. These named pipe servers connect to the parent process in order to retrieve and execute the necessary XML serialised commands.
One of these commands is to load a plugin from an arbitrary location on the system. The child process is required to validate the digital signature of the plugin dynamic-link library (DLL) before loading and executing the file.
However, hackers are able to hijack this process in order to change privileges and load any payload of their choosing onto the machine.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE

Modernise endpoint protection and leave your legacy challenges behind
The risk of keeping your legacy endpoint security tools
The first vulnerability lies in the fact that the child process fails to check whether the source of the initial connection is legitimate. This creates a race condition that effectively sees the hacker try and make a connection with the named pipe ahead of the parent process.
"An attacker using high-performance filesystem synchronisation routines can reliably win the race with the parent process to connect to the named pipe," said NCC Group. During testing NCC Group’s proof of concept code never failed to connect to the named pipe before the parent service could do so.
"Because the child process does not validate the source of the connection it will begin accepting commands from the attacker after the race condition has been exploited."
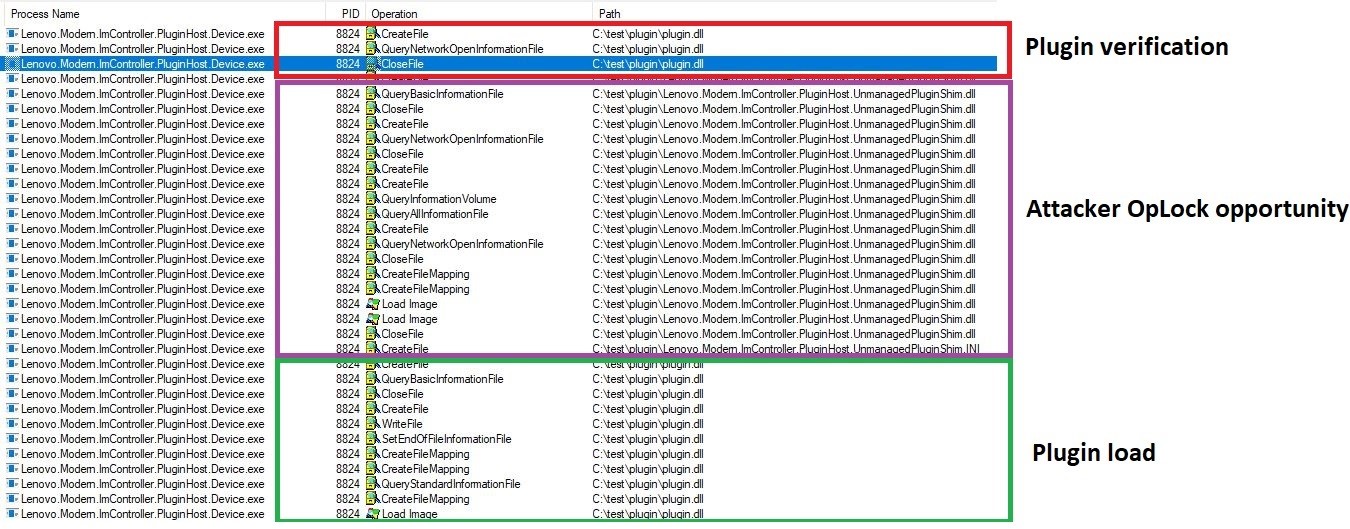
The second vulnerability is a time-of-check to time-of-use flaw, which stems from how the child process validates the plugin it's being asked to load. When loading a DLL, the child process validates its authenticity by checking if it's signed by Lenovo.
However, attackers can use opportunistic locking (OpLocks) on a file to stall the validation process long enough for them to load their own DLL. Once the lock is released, the machine will load the DLL of the attacker's choosing which leads to privilege escalation.
Lenovo has released an advisory in which it warns users to patch machines to the latest IMController version (version 1.1.20.3). The component is automatically updated by the Lenovo System Interface Foundation Service, which means the update can be triggered by rebooting the machine or manually restarting the 'System Interface Foundation Service' service, it said.
It's currently unclear how many Lenovo machines were, or currently are, thought to be affected globally, but Lenovo told IT Pro: "Lenovo worked with NCC in line with industry best practices and fixed the issue in November and customers are already protected."

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 The modern workplace: Standardizing collaboration for the enterprise IT leader
The modern workplace: Standardizing collaboration for the enterprise IT leaderHow Barco ClickShare Hub is redefining the meeting room
-
 CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do that
CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do thatNews The incident at CISA raises yet more concerns about the rise of ‘shadow AI’ and data protection risks
-
 Experts welcome EU-led alternative to MITRE's vulnerability tracking scheme
Experts welcome EU-led alternative to MITRE's vulnerability tracking schemeNews The EU-led framework will reduce reliance on US-based MITRE vulnerability reporting database
-
 Veeam patches Backup & Replication vulnerabilities, urges users to update
Veeam patches Backup & Replication vulnerabilities, urges users to updateNews The vulnerabilities affect Veeam Backup & Replication 13.0.1.180 and all earlier version 13 builds – but not previous versions.
-
 Two Fortinet vulnerabilities are being exploited in the wild – patch now
Two Fortinet vulnerabilities are being exploited in the wild – patch nowNews Arctic Wolf and Rapid7 said security teams should act immediately to mitigate the Fortinet vulnerabilities
-
 Everything you need to know about Google and Apple’s emergency zero-day patches
Everything you need to know about Google and Apple’s emergency zero-day patchesNews A serious zero-day bug was spotted in Chrome systems that impacts Apple users too, forcing both companies to issue emergency patches
-
 Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updated
Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updatedNews CVE data is vital in combating emerging threats, yet inaccurate ratings and lengthy wait times are placing enterprises at risk
-
 IBM AIX users urged to patch immediately as researchers sound alarm on critical flaws
IBM AIX users urged to patch immediately as researchers sound alarm on critical flawsNews Network administrators should patch the four IBM AIX flaws as soon as possible
-
 Critical Dell Storage Manager flaws could let hackers access sensitive data – patch now
Critical Dell Storage Manager flaws could let hackers access sensitive data – patch nowNews A trio of flaws in Dell Storage Manager has prompted a customer alert
-
 Flaw in Lenovo’s customer service AI chatbot could let hackers run malicious code, breach networks
Flaw in Lenovo’s customer service AI chatbot could let hackers run malicious code, breach networksNews Hackers abusing the Lenovo flaw could inject malicious code with just a single prompt