What is Dark Utilities C2 as a service (C2aaS)?
Hackers can use the service to launch cyber attacks with ease for as little as £8.50


Command and control (C2) infrastructure forms the backbone of many malware campaigns targeting businesses and organisations. It’s especially useful for attackers looking to conduct remote operations, allowing them to maintain connections with infected systems and deploy various payloads from afar.
C2 as a service (C2aaS) isn’t a novel idea, and has been a fixture as far back as 2015 with the Quaverse remote access Trojan (QRAT). A new tool called Dark Utilities, however, has seen hackers flock to the C2aaS platform because of how easy and affordable it can be to launch successful malware attacks using it.
Priced at just €9.99 (approximately £8.50), and established in early 2022, Dark utilities already has more than 3,000 registered users, with this figure rising. Its low cost and comprehensive set of features make it an attractive tool to a wide variety of cyber criminals, according to Cisco Talos.
What is Dark Utilities, and what can it do?
The C2aaS platform targets machines using either Windows or Linux, while support exists for Python implementations. Active development is also underway to expand its list of compatible targets, the researchers say. For example, the most recent additions to the platform is support for ARM64 and ARMV71 architectures opening up the platform’s use against other internet-connected devices like Wi-Fi routers.
Dark Utilities allows customers to deploy a range of services once the initial access to the target network has been secured. Remote system access, botnets, distributed denial of services (DDoS) capabilities, and cryptocurrency mining are among the headline features.
Customers also have access to dedicated Discord and Telegram communities that are run by the platform’s developers. It’s here where technical issues can be resolved and other assistance can be provided to the wider customer base. Its Discord channel also serves as the customer authentication platform and, upon authentication, provides users with a status indicator dashboard alongside metrics on the platform’s real-time performance.
The malicious payloads provided by Dark Utilities are also hosted within the Interplanetary File System (IPFS) – a peer-to-peer network designed so that content moderators or law enforcement can’t intervene or otherwise remove the content from there. This means the payloads Dark Utilities uses are unlikely to be tampered with or removed by any central authority, making for effective and well-designed tooling.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“These platforms provide a variety of sophisticated capabilities to adversaries who may otherwise be unable to develop them on their own,” says Talos. “They effectively lower the barrier to entry for cybercriminals entering the threat landscape and enable them to quickly begin launching attacks targeting a variety of operating systems.”
What services does Dark Utilities offer?
Dark Utilities: Botnets
Registering new bots with the platform requires a new payload to be built and successfully installed on a target machine. Once the connection can be established, the bot will then become visible to the attacker in a management platform which details all the systems that the attacker can access. It’s from here where hackers can launch DDoS attacks, cryptomining, and remote code execution.
The Dark Utilities dashboard
The platform itself provides documentation for customers and step-by-step instructions on how to perform network reconnaissance in order to find exploitable vulnerabilities in servers that can be used to infect targets, facilitating the initial foothold.
“Given the low cost associated with the platform and the amount of functionality it provides, it is likely that this will continue to be increasingly popular with threat actors seeking to build botnets without requiring significant amounts of time and effort to develop their own malware,” Talos says.
Dark Utilities: DDoS
The C2aaS platform offers support for two types of DDoS attack: layer 4 and layer 7, researchers say.
Layer 4 DDoS attacks support transmission control protocol (TCP), user datagram protocol (UDP) and internet control message protocol (ICMP), as well as pre-built support for attacks within popular video games like Counter-Strike: Global Offensive and Among Us.
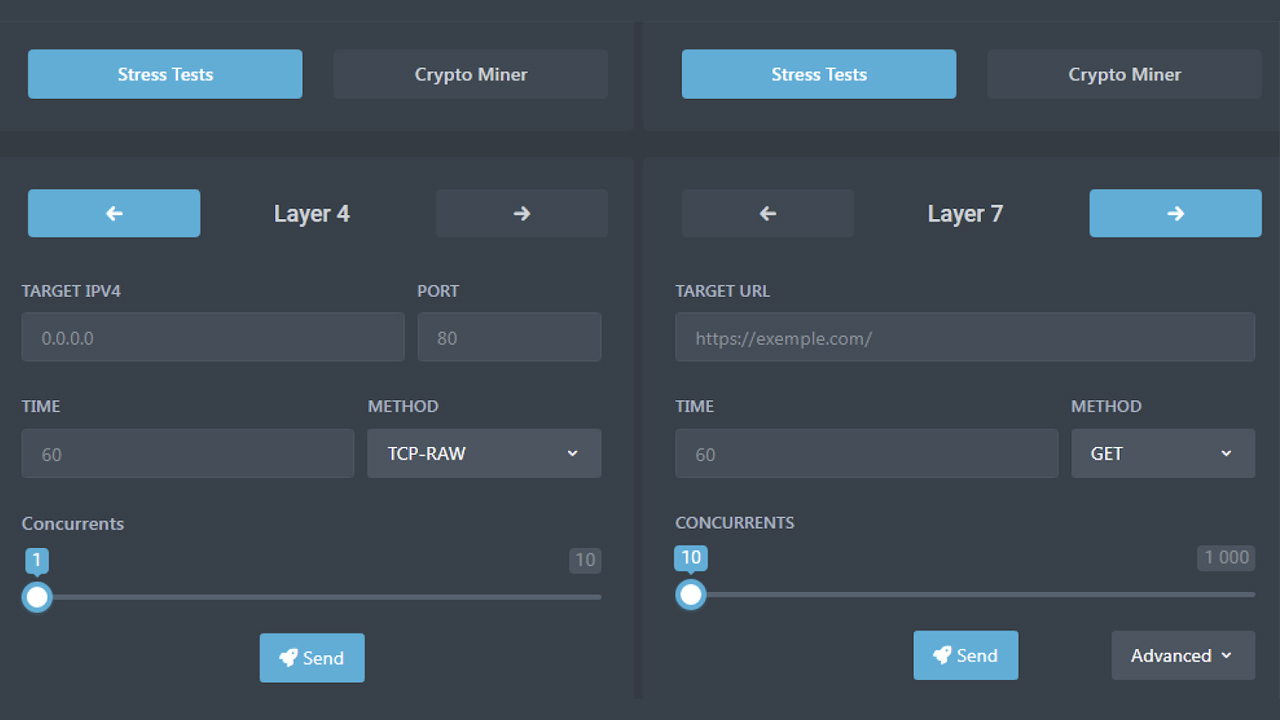
The Dark Utilities user interface
Layer 7 DDoS attacks support a swathe of HTTP methods such as GET, POST, HEAD, PATCH, PUT, DELETE, OPTIONS, and CONNECT. The platform provides users with a polished graphical user interface (GUI) through which each type of attack can be configured.
Dark Utilities: Cryptomining
The supported mining capability is for the Monero cryptocurrency – one favoured by cyber criminals due to the way in which it anonymises the users that have been involved in transactions.
If the mining option is deployed by the attacker when building the payload, a script will execute, downloading the XMRig mining tool via an IPFS gateway and executing it on the system. The tool will also self-terminate if the Windows Task Manager application is executed, for example, to evade detection.
Who created Dark Utilities?
Little is known about the developer, or development team, behind the tool that’s ballooning in popularity. Talos’ research revealed the lead developer could be one that goes by the online handle of Inplex-sys.
Although the individual seems to have a limited presence on underground forums, suggesting they are relatively new to the industry, previous posts indicate they're a French speaker, but they can also speak English. A Doxbin account matching the handle revealed a location set as Germany, but the researchers believe this was a mistake, or misdirection.
A user with the same handle has also been found promoting the tool in a variety of online communities, including via the LAPSU$ hacking group which found notoriety in early 2022 after claiming attacks on Nvidia and Okta.
Included in promotional messages were also mentions for Smart Bot and Omega Project, alongside Dark Utilities. Smart Bot is a tool for launching spam attacks against users of Discord and the Twitch streaming site, while the Omega Project appears to be a server administration service.
Administrators concerned about the threat posed by Dark Utilities can use Talos’ catalogue of indicators of compromise (IOCs) as a reference for threat hunting.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.

