Microsoft releases Fusion ransomware detection tool for Azure
Fusion Detection for Ransomware uses machine learning to spot malicious activity across a user's network


Microsoft has released a new ransomware detection feature for Azure that uses machine learning to spot potential attacks.
'Fusion Detection for Ransomware' will send an alert to customers when it observes actions that are "potentially associated with ransomware activities".
The alerts will inform users of what was detected, and on which device, with the system correlating data from other Azure services, such as Azure Defender, Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Cloud App Security, and Azure Sentinel scheduled analytics rules.
Once ransomware activities are detected and correlated by the Fusion's machine learning model, a high severity incident with the label "Multiple alerts possibly related to Ransomware activity detected" will be triggered in the customer's Azure Sentinel workspace (shown in the image below).
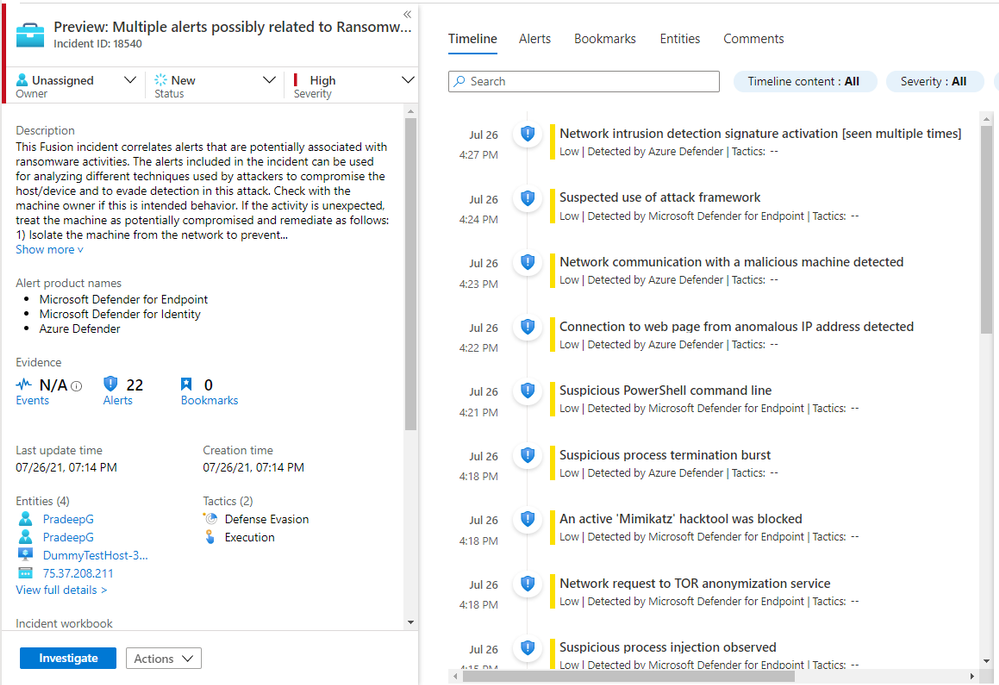
After an alert has been sent, Microsoft recommends users check the device/host in question to see if its behaviour is "unexpected". If so, the user should treat the machine as "potentially compromised" and take immediate actions, such as isolating the machine from the network, running full anti-virus scans, and investigating the rest of the network for similar signs.
Ransomware has become a lucrative occupation, according to a recent report from Unit 42, with average payouts almost doubling over the past year. Since 2020, payouts for successful ransomware attacks have increased 82% to a record $570,000 in the first half of 2021. The increase followed the previous year's 171% jump to more than $312,000.
"Preventing such attacks in the first place would be the ideal solution but with the new trend of 'ransomware as a service' and human operated ransomware, the scope and the sophistication of attacks are increasing - attackers are using slow and stealth techniques to compromise network, which makes it harder to detect them in the first place," Microsoft security researcher Sylvie Liu wrote in a blog post.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
-
 The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to know
The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to knowNews The group appears to be infecting support and help-desk personnel with remote access trojans and other forms of malware
-
 Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposed
Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposedNews No ransom has been paid, said president and group CEO Atsushi Katsuki, and the company is restoring its systems
-
 The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'
The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'News Media Land offers 'bulletproof' hosting services used for ransomware and DDoS attacks around the world
-
 A notorious ransomware group is spreading fake Microsoft Teams ads to snare victims
A notorious ransomware group is spreading fake Microsoft Teams ads to snare victimsNews The Rhysida ransomware group is leveraging Trusted Signing from Microsoft to lend plausibility to its activities
