Apple’s new iPhone bug-hunting scheme branded a “poison pill"
Researchers baulk at hefty restrictions such as being bound to silence during a limitless disclosure window

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
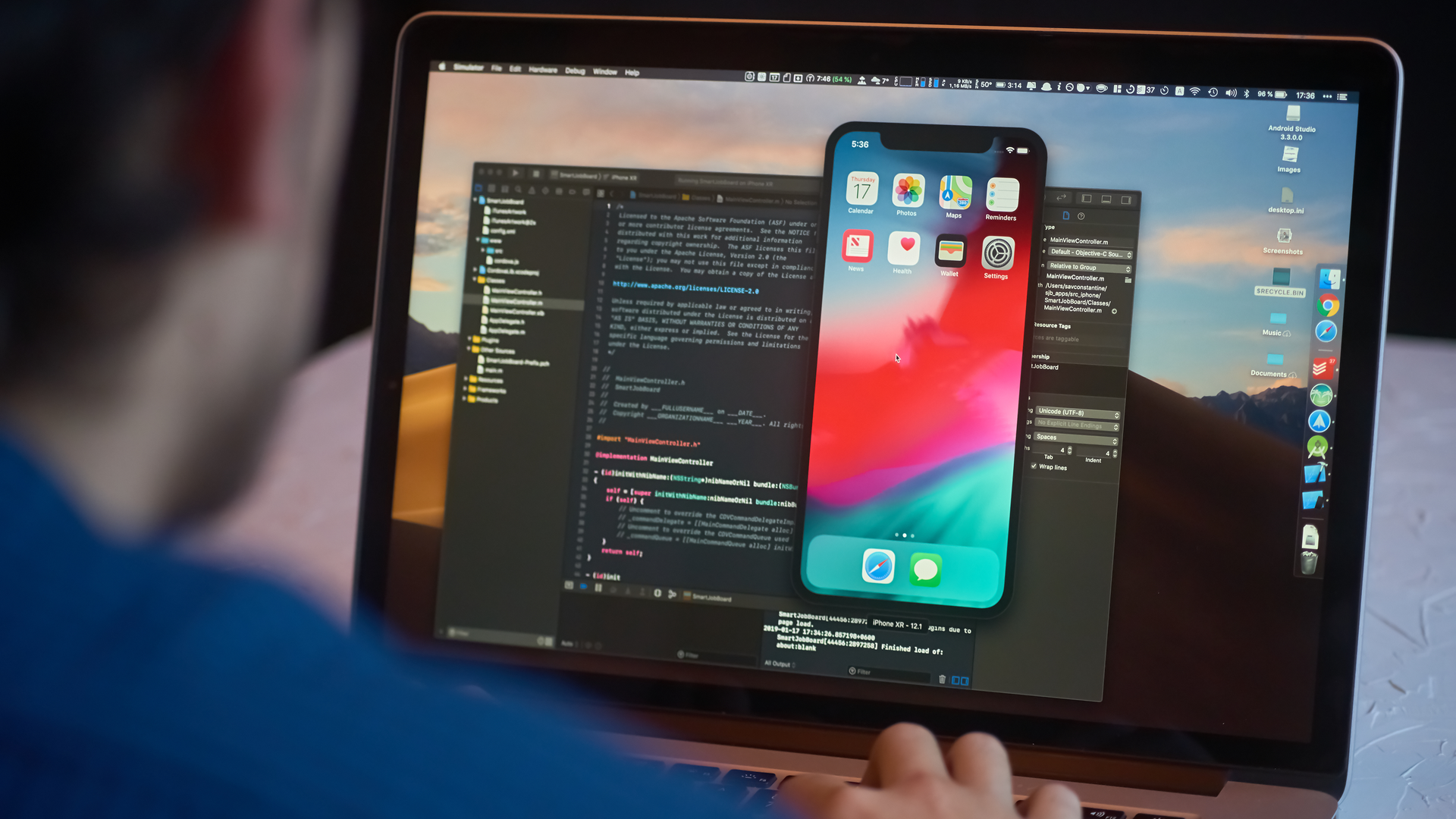
Researchers have expressed frustration at the terms of an Apple bug bounty scheme in which special iPhones will be shipped out in the hope device and iOS vulnerabilities can be fixed more effectively.
Some voices in the security community have lamented restrictions in the Security Research Device Program (SRDP) which prevent them from publicly or privately disclosing any flaws until Apple sets its own disclosure date. This restriction, in addition to strict rules on how the iPhones can be used, has led some to describe the scheme as a "poison pill".
This SRDP was first announced in August last year at the Black Hat security conference, with no suggestion as to why it’s taken so long for the programme to be launched. Apple said at the time that it wanted to attract some of the most exceptional researchers that have been focusing their time on other platforms.
These devices are “dedicated exclusively to security research”, with unique code execution and containment policies. They also behave as closely to standard iPhones as possible, although shell access is available and researchers can run any tools on them.
They are not meant for personal use or daily carry, however, and must remain on the premises of participants at all times. All verified vulnerabilities, meanwhile, are legally required to be reported to Apple immediately, or the appropriate third party if the bug is found in third-party code.
Apple will then provide participants with a publication date, up to which point participants are restricted from discussing the vulnerability with anybody else, let alone in public.
This aspect of the scheme is proving to be a major sticking point for many, given Apple hasn’t committed to any particular disclosure window or timeline. Effectively, that means researchers can be ‘gagged’ for an indefinite period until Apple decides to set a publication date.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE

Introducing VMDR: Vulnerability Management, Detection and Response
The all-in-one vulnerability management service
“Apple has no reason to give you a publication date until they decide they want to give you one,” one iOS jailbreaker told IT Pro, adding in a tweet that that participation was “a poison pill”.
“They could take as long as they want. You could be under NDA essentially forever. Disclosure deadlines are standard practice in the industry. They give vendors an incentive to address issues promptly.”
They also highlighted an explanation from Google as to why its Project Zero research programme has a 90-day disclosure window, chiefly, that it incentivises developers to fix vulnerabilities found in their code at a much faster pace.
Apple insists that it will work in good faith to resolve each vulnerability as soon as is practical, and that it will usually provide participating researchers with a publication date.
Researchers who are already a member of the Apple Developer Program can apply to participate in the programme, and will soon begin receiving special iPhones on a 12-month renewable loan should they qualify.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 AWS CEO Matt Garman isn’t convinced AI spells the end of the software industry
AWS CEO Matt Garman isn’t convinced AI spells the end of the software industryNews Software stocks have taken a beating in recent weeks, but AWS CEO Matt Garman has joined Nvidia's Jensen Huang and Databricks CEO Ali Ghodsi in pouring cold water on the AI-fueled hysteria.
-
 Deepfake business risks are growing
Deepfake business risks are growingIn-depth As the risk of being targeted by deepfakes increases, what should businesses be looking out for?
-
 CVEs are set to top 50,000 this year, marking a record high – here’s how CISOs and security teams can prepare for a looming onslaught
CVEs are set to top 50,000 this year, marking a record high – here’s how CISOs and security teams can prepare for a looming onslaughtNews While the CVE figures might be daunting, they won't all be relevant to your organization
-
 Microsoft patches six zero-days targeting Windows, Word, and more – here’s what you need to know
Microsoft patches six zero-days targeting Windows, Word, and more – here’s what you need to knowNews Patch Tuesday update targets large number of vulnerabilities already being used by attackers
-
 Experts welcome EU-led alternative to MITRE's vulnerability tracking scheme
Experts welcome EU-led alternative to MITRE's vulnerability tracking schemeNews The EU-led framework will reduce reliance on US-based MITRE vulnerability reporting database
-
 Veeam patches Backup & Replication vulnerabilities, urges users to update
Veeam patches Backup & Replication vulnerabilities, urges users to updateNews The vulnerabilities affect Veeam Backup & Replication 13.0.1.180 and all earlier version 13 builds – but not previous versions.
-
 Two Fortinet vulnerabilities are being exploited in the wild – patch now
Two Fortinet vulnerabilities are being exploited in the wild – patch nowNews Arctic Wolf and Rapid7 said security teams should act immediately to mitigate the Fortinet vulnerabilities
-
 Everything you need to know about Google and Apple’s emergency zero-day patches
Everything you need to know about Google and Apple’s emergency zero-day patchesNews A serious zero-day bug was spotted in Chrome systems that impacts Apple users too, forcing both companies to issue emergency patches
-
 Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updated
Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updatedNews CVE data is vital in combating emerging threats, yet inaccurate ratings and lengthy wait times are placing enterprises at risk
-
 IBM AIX users urged to patch immediately as researchers sound alarm on critical flaws
IBM AIX users urged to patch immediately as researchers sound alarm on critical flawsNews Network administrators should patch the four IBM AIX flaws as soon as possible