Why the Raspberry Pi's immune to the Meltdown and Spectre bugs
The tiny $35 microcomputer is your safest bet to avoid the crippling chip flaws

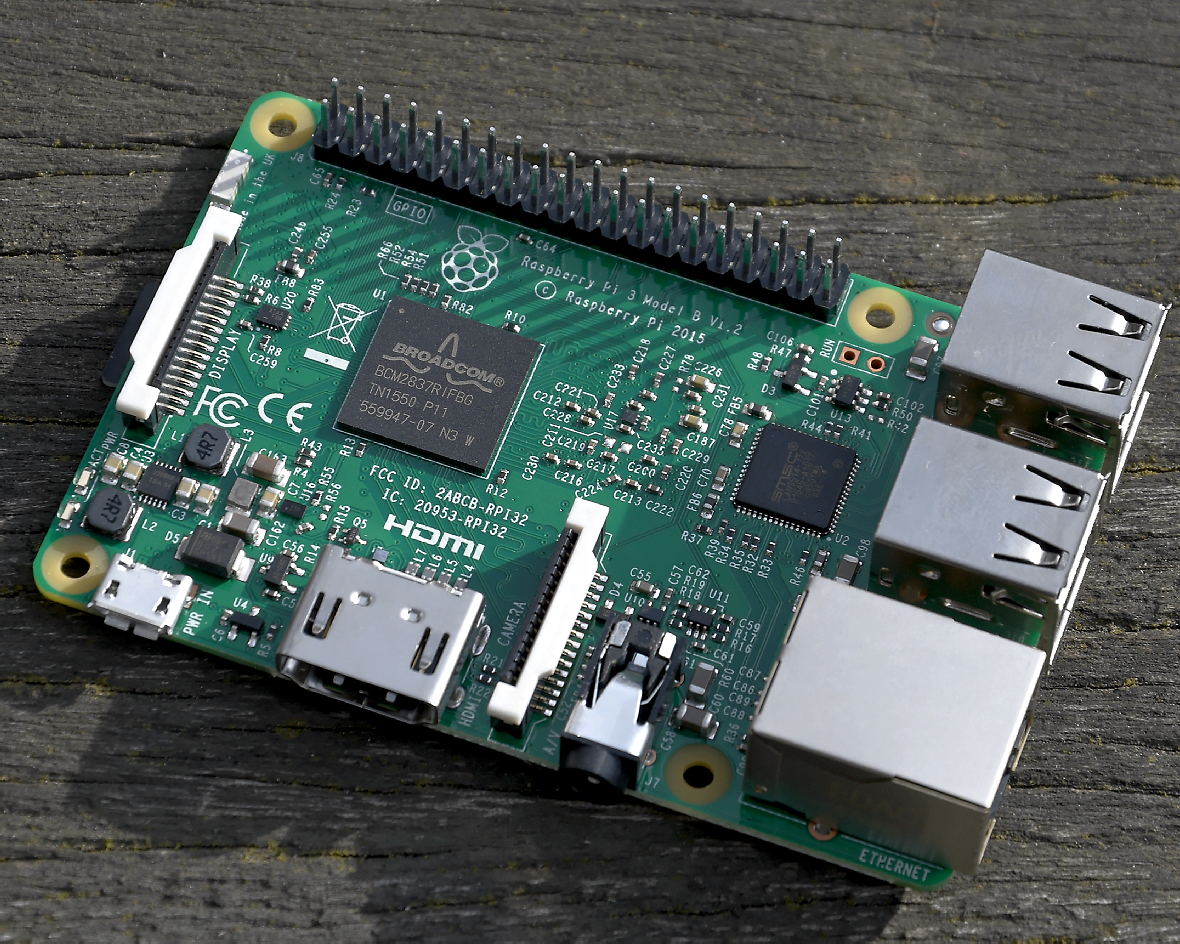
While the Meltdown and Spectre CPU flaws have caused widespread security issues for expensive, high-end computers using Intel, ARM and AMD chips, there's one processor that remains blissfully unaffected - the humble Raspberry Pi.
The $35 microcomputer (as well as all of its variants) is not vulnerable to the recently discovered bugsbecause the CPU it uses does not utilise out-of-order processing, the Raspberry Pi Foundation revealed last Friday.
Meltdown and Spectre allow attackers to read data from locations in a chip system kernel's address space and current address space respectively, exploiting flaws in the way CPUs employ caching and speculative execution.
"Modern processors go to great lengths to preserve the abstraction that they are in-order scalar machines that access memory directly," Raspberry Pi founder Eben Upton explained in a blog post, "while in fact using a host of techniques including caching, instruction reordering, and speculation to deliver much higher performance than a simple processor could hope to achieve."
"Meltdown and Spectre are examples of what happens when we reason about security in the context of that abstraction, and then encounter minor discrepancies between the abstraction and reality. The lack of speculation in the ARM1176, Cortex-A7, and Cortex-A53 cores used in Raspberry Pi render us immune to attacks of the sort."
So while your top-of-the-range work device might be vulnerable to hackers, your garage Pi project remains happily safe from the threat.
Researchers have noted that while newer and more powerful machines are rendered vulnerable by this bug, older 'obsolete' machines remain secure. As an experiment, engineer and NUS School of Computing graduate Yeo Kheng Meng managed to get a modern Linux distro running on a 25-year-old IBM PC from 1993 - an x86 machine that isn't vulnerable to Meltdown or Spectre due to the fact that it doesn't support out-of-order processing.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Adam Shepherd has been a technology journalist since 2015, covering everything from cloud storage and security, to smartphones and servers. Over the course of his career, he’s seen the spread of 5G, the growing ubiquity of wireless devices, and the start of the connected revolution. He’s also been to more trade shows and technology conferences than he cares to count.
Adam is an avid follower of the latest hardware innovations, and he is never happier than when tinkering with complex network configurations, or exploring a new Linux distro. He was also previously a co-host on the ITPro Podcast, where he was often found ranting about his love of strange gadgets, his disdain for Windows Mobile, and everything in between.
You can find Adam tweeting about enterprise technology (or more often bad jokes) @AdamShepherUK.
-
 Will autonomous robotics leap forward in 2026?
Will autonomous robotics leap forward in 2026?In-depth Connectivity and cost benefits remain barriers, despite breakthroughs in physical AI
-
 AWS and NTT Data team up to drive legacy IT modernization in Europe
AWS and NTT Data team up to drive legacy IT modernization in EuropeNews Partnership between AWS and NTT DATA aims to boost AWS European Sovereign Cloud capabilities
-
 Experts welcome EU-led alternative to MITRE's vulnerability tracking scheme
Experts welcome EU-led alternative to MITRE's vulnerability tracking schemeNews The EU-led framework will reduce reliance on US-based MITRE vulnerability reporting database
-
 Veeam patches Backup & Replication vulnerabilities, urges users to update
Veeam patches Backup & Replication vulnerabilities, urges users to updateNews The vulnerabilities affect Veeam Backup & Replication 13.0.1.180 and all earlier version 13 builds – but not previous versions.
-
 Two Fortinet vulnerabilities are being exploited in the wild – patch now
Two Fortinet vulnerabilities are being exploited in the wild – patch nowNews Arctic Wolf and Rapid7 said security teams should act immediately to mitigate the Fortinet vulnerabilities
-
 Everything you need to know about Google and Apple’s emergency zero-day patches
Everything you need to know about Google and Apple’s emergency zero-day patchesNews A serious zero-day bug was spotted in Chrome systems that impacts Apple users too, forcing both companies to issue emergency patches
-
 The Microsoft bug bounty program just got a big update — and even applies to third-party code
The Microsoft bug bounty program just got a big update — and even applies to third-party codeNews Microsoft is expanding its bug bounty program to cover all of its products, even those that haven't previously been covered by a bounty before and even third-party code.
-
 Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updated
Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updatedNews CVE data is vital in combating emerging threats, yet inaccurate ratings and lengthy wait times are placing enterprises at risk
-
 IBM AIX users urged to patch immediately as researchers sound alarm on critical flaws
IBM AIX users urged to patch immediately as researchers sound alarm on critical flawsNews Network administrators should patch the four IBM AIX flaws as soon as possible
-
 Laid off Intel engineer accused of stealing 18,000 files on the way out
Laid off Intel engineer accused of stealing 18,000 files on the way outNews Intel wants the files back, so it's filed a lawsuit claiming $250,000 in damages
